Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×With Active Directory Domain Services (AD DS), network administrators and users have access to directory data. In AD DS, for instance, a user's name, password, phone number, and so on, is stored and enabled for other authorized users on the same network to access. Active Directory stores information about network objects and makes it easy to find and use this information for administrators and users. Based on a hierarchical, logical structure, Active Directory organizes directory information by using a structured data store.
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, Azure AD, OpenLDAP, Google, AWS Cognito etc), Identity Providers (like Okta, Shibboleth, Ping, OneLogin, KeyCloak), Databases (like MySQL, Maria DB, PostgreSQL) and many more.
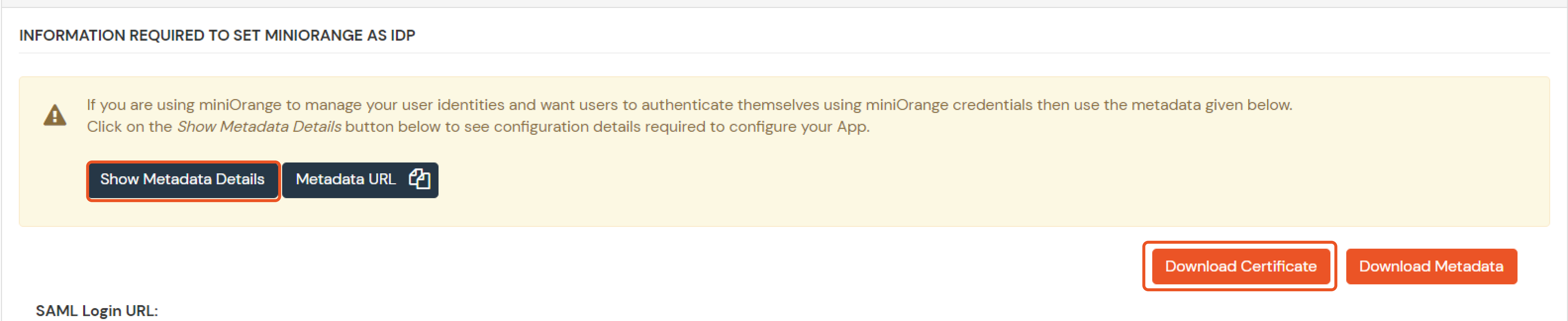
Given below are the steps to configure AD as User Store connect it with miniorange broker to single sign-on into using SAML protocol.
