Need Help? We are right here!
Search Results:
×
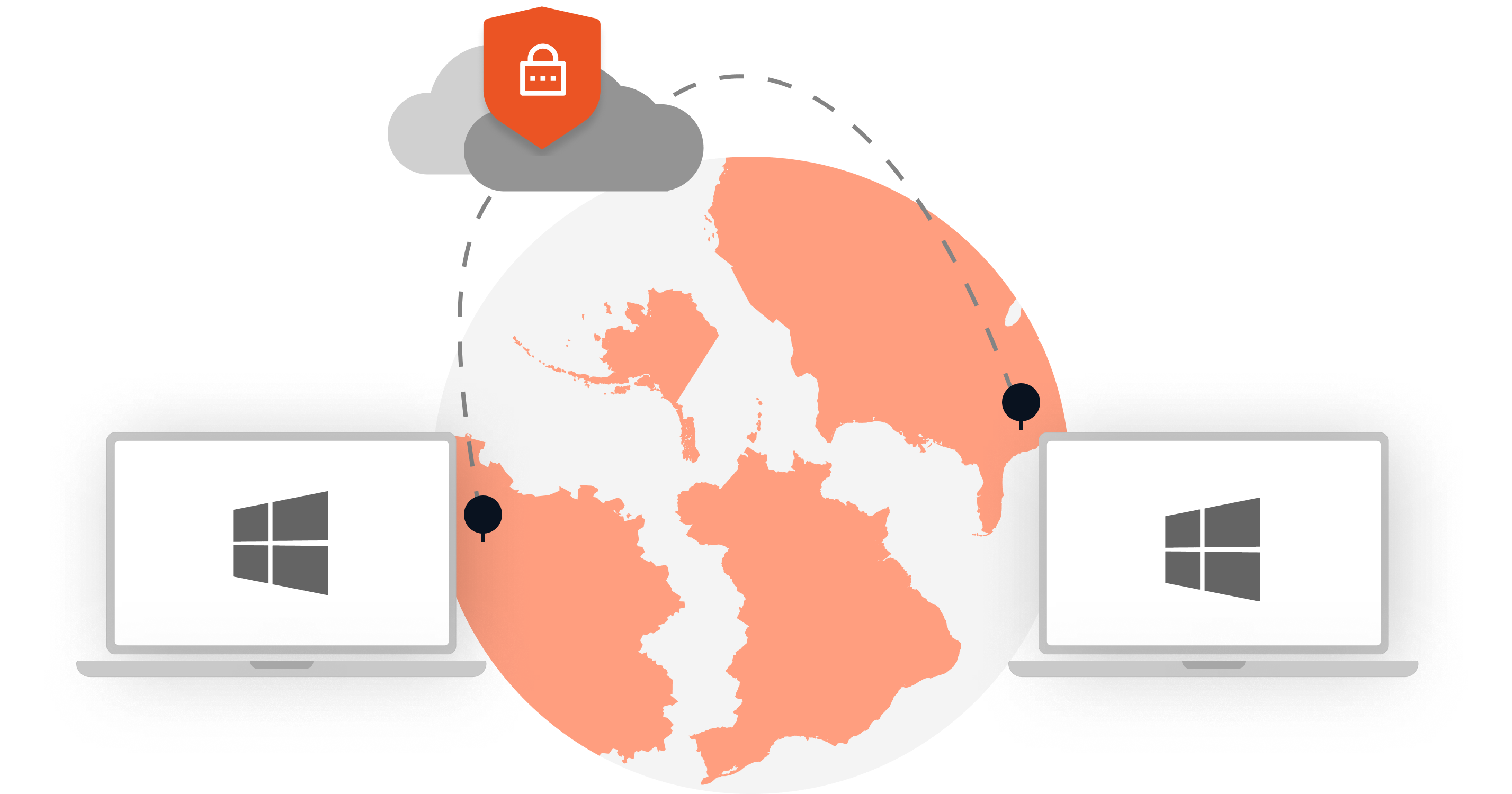
Remote Desktop Services allows users to securely access Windows systems remotely over a network connection. Remote Desktop Protocol (RDP), Remote Desktop Gateway (RD Gateway), Remote Desktop Web Access, or Web client (RD Web Access/RD Web Client) are part of the Remote Desktop Services that modern workforces are using to remotely access enterprise systems.
