Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×
Oracle E-Business Suite is a major product line of Oracle Corporation. Oracle EBS is a combined set of business applications for automating customer relationship management (CRM), Enterprise Resource Planning (ERP) and Supply Chain Management (SCM) which helps in automating the processes within organizations.
"miniOrange SSO connector enables the Single Sign-On (SSO) between Oracle EBS and Shibboleth without the need to purchase and install Oracle Access Manager (OAM) and Oracle Internet Directory (OID) license."
Oracle EBS Shibboleth SSO integration is enabled with the help of miniOrange SSO Connector. This integration involves registering the miniOrange connector as a SAML Service Provider (SP) in Shibboleth, and Shibboleth as a SAML Identity Provider (IdP) in the miniOrange connector. The authentication flow works like this: when a user tries to login into Oracle EBS, the authentication is delegated to miniOrange, which redirects the user to Shibboleth for Single Sign On Login, thereby triggering Oracle EBS Shibboleth SSO. Upon successful authentication, the user is granted access to Oracle EBS. Oracle EBS can also be protected with Shibboleth Multi-Factor Authentication, apart from Oracle EBS Shibboleth SSO. Oracle EBS URL can be added to Shibboleth Applications Dashboard by Shibboleth Admin, and users can launch it like any other Shibboleth Application. miniOrange SSO connector can enable Shibboleth SSO for the following supported Oracle EBS versions - R12 and R12.2 and it can also enable Oracle EBS integrations such as OBIEE, Hyperion/EPM Suite, ADF Applications, WebCenter and Agile. miniOrange SSO Connector can also enable Shibboleth Cloud SSO for other Oracle Products as well such as Peoplesoft, Siebel and JD Edwards.
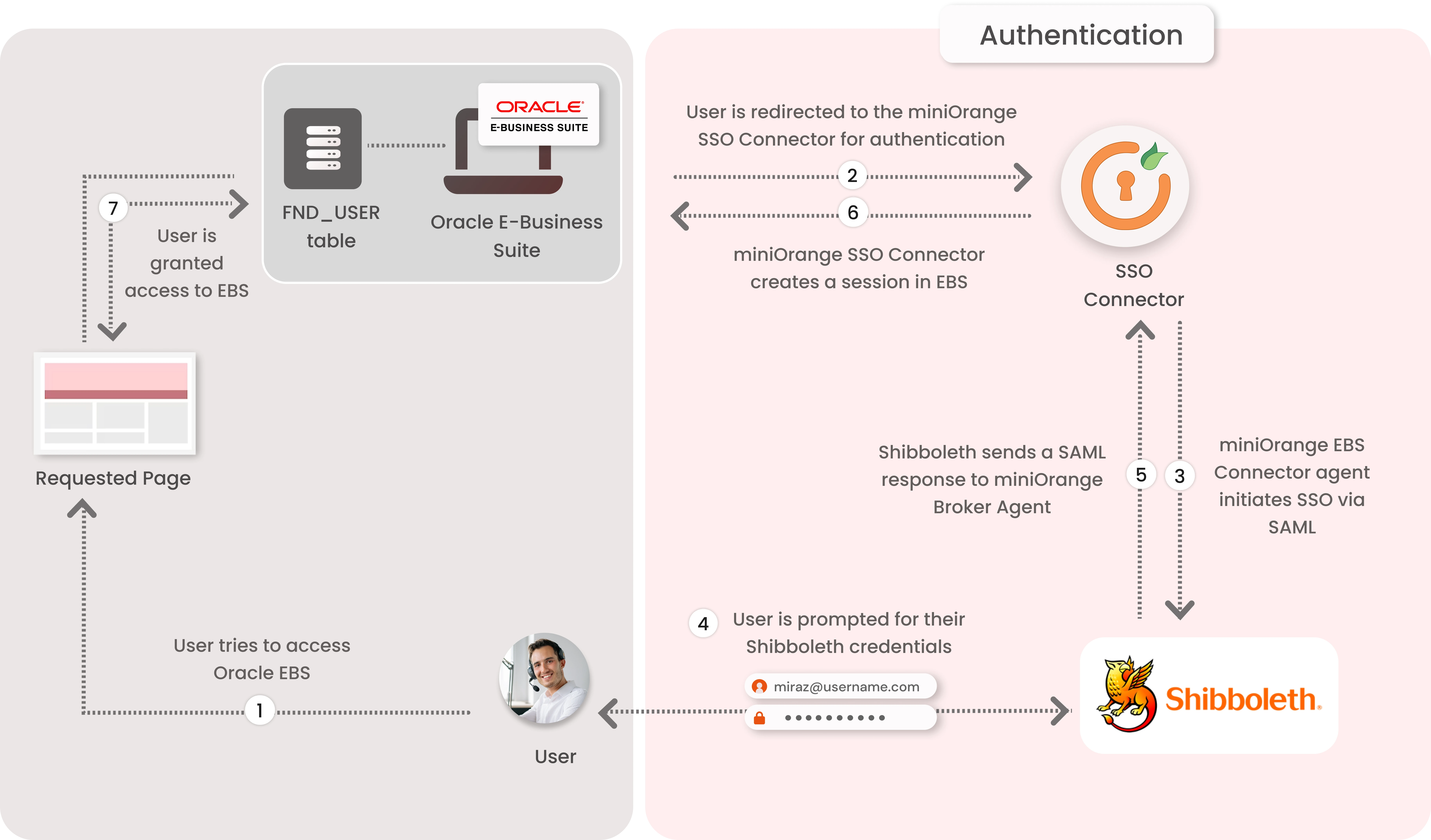