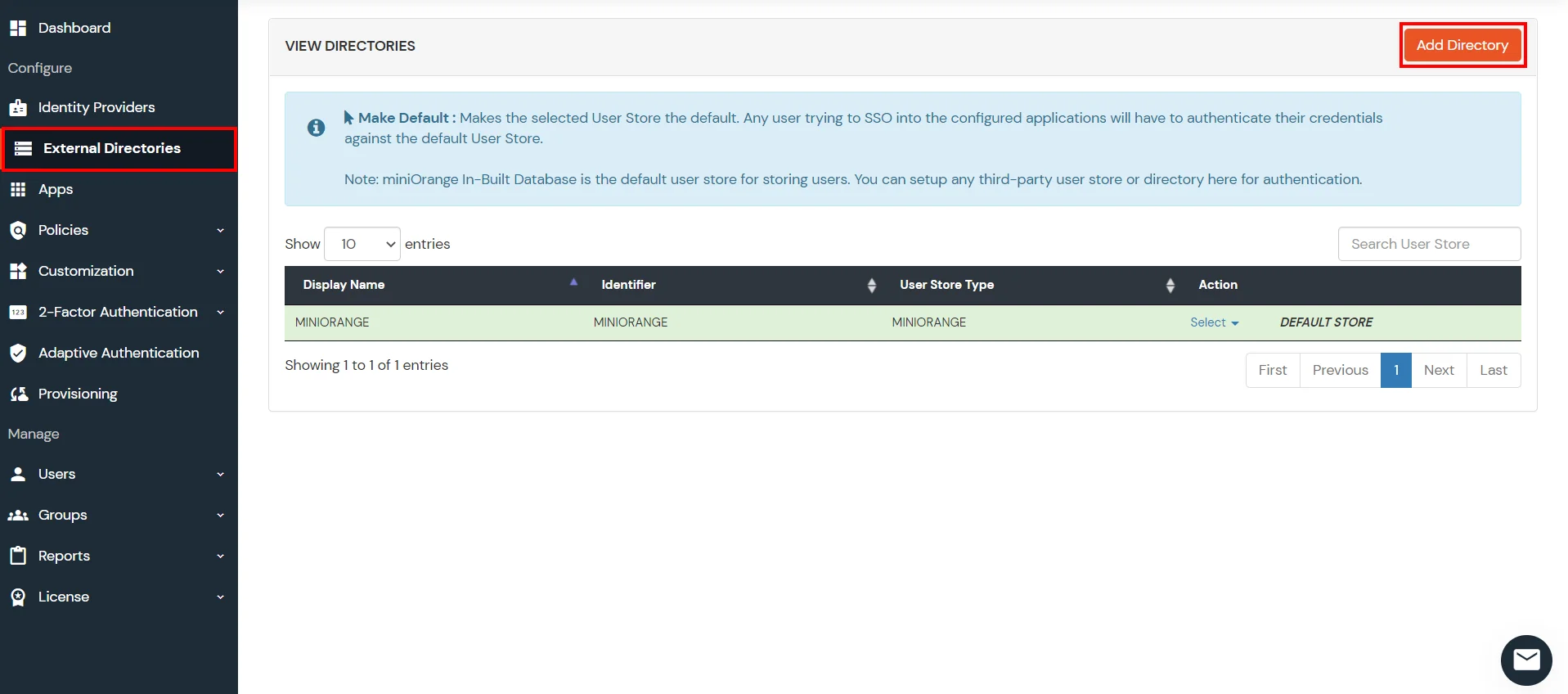
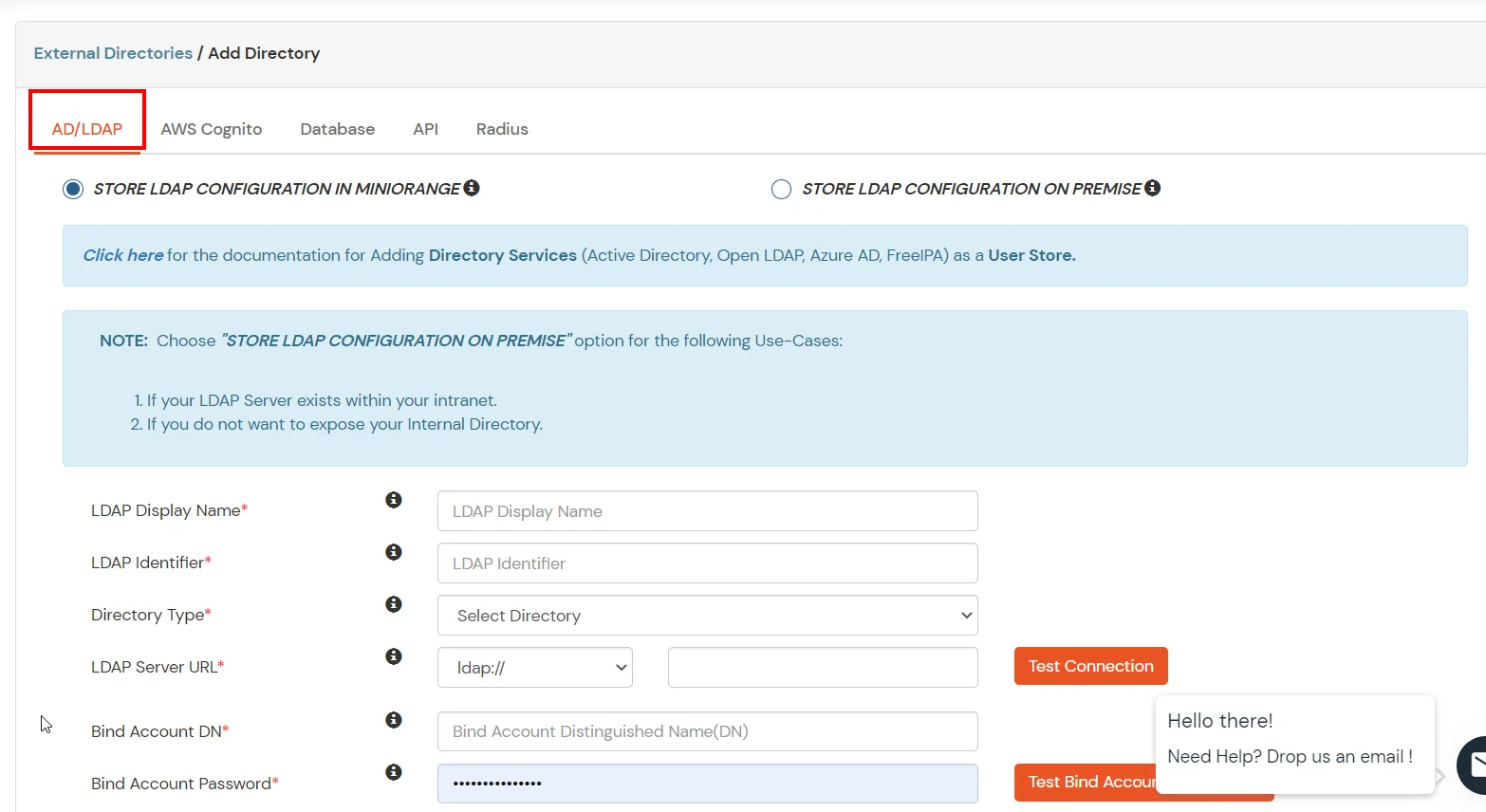
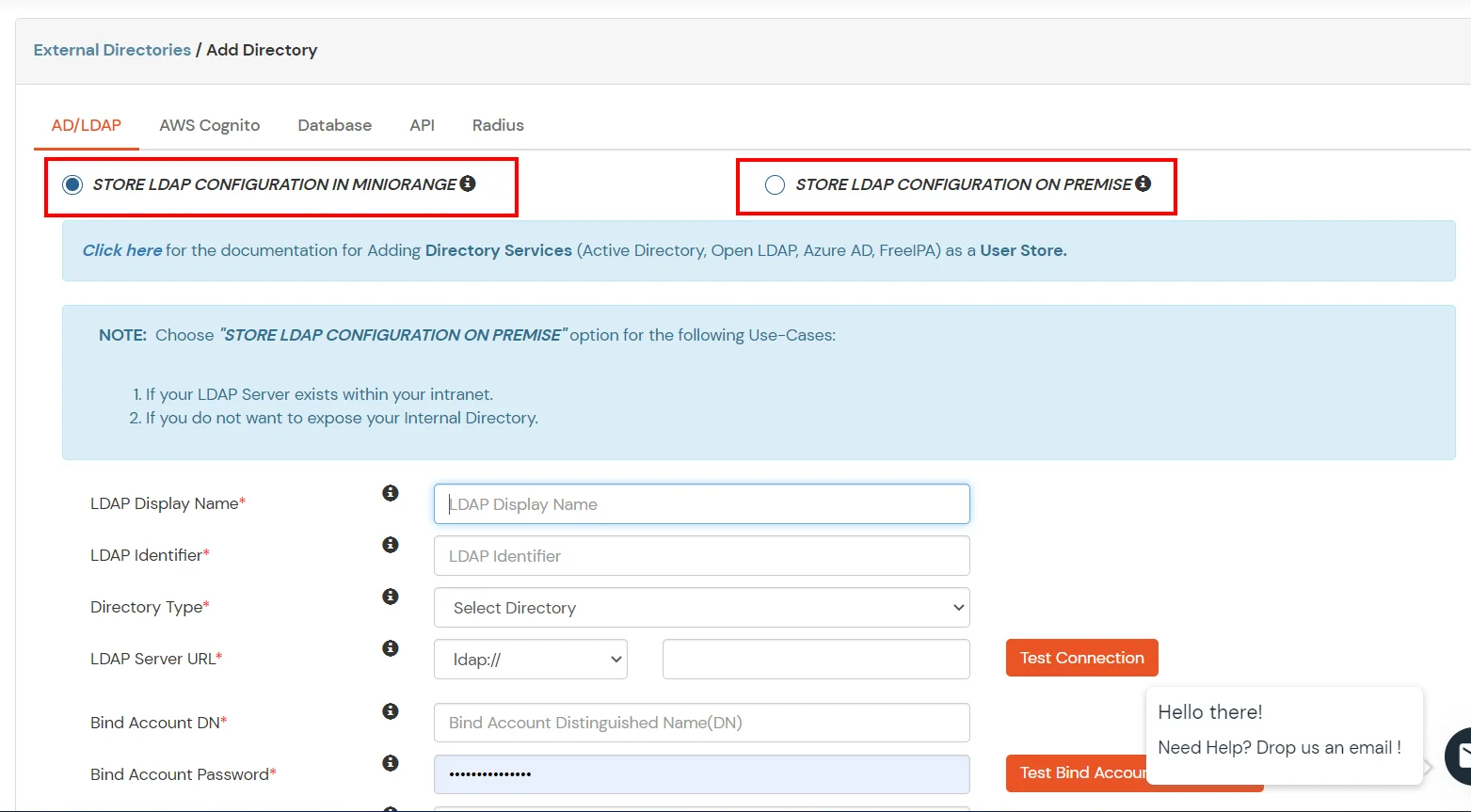
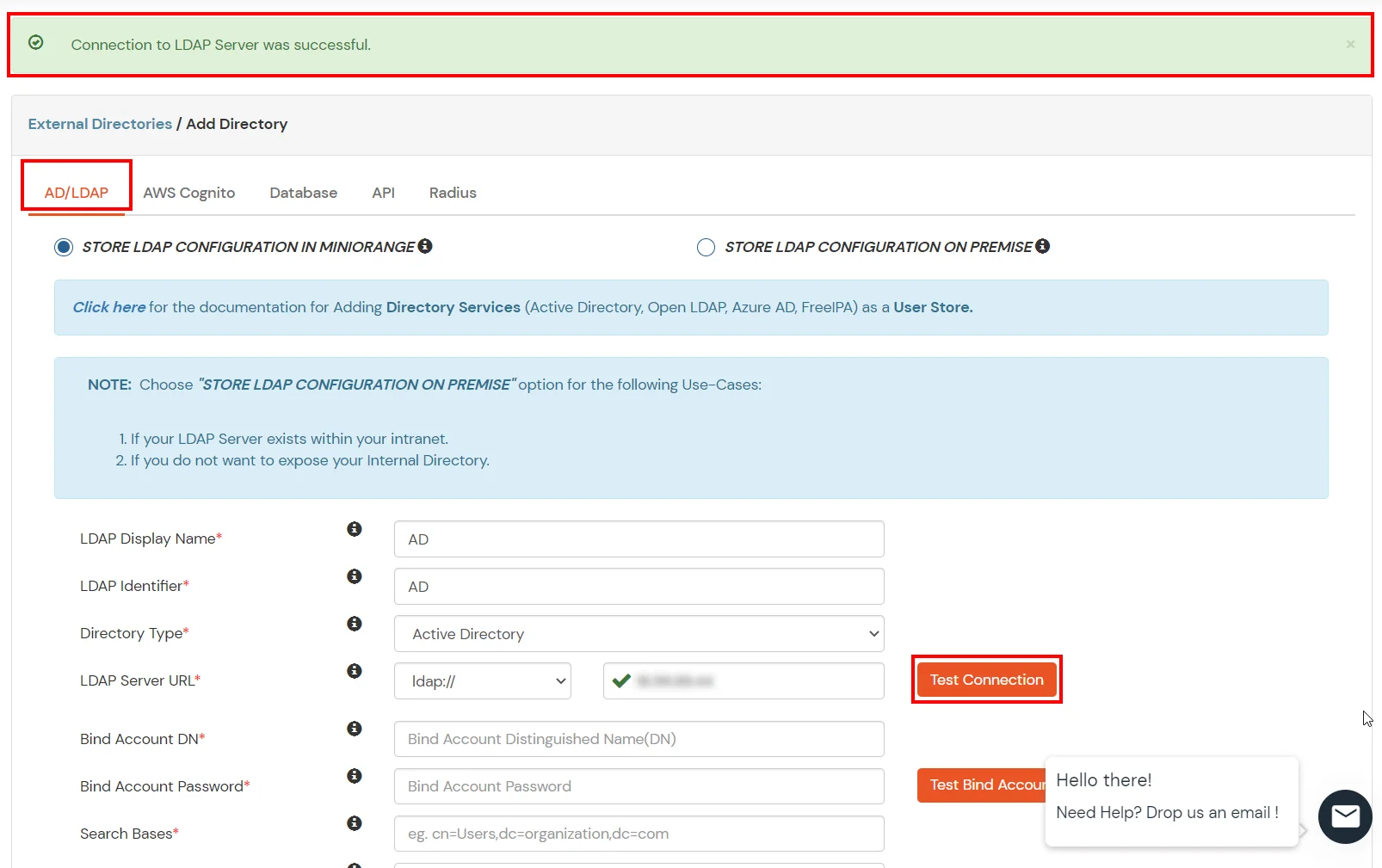
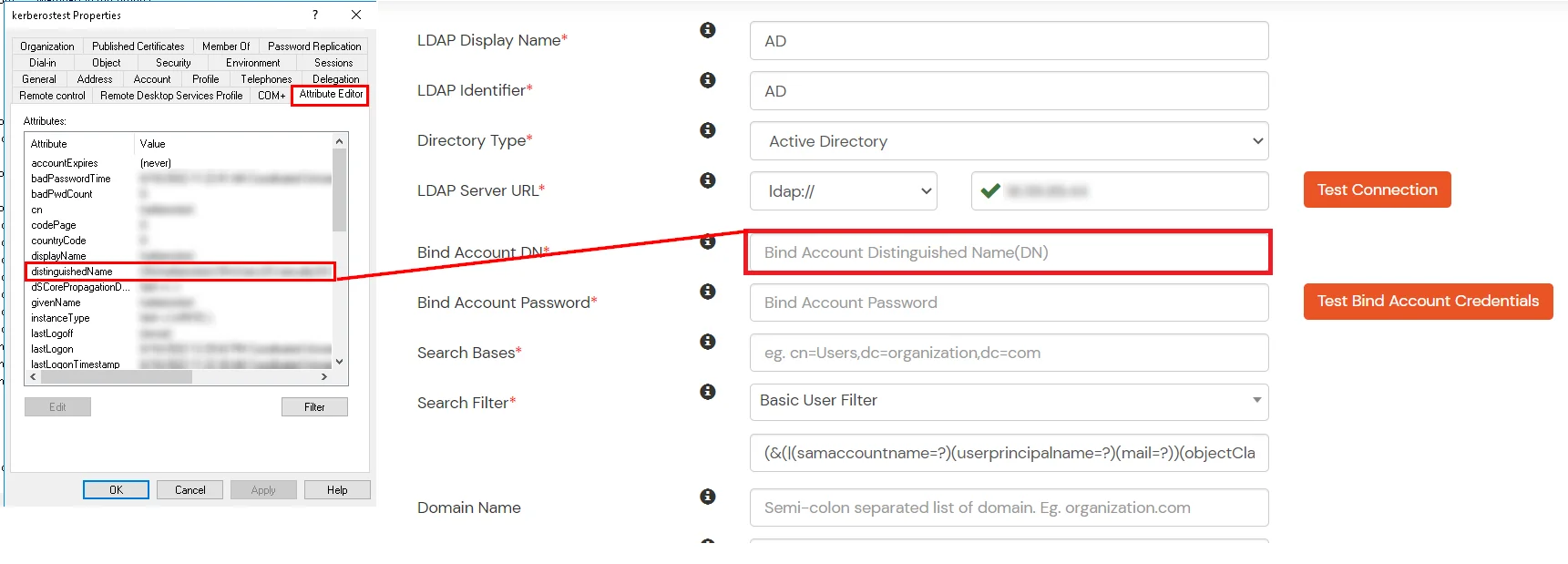
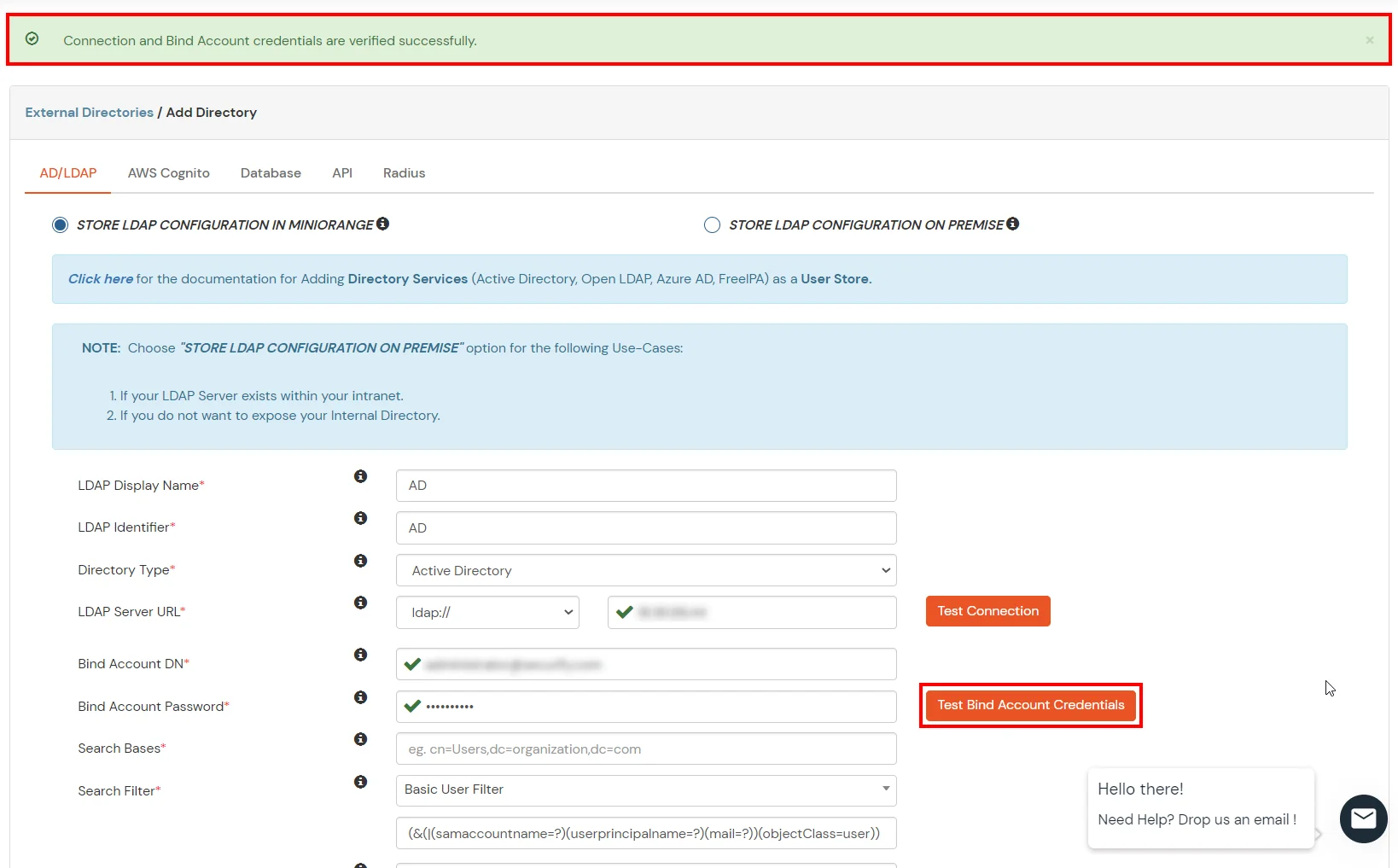
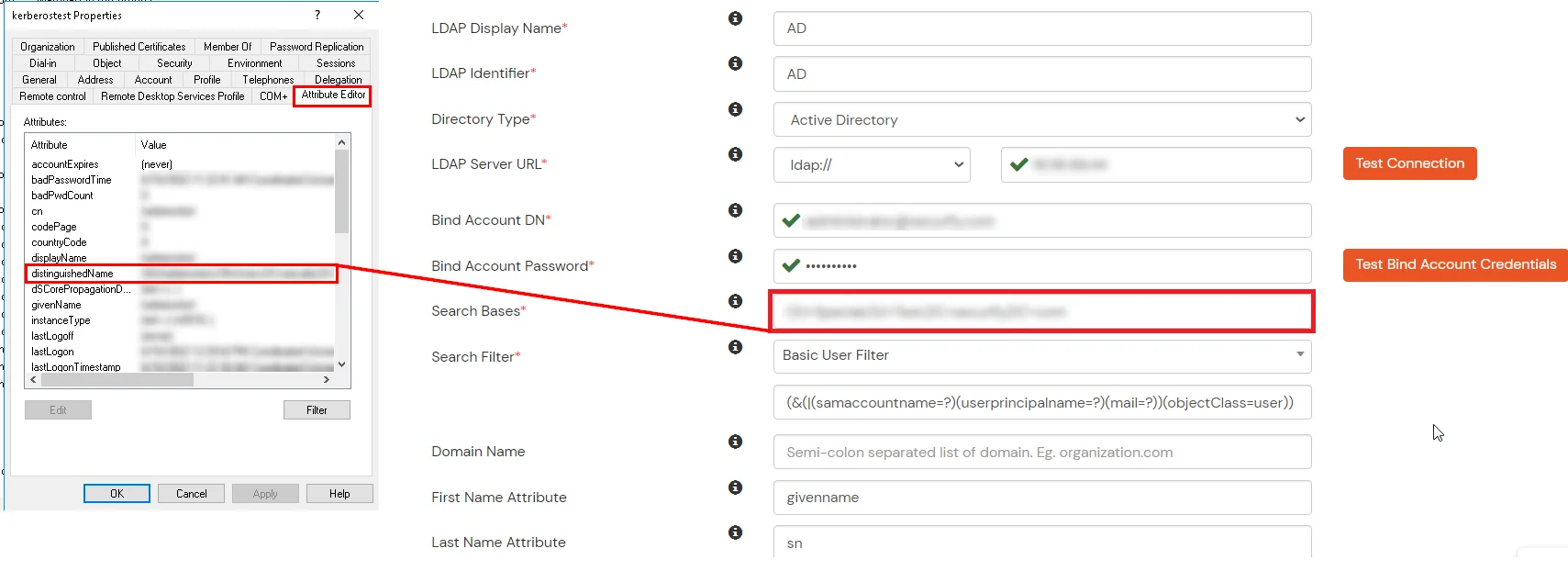
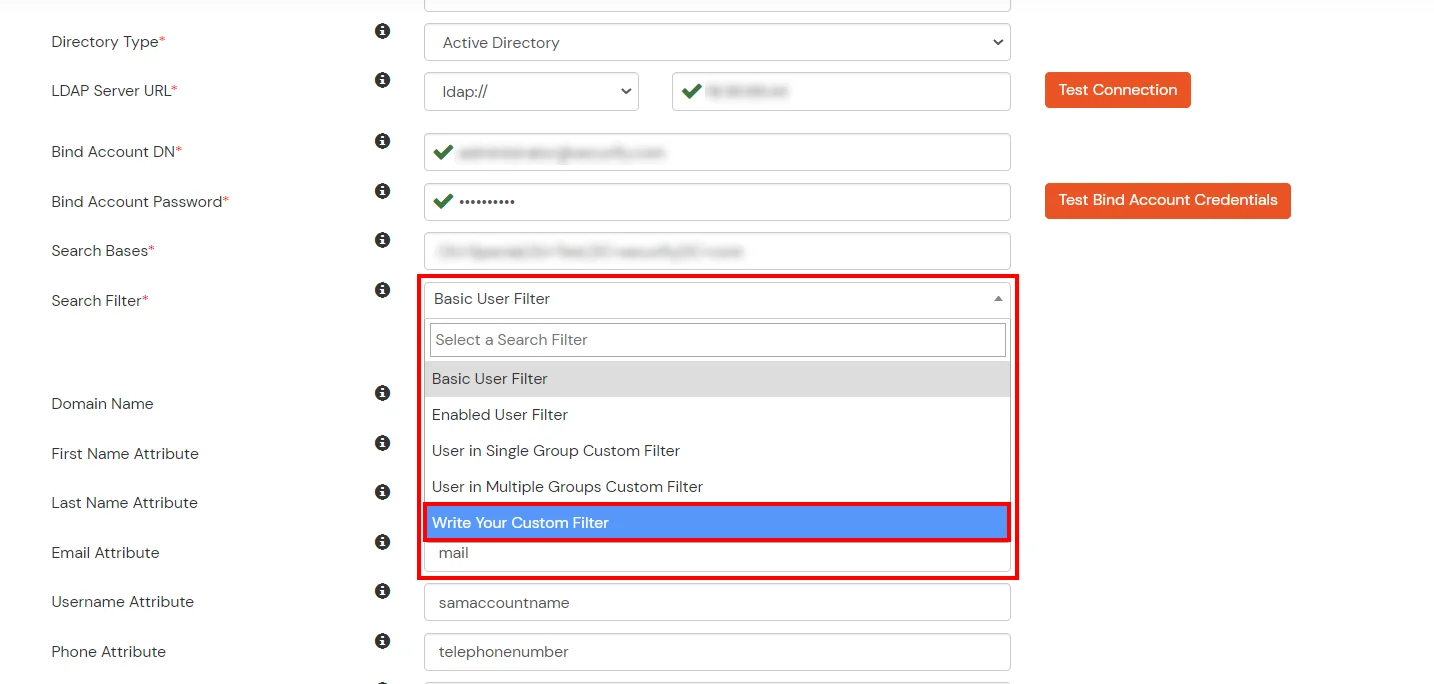
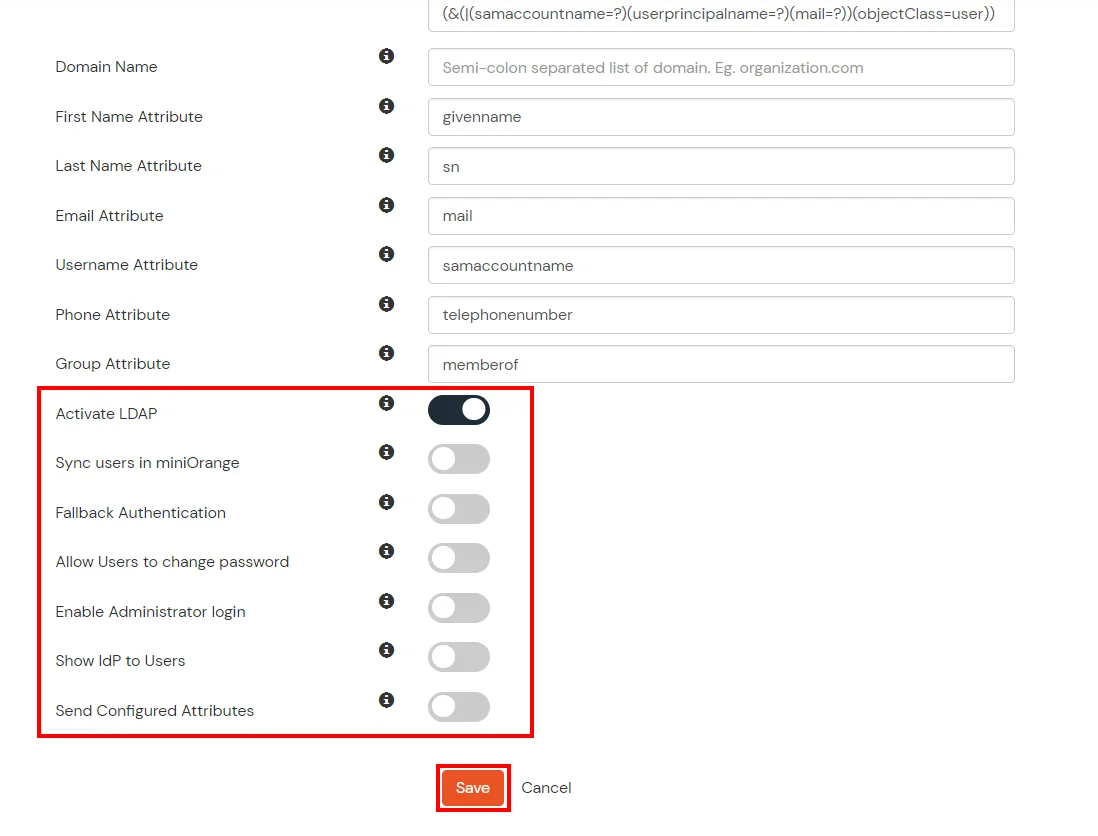
Here's the list of the attributes and what it does when we enable it. You can enable/disable accordingly.