But if the credentials (username and password) for Remote Desktop login are leaked, then hackers can easily gain access, resulting in data breaches. Hence, organizations require robust security mechanisms like Multi-Factor Authentication (MFA) on Remote Desktop logon to safeguard Remote Desktop access.
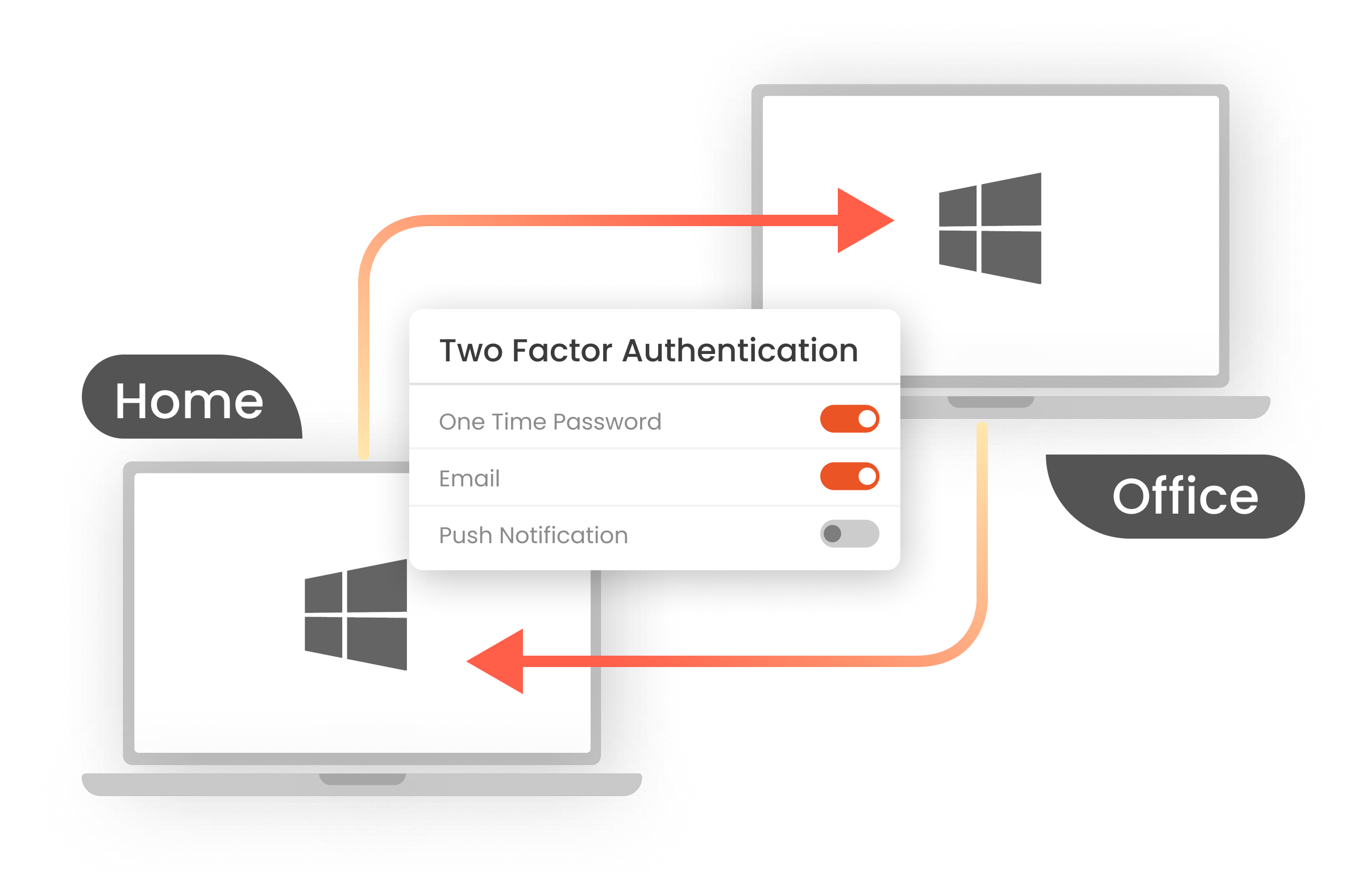
MFA adds an extra layer of security on Remote Desktop connections and prompts a second factor or 2FA/MFA challenge after the user completes the first level of authentication using their credentials. Hence, even if a hacker logs in with a stolen password, they won’t be able to fulfill the 2FA challenge (e.g., Push notification on the user's phone). This way the enterprise systems and sensitive data are secured.