1. The User sends the request to access the Oracle E-Business Suite.
2. Oracle EBS redirects the request to the miniOrange SSO Connector for authentication.
3. The miniOrange SSO Connector redirects the user to Shibboleth for authentication.
4. The user is prompted for their Shibboleth credentials, and is authenticated upon a successful response.
5. The connector receives the user’s Oracle EBS registered username/email from Shibboleth via SAML attributes.
6. The connector checks the value of the username/email received from Shibboleth against the FND_USER table in the Oracle EBS Database & creates a session for them.
7. Upon successfully creating a session, user is redirected to the Oracle E-Business Suite portal as logged-in user
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, Azure AD, OpenLDAP, Google, AWS Cognito etc), Identity Providers (like Shibboleth, Ping, Okta, OneLogin, KeyCloak), Databases (like MySQL, Maria DB, PostgreSQL) and many more.
eg. idp.encryption.optional = true
<MetadataProvider xmlns:samlmd="urn:oasis:names:tc:SAML:2.0:metadata"
id="miniOrangeInLineEntity" xsi:type="InlineMetadataProvider" sortKey="1">
<samlmd:EntityDescriptor ID="entity" entityID="<SP-EntityID / Issuer from Service Provider Info tab in plugin.>"
validUntil="2020-09-06T04:13:32Z">
<samlmd:SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true"
protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<samlmd:NameIDFormat>
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
</samlmd:NameIDFormat>
<samlmd:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
Location="<ACS (AssertionConsumerService) URL from Step1 of the plugin under Identity Provider Tab.>"
index="1" />
</samlmd:SPSSODescriptor>
</samlmd:EntityDescriptor>
</MetadataProvider>
idp.nameid.saml2.default=urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress
<!-- SAML 2 NameID Generation -->