| Attribute | Description |
|---|---|
| Activate LDAP | All user authentications will be done with LDAP credentials if you Activate it |
| Sync users in miniOrange | Users will be created in miniOrange after authentication with LDAP |
| Fallback Authentication | If LDAP credentials fail then user will be authenticated through miniOrange |
| Allow users to change password | This allows your users to change their password. It updates the new credentials in your LDAP server |
| Enable administrator login | On enabling this, your miniOrange Administrator login authenticates using your LDAP server |
| Show IdP to users | If you enable this option, this IdP will be visible to users |
| Send Configured Attributes | If you enable this option, then only the attributes configured below will be sent in attributes at the time of login |
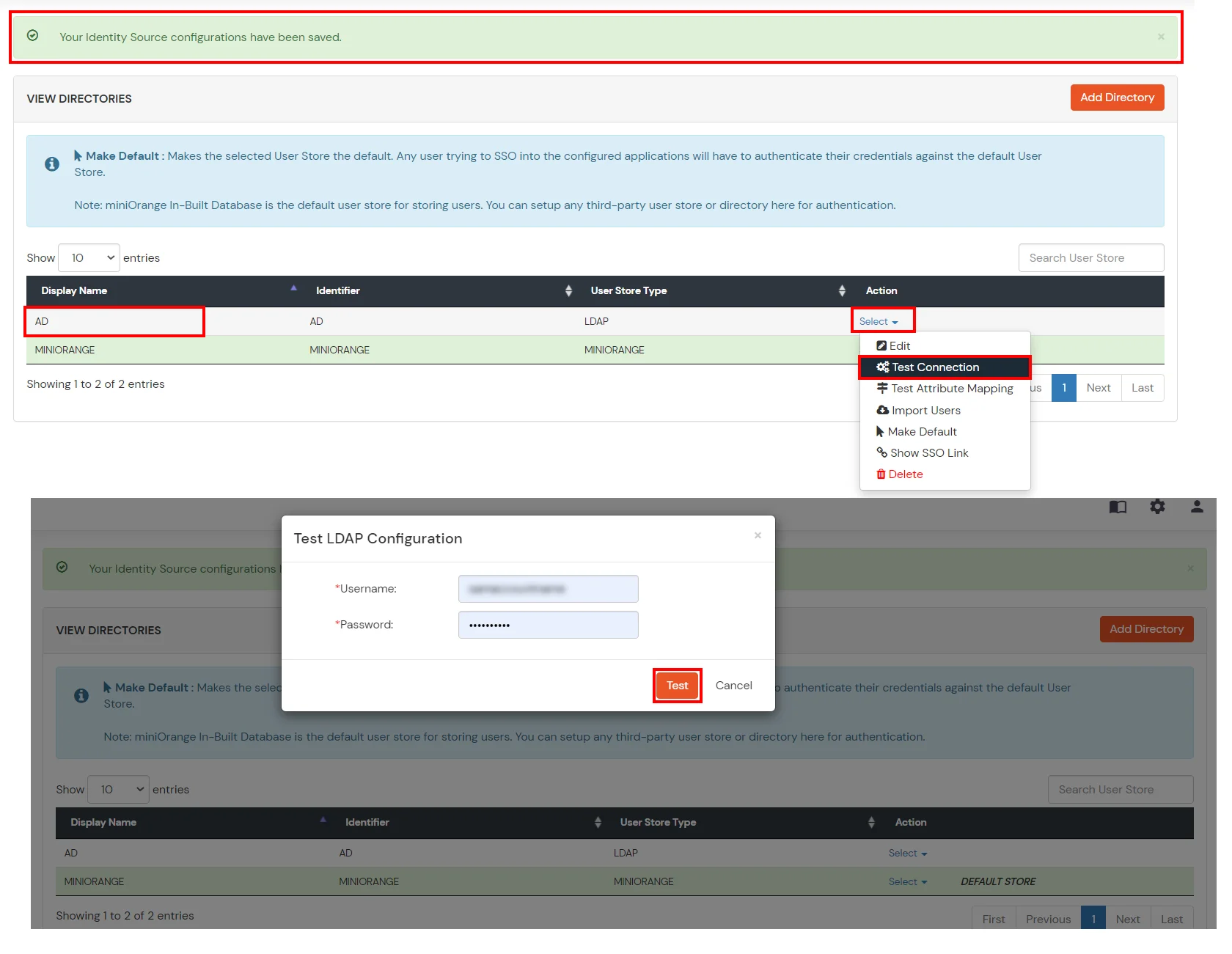
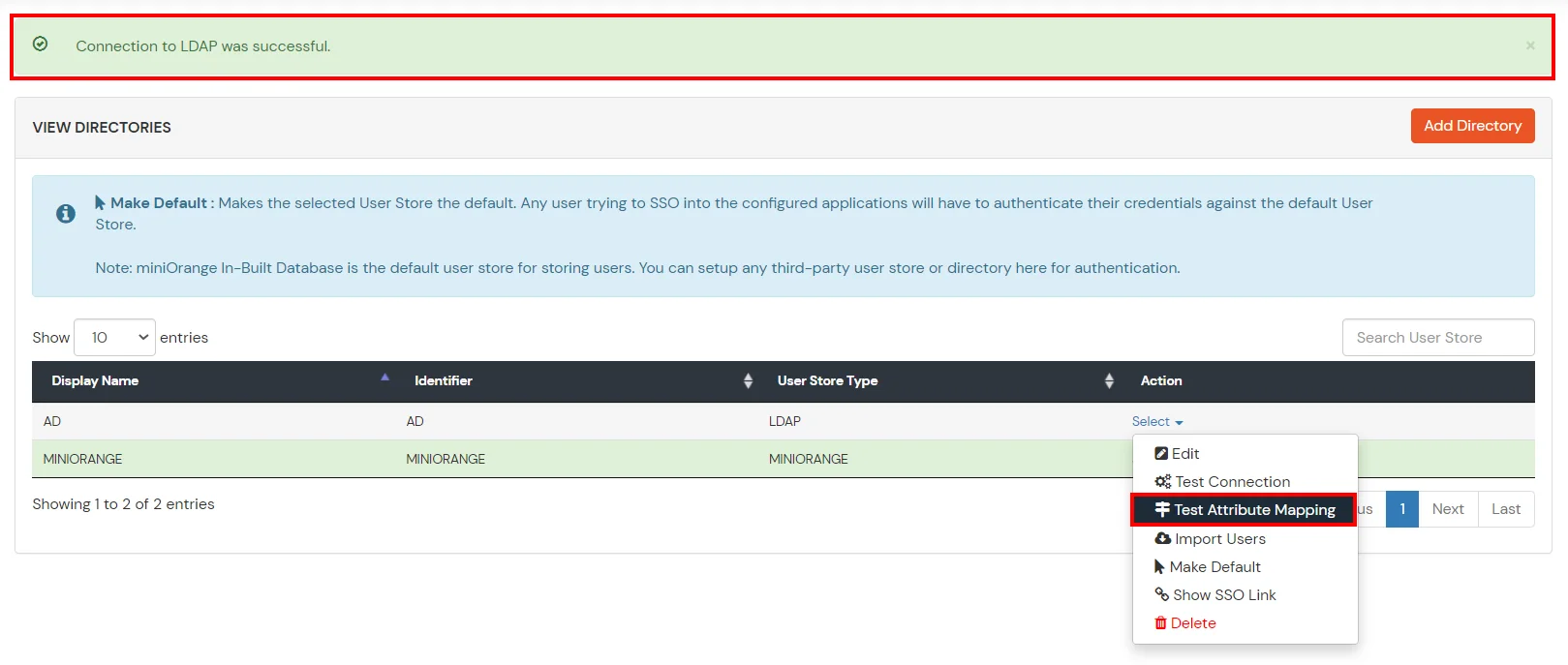
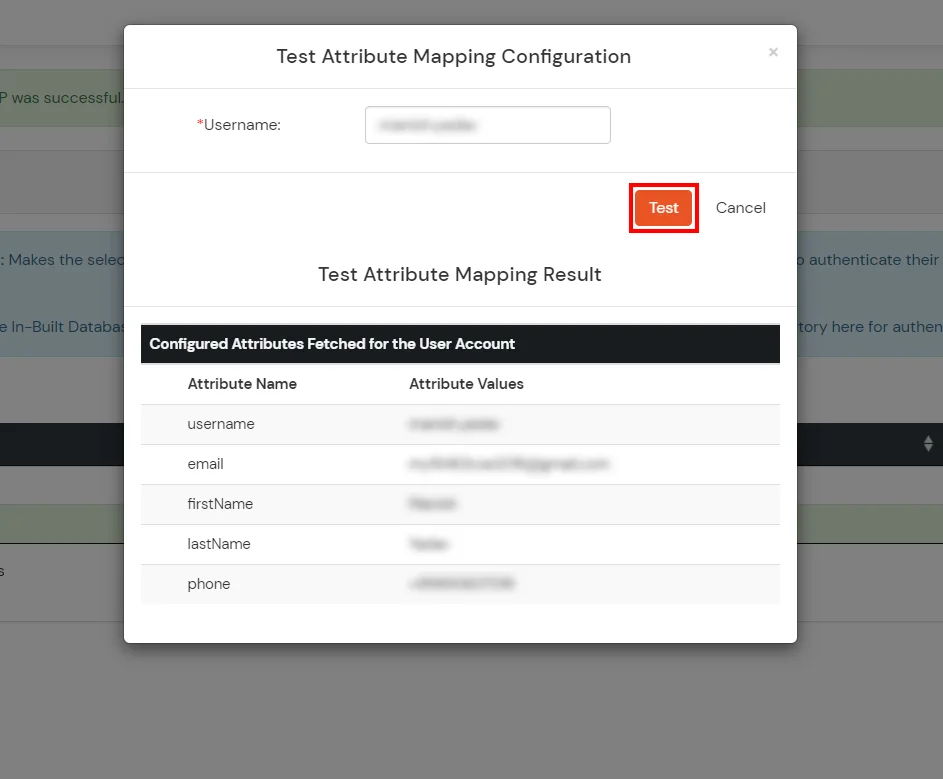
Refer our guide to setup LDAP on windows server.