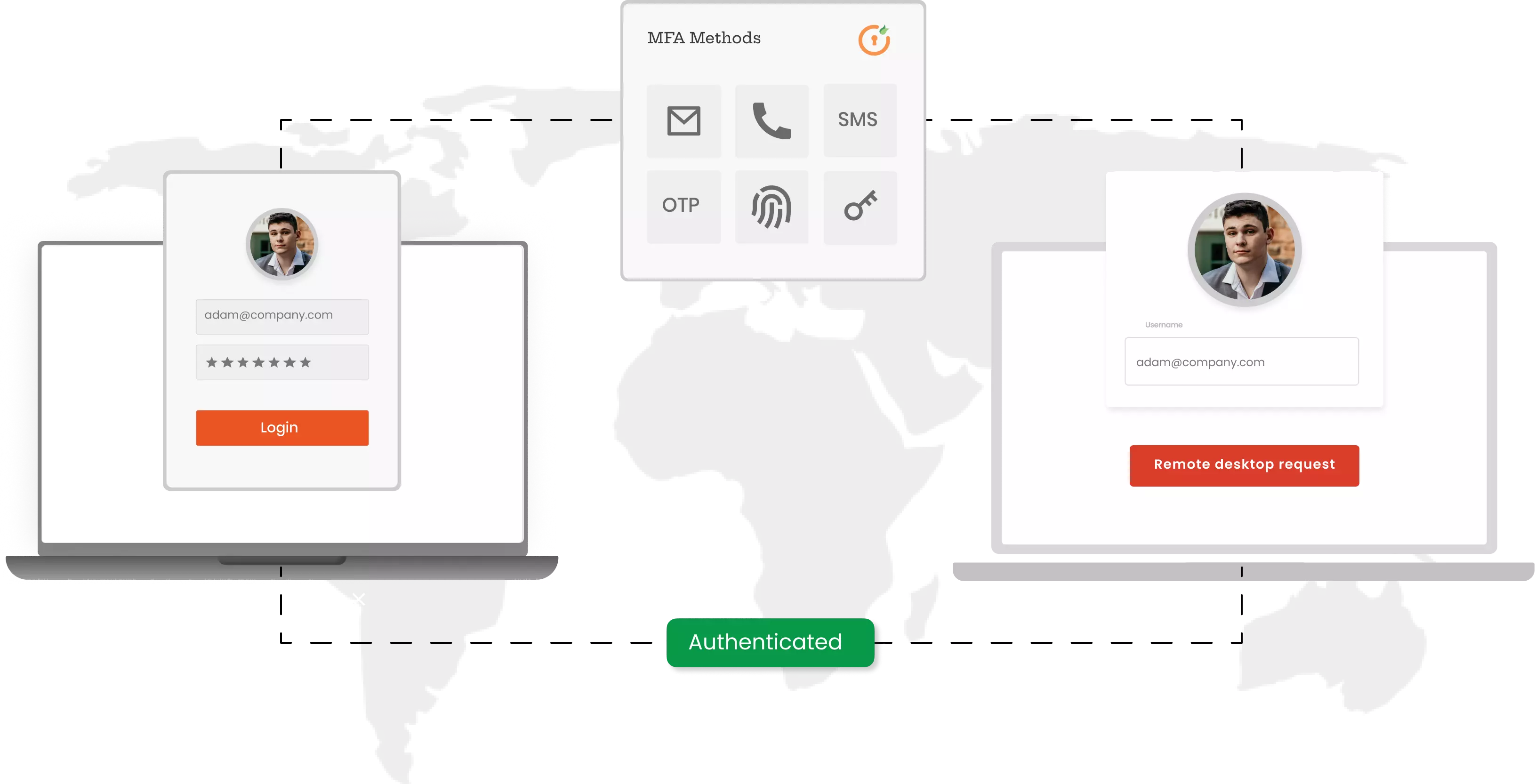
miniOrange provides 15+ 2FA/MFA methods like OTP over SMS/Email, Push Notification, Hardware Tokens, etc. This will ensure that your sensitive data is protected and will help you comply with International Regulations and Cyber Insurance Policy compliance as well.