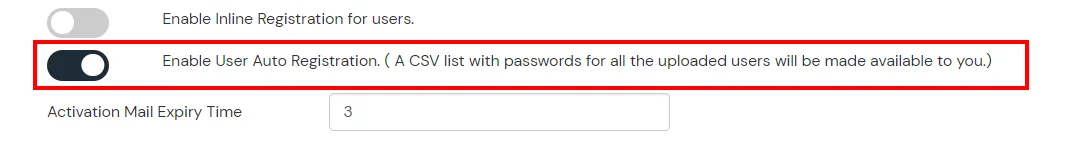
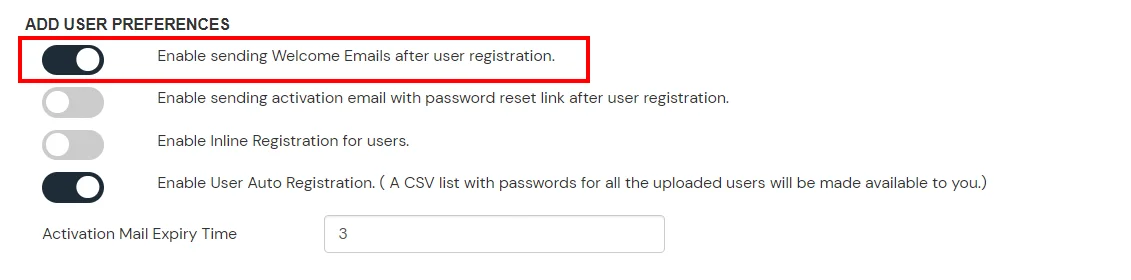
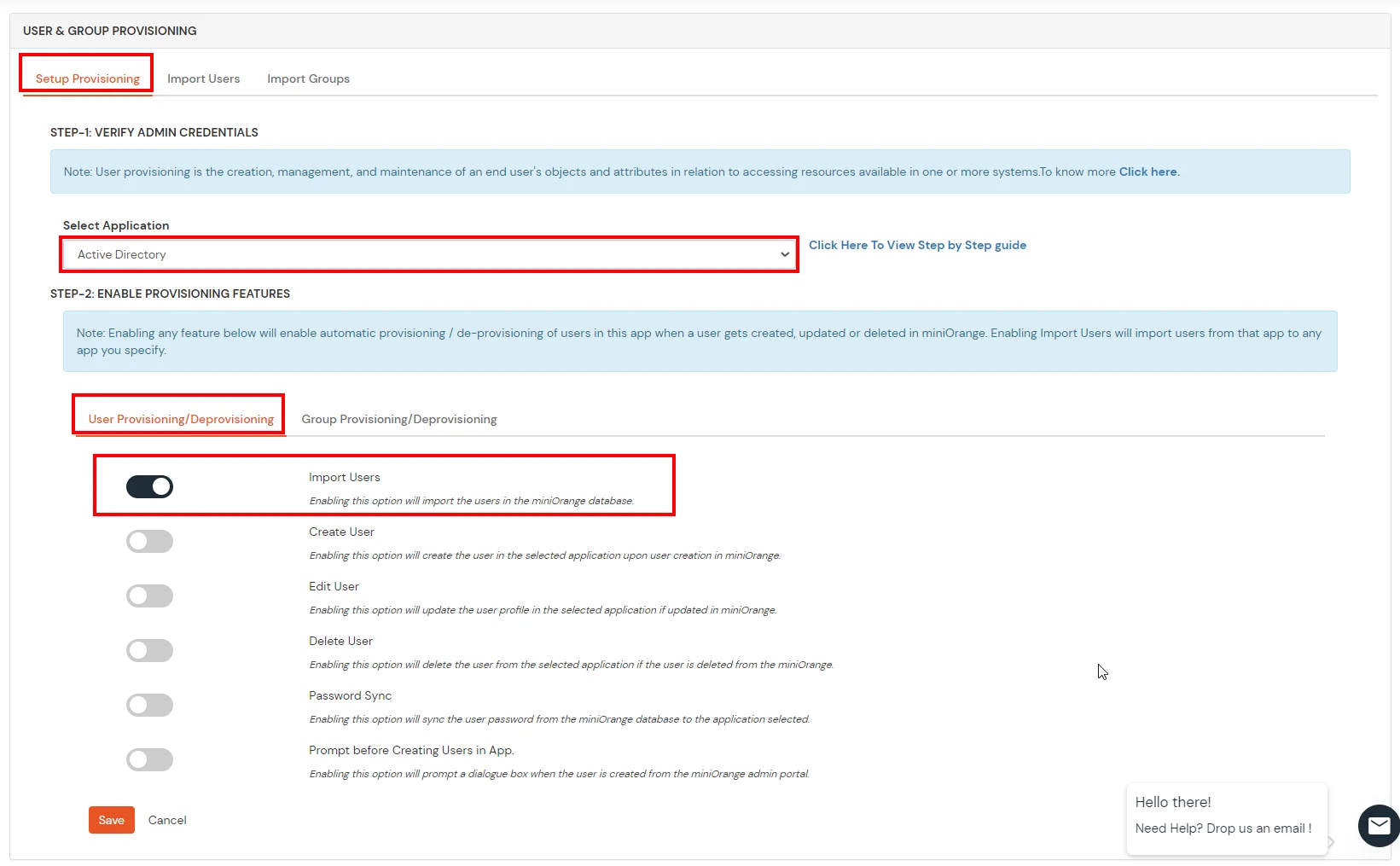
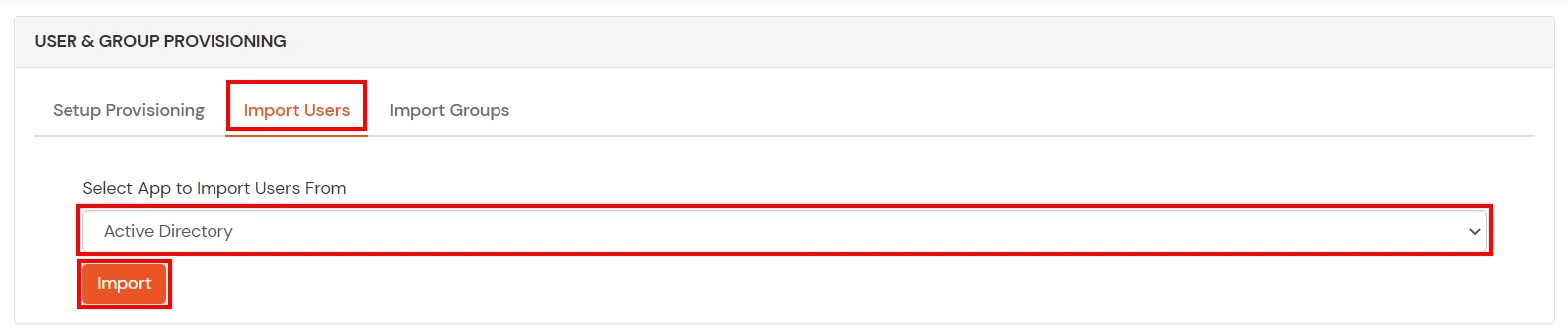
If you have already configured your application in miniOrange you can skip the following steps.