You might be using Remote Desktop Protocol or RDP to remotely access and manage servers, workstations, and infrastructure devices. But if the credentials or password of your RDP logons falls into the wrong hands, your entire corporate network could be compromised. Hence, it is necessary to implement Remote Desktop MFA for RDP connections to add an extra layer of security, blocking hackers from accessing your networks and systems.
Remote Desktop Gateway or RD Gateway is used by Organizations to allow remote users to access specific applications securely without the need for full desktop access. However, remote access via RD Gateway is also vulnerable to modern cyberattacks and hacking. To avoid compromise of RD Gateway login, Remote Desktop MFA can prove to be an effective method. The miniOrange MFA for RD Gateway is completely agentless, which means that it can be seamlessly deployed even on non-domain joined systems as well. This makes deployment faster and simpler.
**Note: miniOrange offers 2FA/MFA methods such as Push notifications and Authentication via Email/SMS link for RD Gateway.
Organizations use RD Web Access for publishing RemoteApp programs, enabling users to launch individual applications from the portal rather than full desktops. Similarly, the RD Web client does the same job, but it does it via a browser. MFA security can further secure access to RemoteApp programs hosted via RD Web Access and Web Client. Enable MFA for all HTML5-based Remote Desktop web client logins.
Offline MFA enables seamless user access even when the authentication server or internet is down. This ensures that users can continue their work effectively without any disruptions.
Set Custom MFA policies like user-specific MFA access, bypassing MFA for Admin accounts and setting a time for MFA after subsequent login.
Secure your Remote Desktop Services, VPNs, and more with a Central Authentication source that also supports other IDPs like Active Directory.
Enable users to securely access different domain-joined systems within the enterprise network. Let your users log in using trusted domains like Azure AD, Active Directory, etc.
Configure different MFA methods for each machine having generic non-unique usernames such as admin, administrator, etc., in both domain-joined & non-domain-joined environments.
Reduce help-desk calls by enabling your users to reset their passwords for the first authentication factor via the self-service portal. Optimize support team costs.
Create a personalized login experience for your users by highlighting your logo on the login screen.
By using Group policies or GPO, the MFA module can be deployed at once to all your machines and systems. This makes the deployment process faster on non-domain-joined systems.
Tackle high-risk scenarios and secure all your Remote Desktop Services with miniOrange Risk-based Authentication or Adaptive MFA. This is an advanced form of MFA where you can restrict user access based on contextual factors like IP, Device, Time, and location. With custom Risk-based Authentication policies, you can either restrict access based on these contextual factors or you can configure it to prompt MFA only when the situation demands as per the policies you have set. This will improve workforce productivity and provide your organization with a smart security response.
Explore Risk-based AuthenticationSecure your Mac Devices & Mac SSH Login with miniOrange Multi-Factor Authentication (MFA) for enterprise systems using macOS Operating systems. Fulfill Cyber Insurance Compliance with ease.
The miniOrange MFA module can be installed on all servers and devices running on Linux operating systems to enable Multi-Factor Authentication (MFA). Enable MFA on SSH connection to Linux servers.
per user per month
*Please contact us to get volume discounts for higher user tiers.







"miniOrange provided DBS with a solution to restrict access to Fortigate VPN with Multi-Factor Authentication (MFA). Because the organisation wanted the entire setup to be protected from internet exposure,..."
Authenticator apps are utilized to generate One-Time Password (OTP) tokens based on locally stored keys or secrets. These soft tokens enable users to complete the Two-Factor Authentication (2FA) challenge even when the device lacks internet connectivity or if the authentication server is inaccessible.
In this case, your admin can give you access through their admin console. Admin can enable the “Forgot my phone” option temporarily. If you already have another phone, then you can ask the admin to reset your phone number and easily log in via 2FA.
Yes, we provide 24×7 support for all and any issues you might face while using our miniOrange solution, which includes technical support from our developers. You can get prioritized support based on the Support Plan you have opted for.

Our Other Identity & Access Management Products