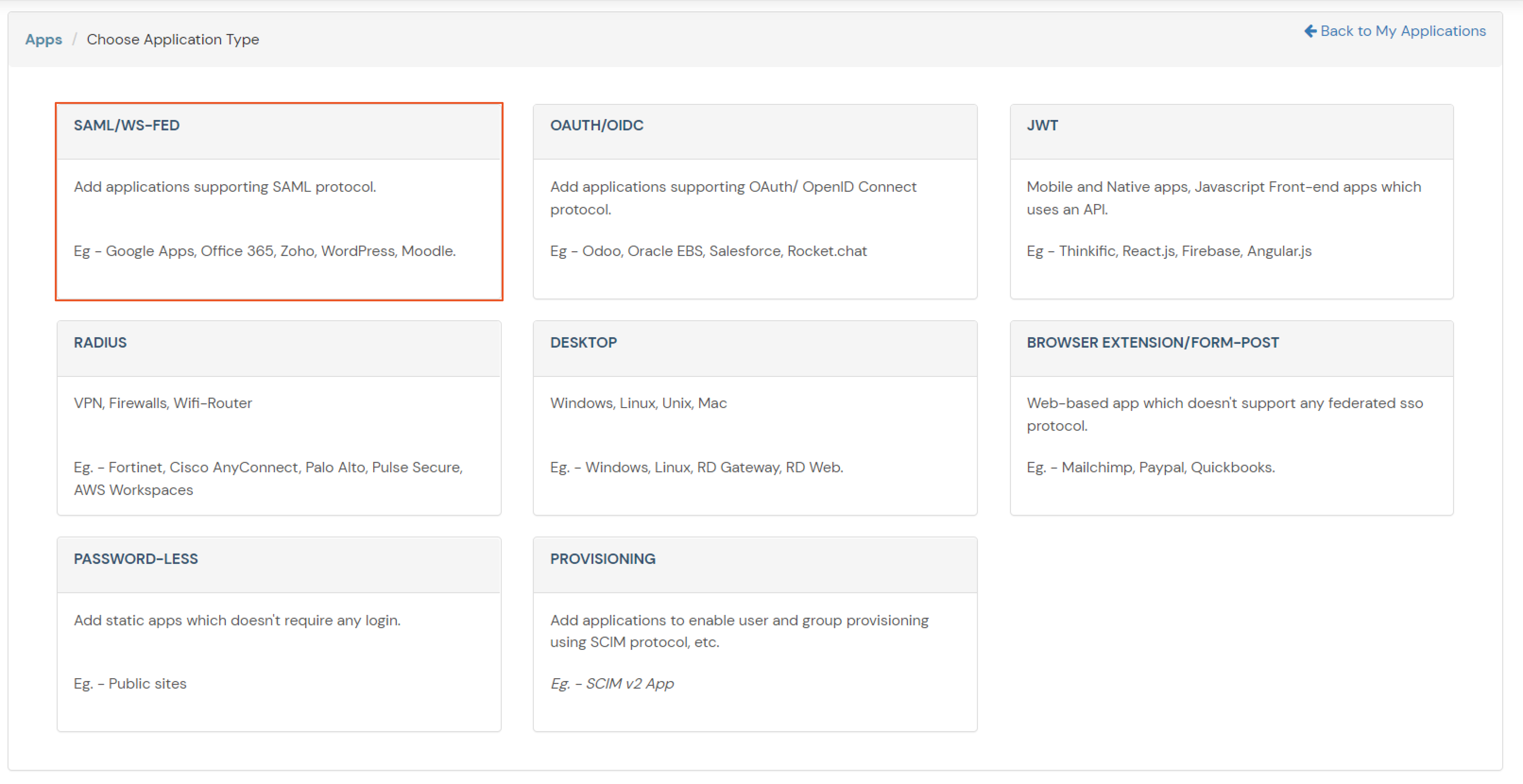
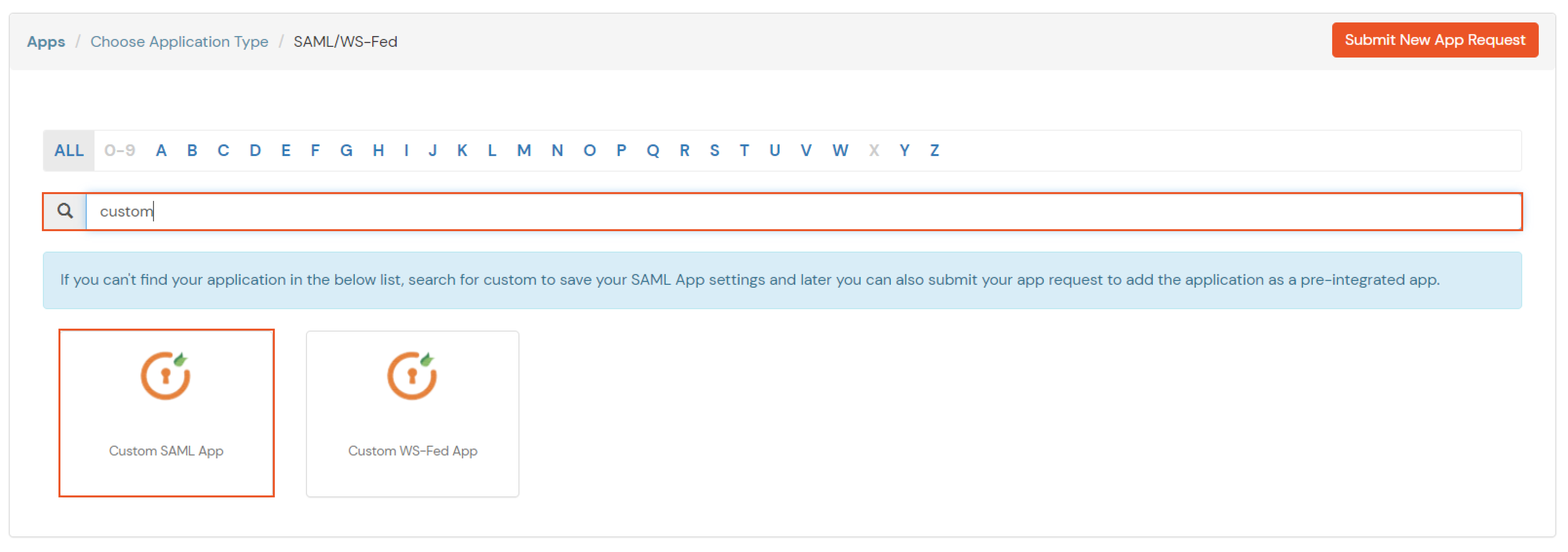
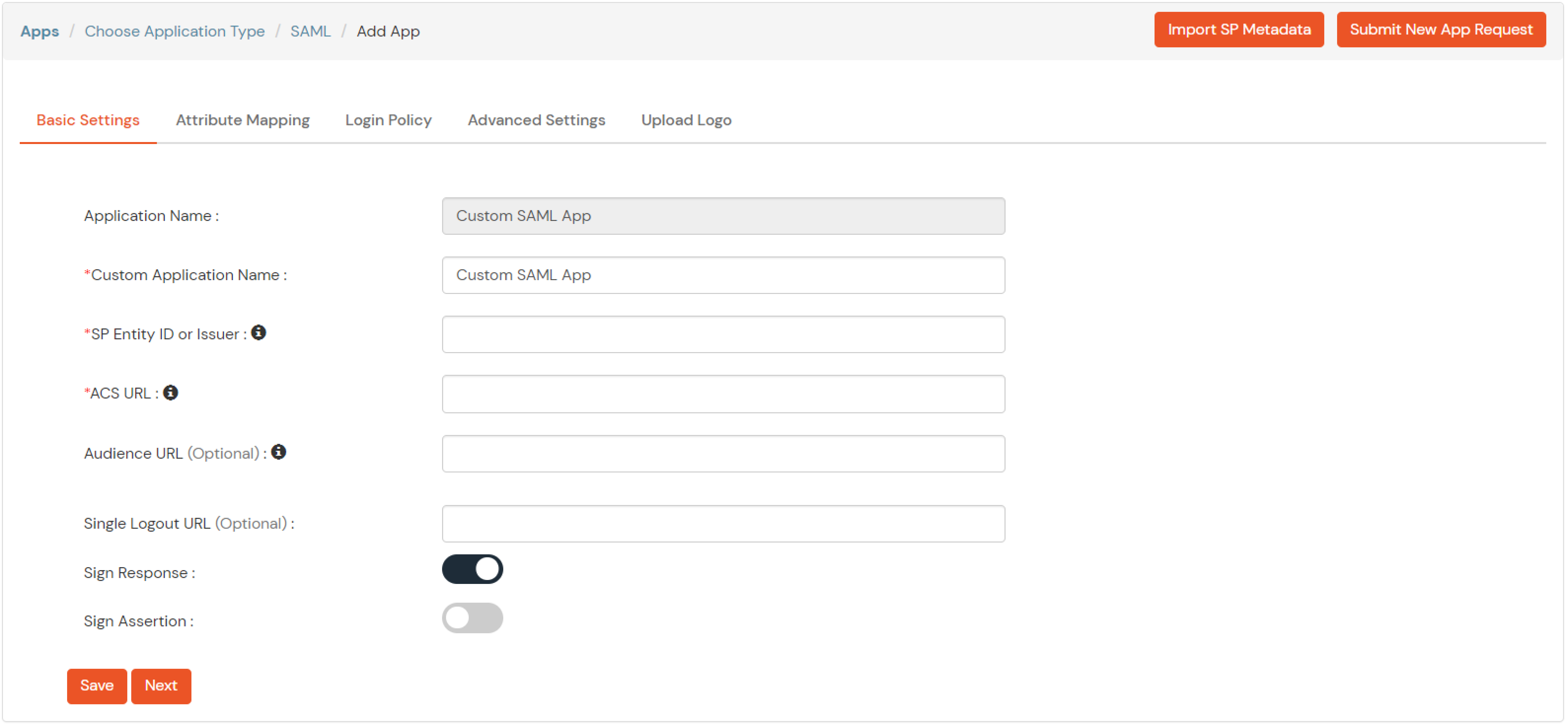
| Service Provider Name | Choose appropriate name according to your choice |
| SP Entity ID or Issuer | Your Application Entity ID |
| ACS URL X.509 Certificate (optional) | Your Application Assertion Consumer Service URL |
| NameID format | Select urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress |
| Response Signed | Unchecked |
| Assertion Signed | Checked |
| Encrypted Assertion | Unchecked |
| Group policy | Default |
| Login Method | Password |
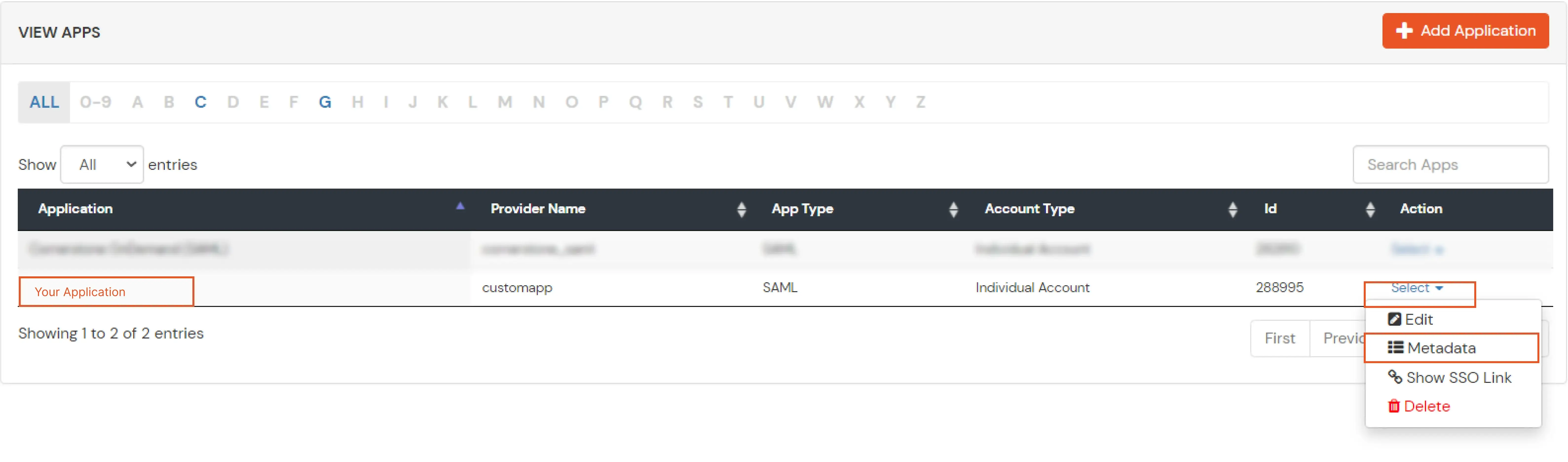
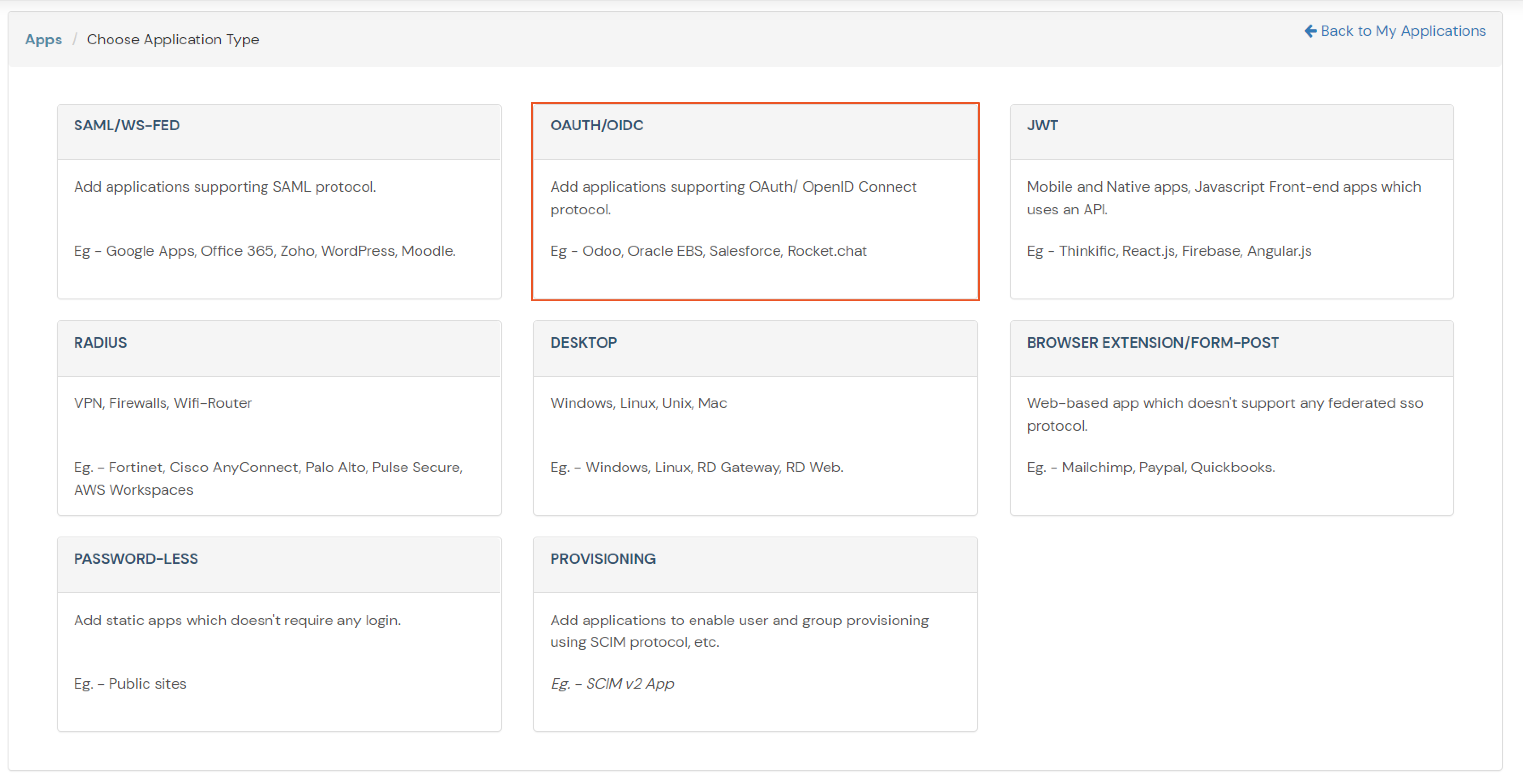

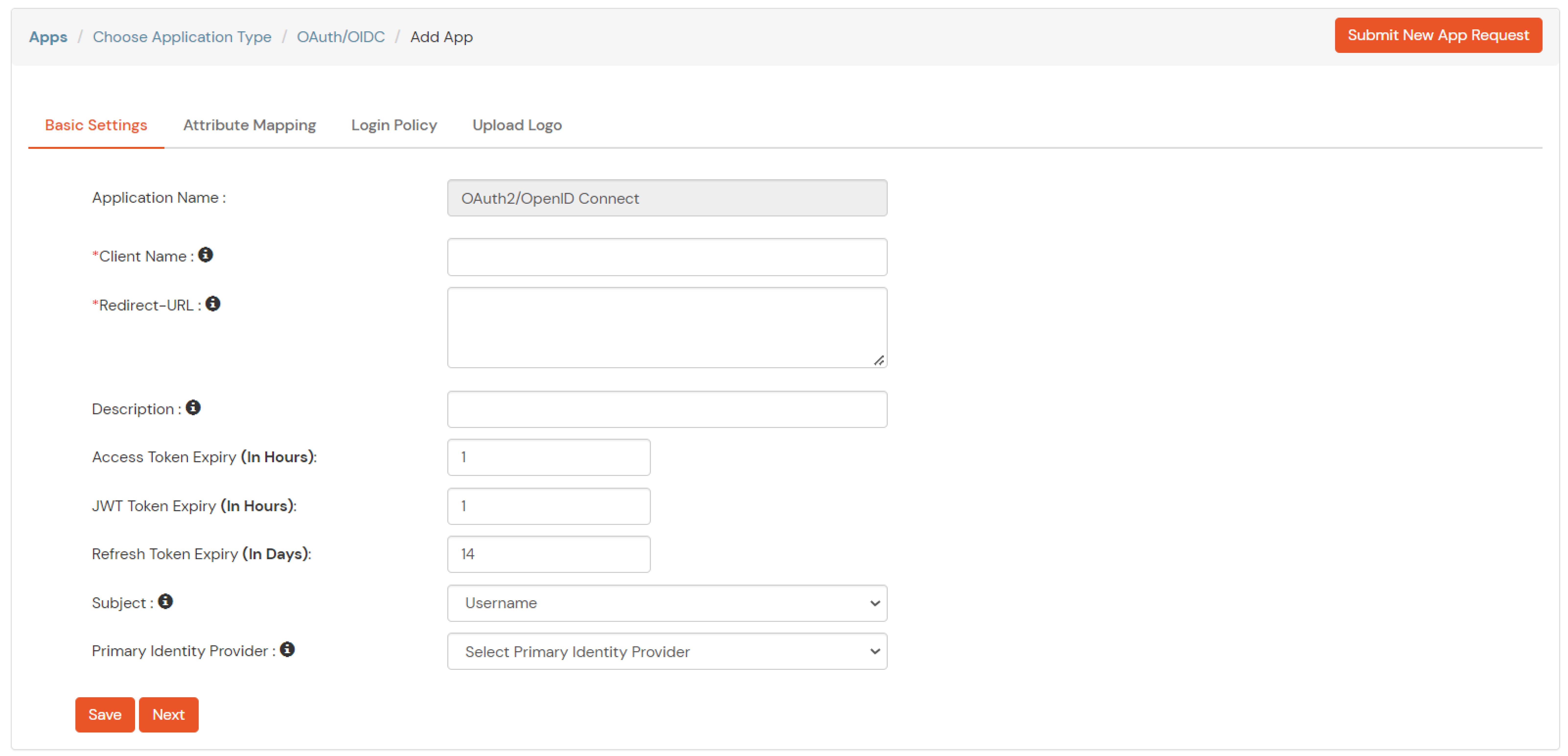
| Client Name | Add appropriate Name |
| Redirect URL | Get the Redirect-URL from your OAuth Client |
| Description | Add if required |
| Group Name | Default |
| Policy Name | As per your Choice |
| Login Method | Password |
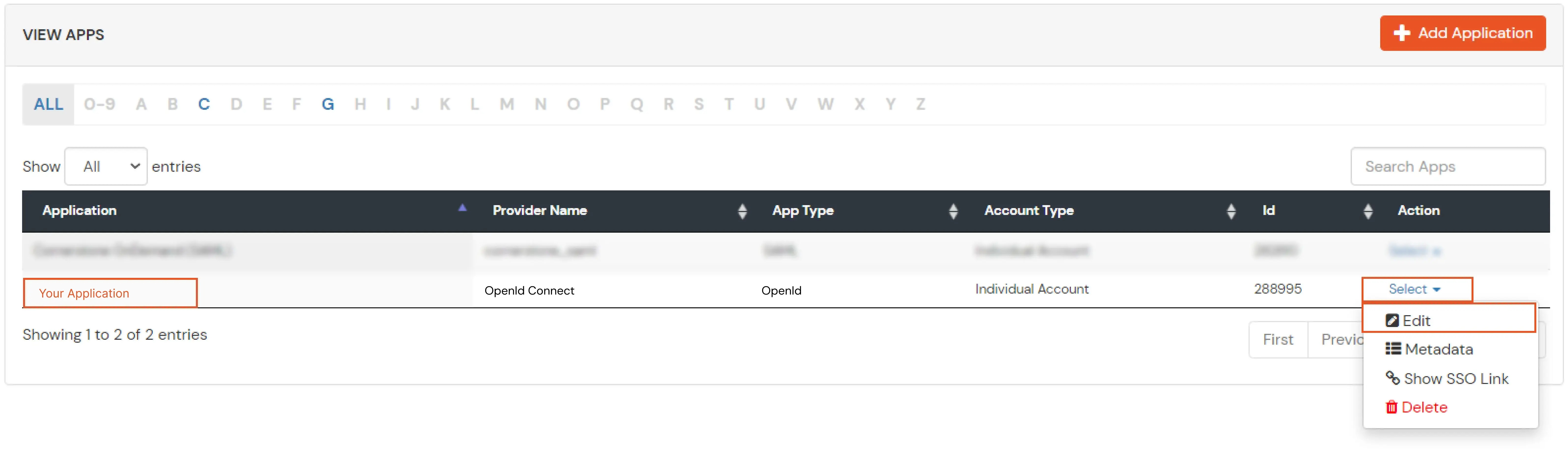
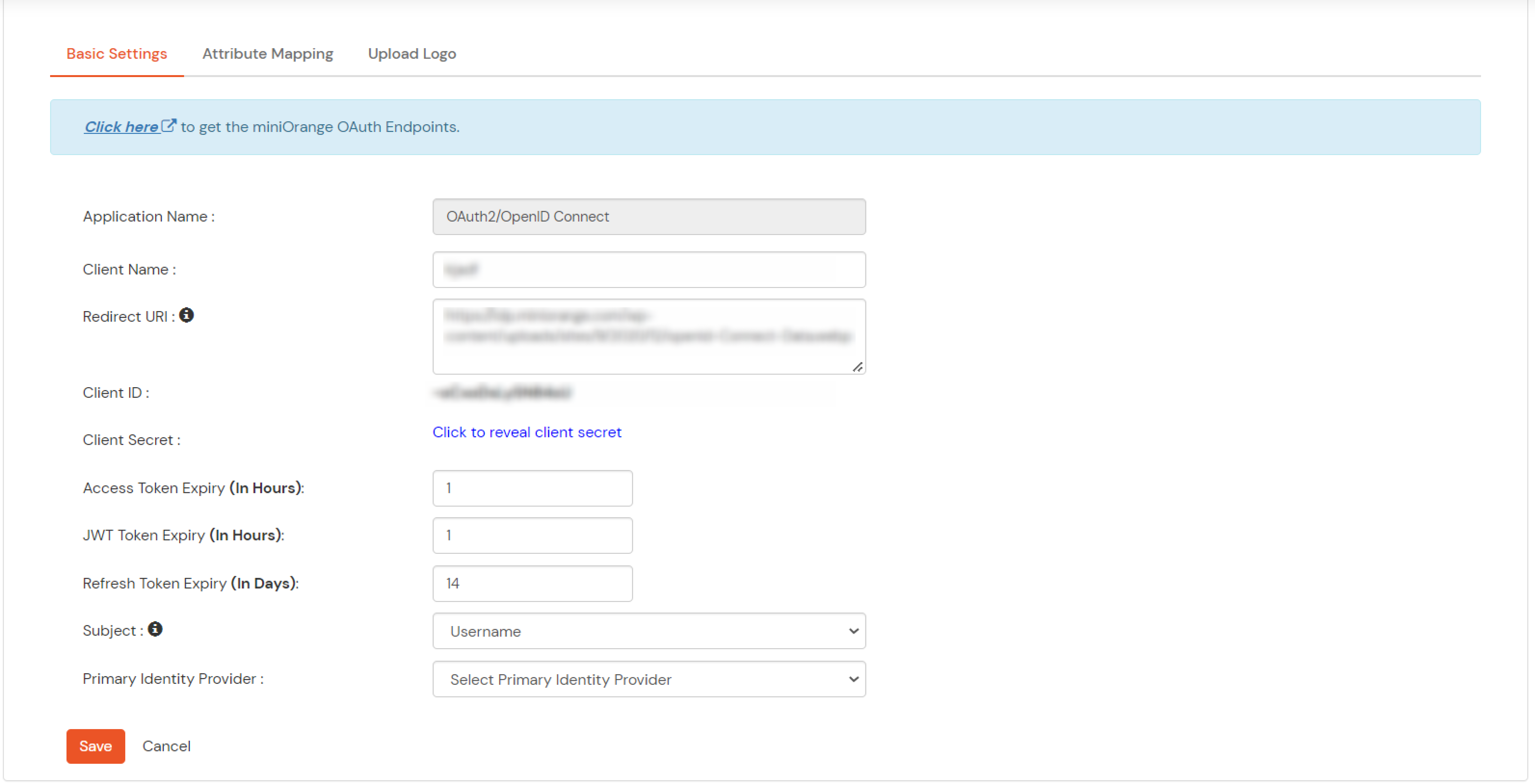
Note: Choose the Authorization Endpoint according to the identity source you configure.
https://{mycompany.domainname.com}/moas/idp/openidssohttps://{mycompany.domainname.com}/broker/login/oauth{customerid}
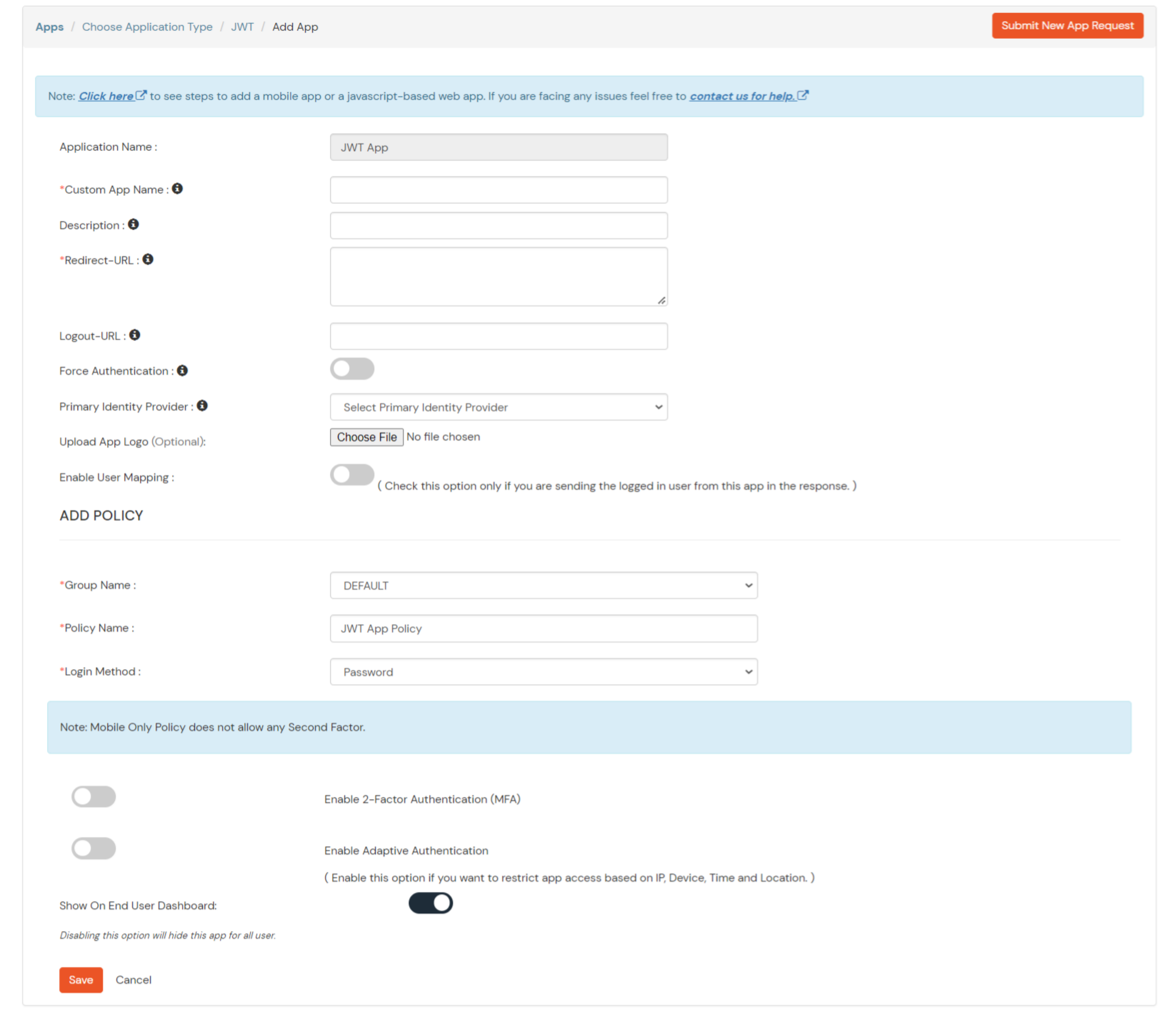
In case you are setting up SSO with Mobile Applications where you can't create an endpoint for Redirect or Callback URL, use below URL.
https://login.xecurify.com/moas/jwt/mobile

Our Other Identity & Access Management Products