<util:list id="shibboleth.SAML2NameIDGenerators">
<!--<ref bean="shibboleth.SAML2TransientGenerator" /> -->
<!-->ref bean="shibboleth.SAML2PersistentGenerator" /> -->
<bean parent="shibboleth.SAML2AttributeSourcedGenerator"
p:format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"
p:attributeSourceIds="#{ {'email'} }" />
</util:list>
<!-- Note: AttributeDefinitionid must be same as what you provided in attributeSourceIds in conf/saml-nameid.xml -->
<resolver:AttributeDefinitionxsi:type="ad:Simple" id="email" sourceAttributeID="mail">
<resolver:Dependency ref="ldapConnector" />
<resolver:AttributeEncoderxsi:type="enc:SAML2String" name="email" friendlyName="email" />
</resolver:AttributeDefinition >
<resolver:DataConnector id="ldapConnector" xsi:type="dc:LDAPDirectory" ldapURL="%{idp.authn.LDAP.ldapURL}"
baseDN="%{idp.authn.LDAP.baseDN}" principal="%{idp.authn.LDAP.bindDN}"
principalCredential="%{idp.authn.LDAP.bindDNCredential}">
<dc:FilterTemplate>
<!-- Define you User Search Filter here -->
<![CDATA[ (&(objectclass=*)(cn=$requestContext.principalName)) ]]>
</dc:FilterTemplate>
<dc:ReturnAttributes>*</dc:ReturnAttributes>
</resolver:DataConnector>
<afp:AttributeFilterPolicy id="ldapAttributes">
<afp:PolicyRequirementRulexsi:type="basic:ANY"/>
<afp:AttributeRuleattributeID="email">
<afp:PermitValueRulexsi:type="basic:ANY"/>
</afp:AttributeRule>
</afp:AttributeFilterPolicy>
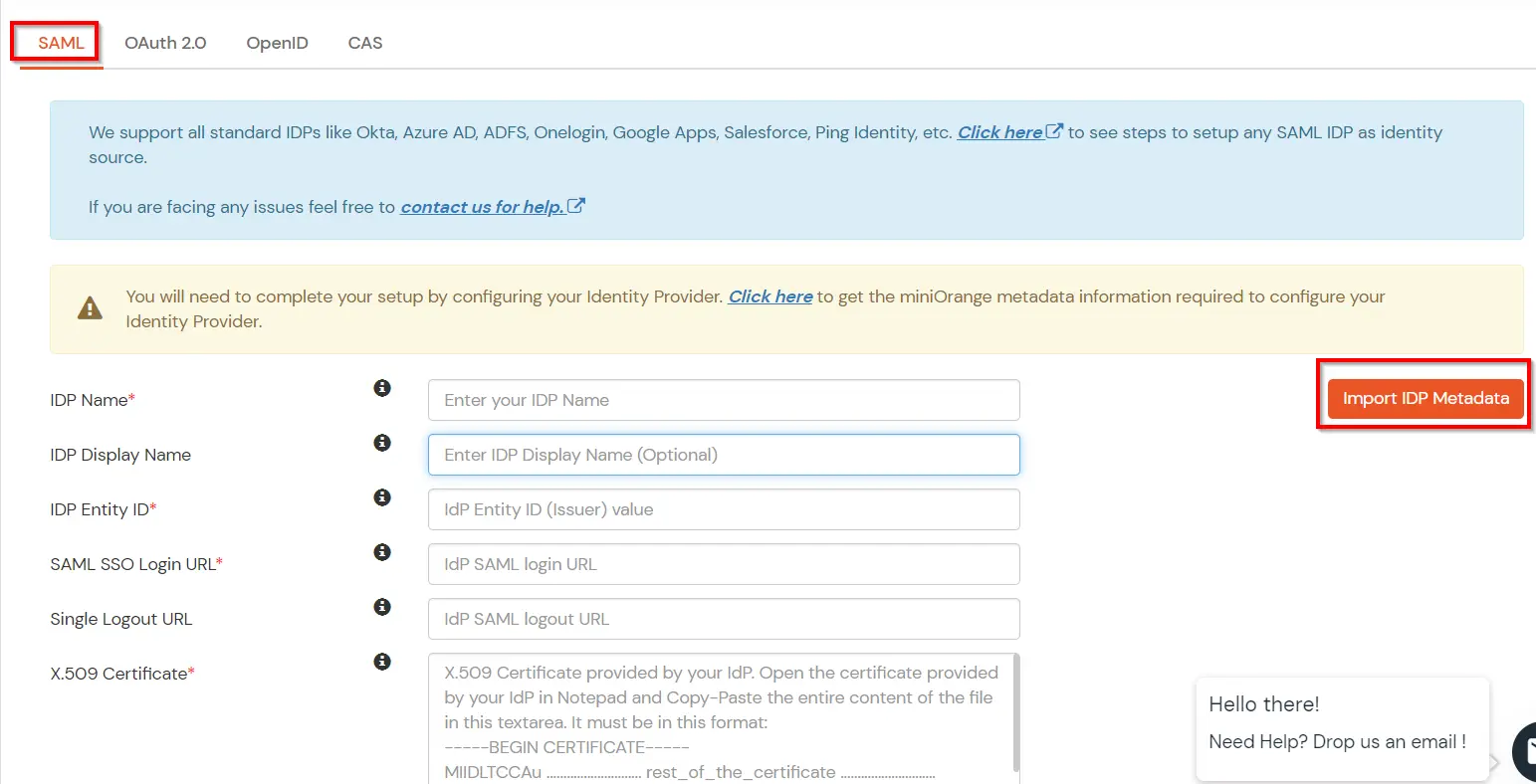
| IDP Entity ID | https://<your_domain>/idp/shibboleth |
| Single Login URL | https://<your_domain>/idp/profile/SAML2/Redirect/SSO |
| Single Logout URL | https://<your_domain>/idp/shibboleth |
| X.509 Certificate | The public key certificate of your Shibboleth server |
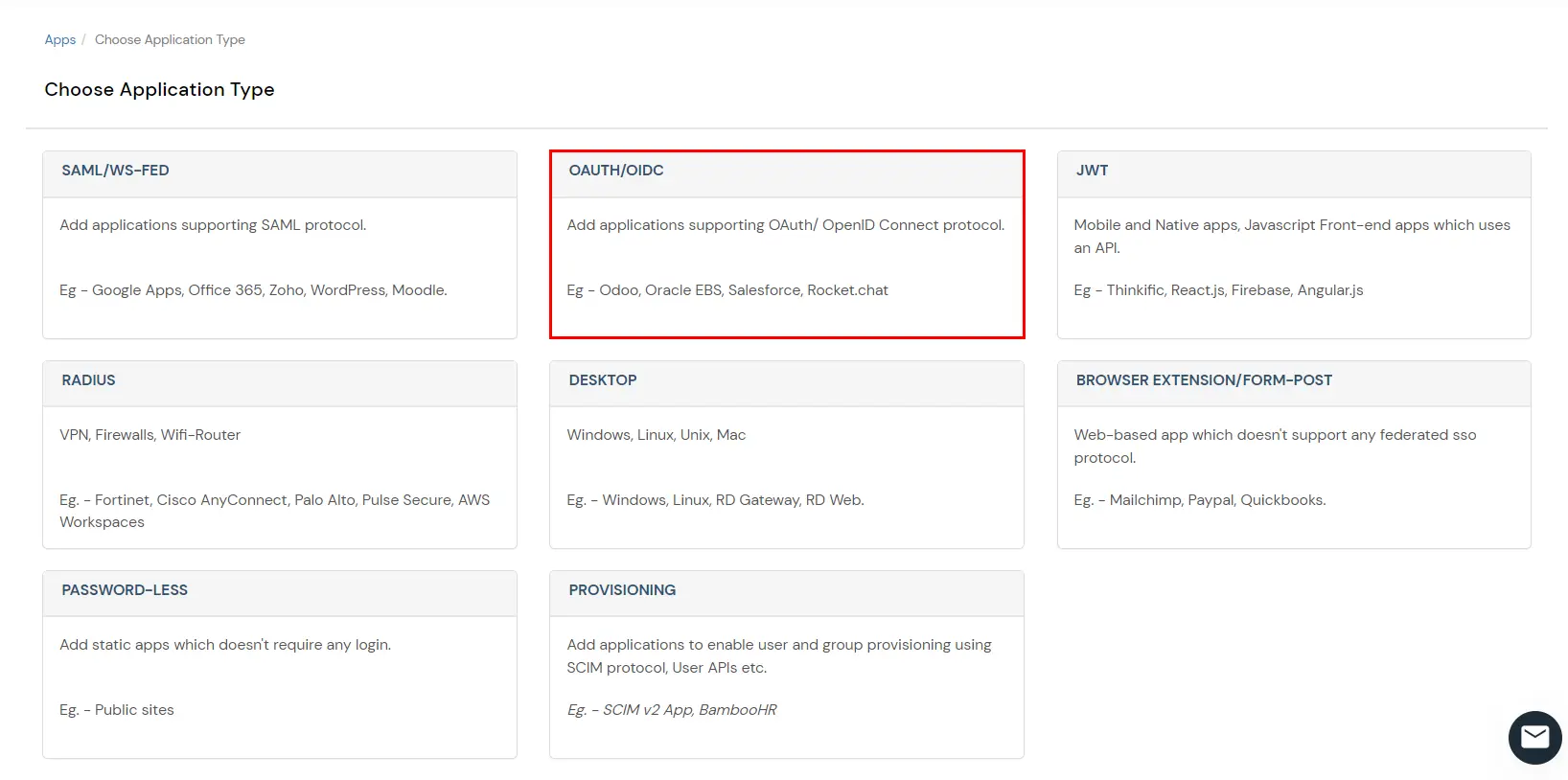

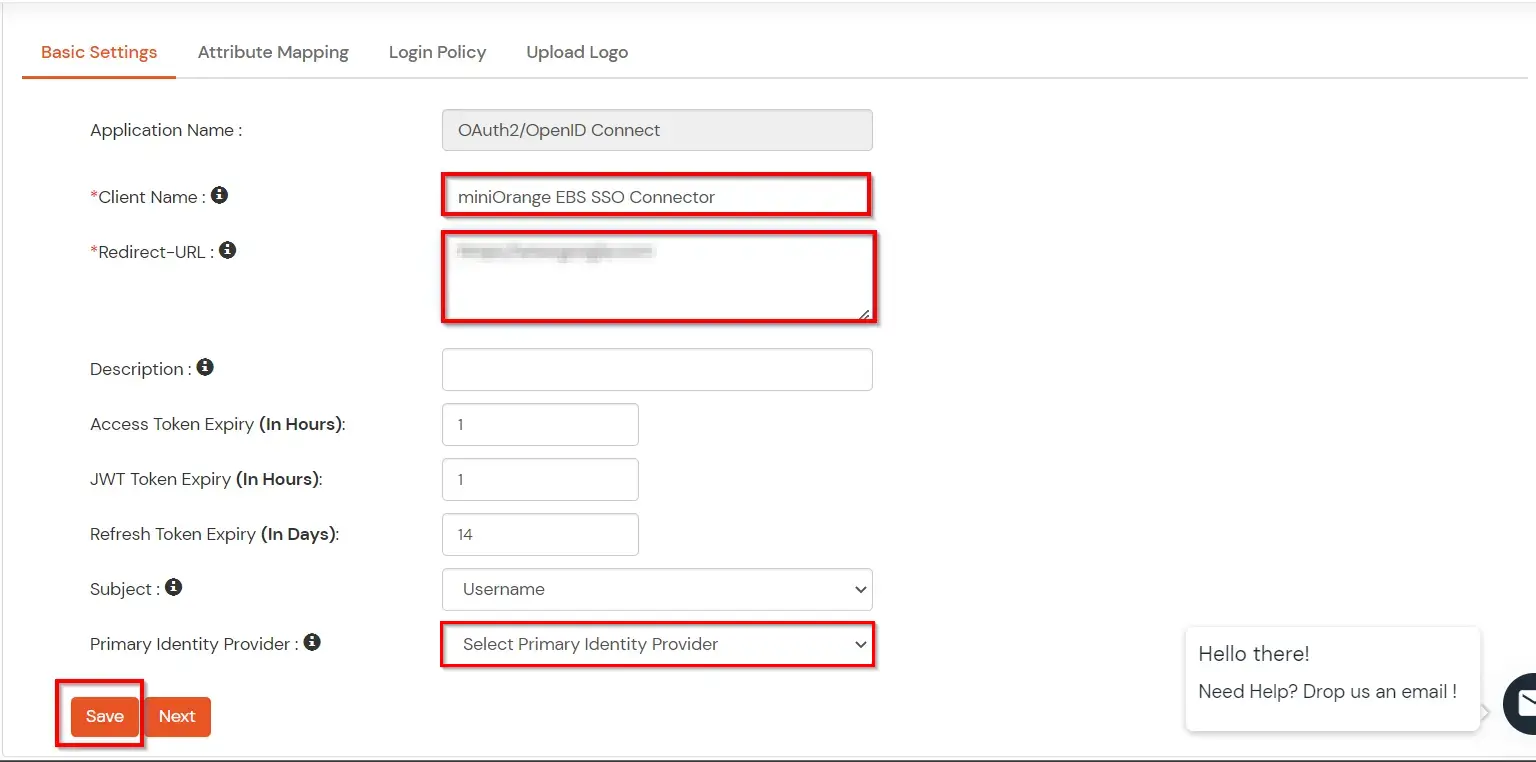
You can edit Application by using the following steps:
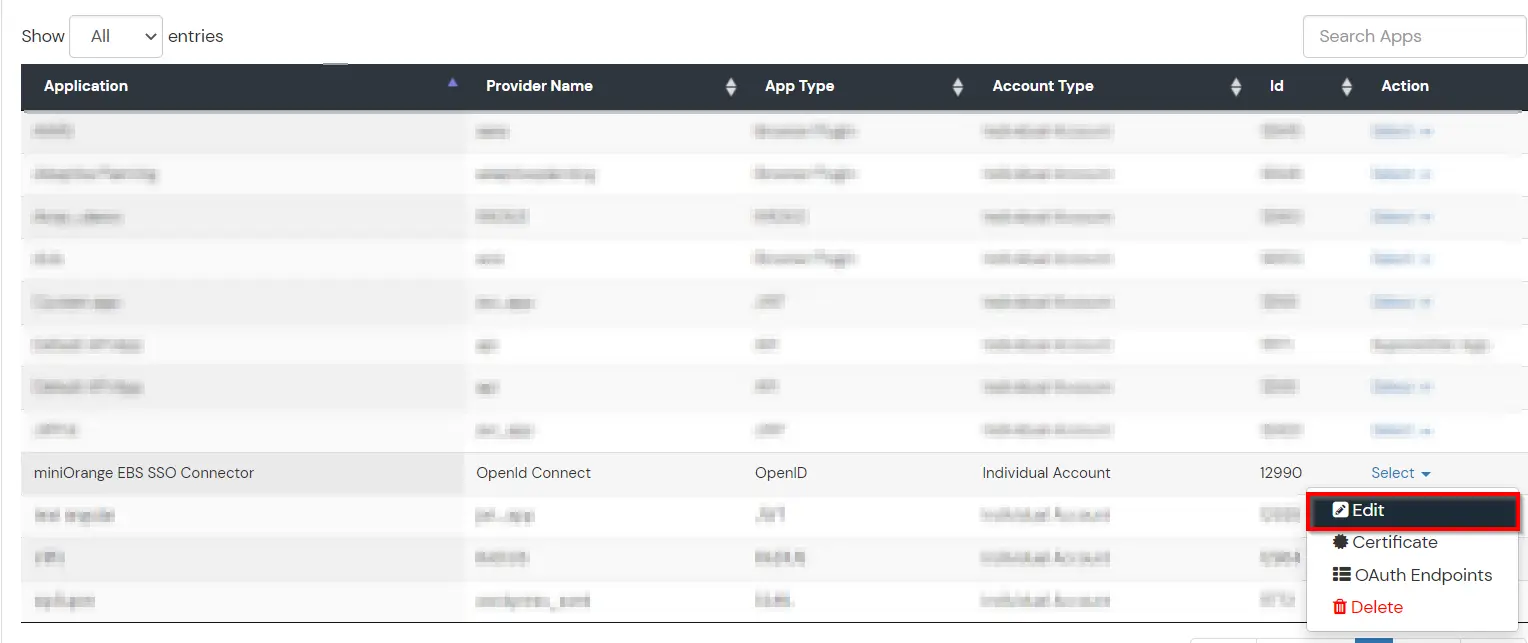
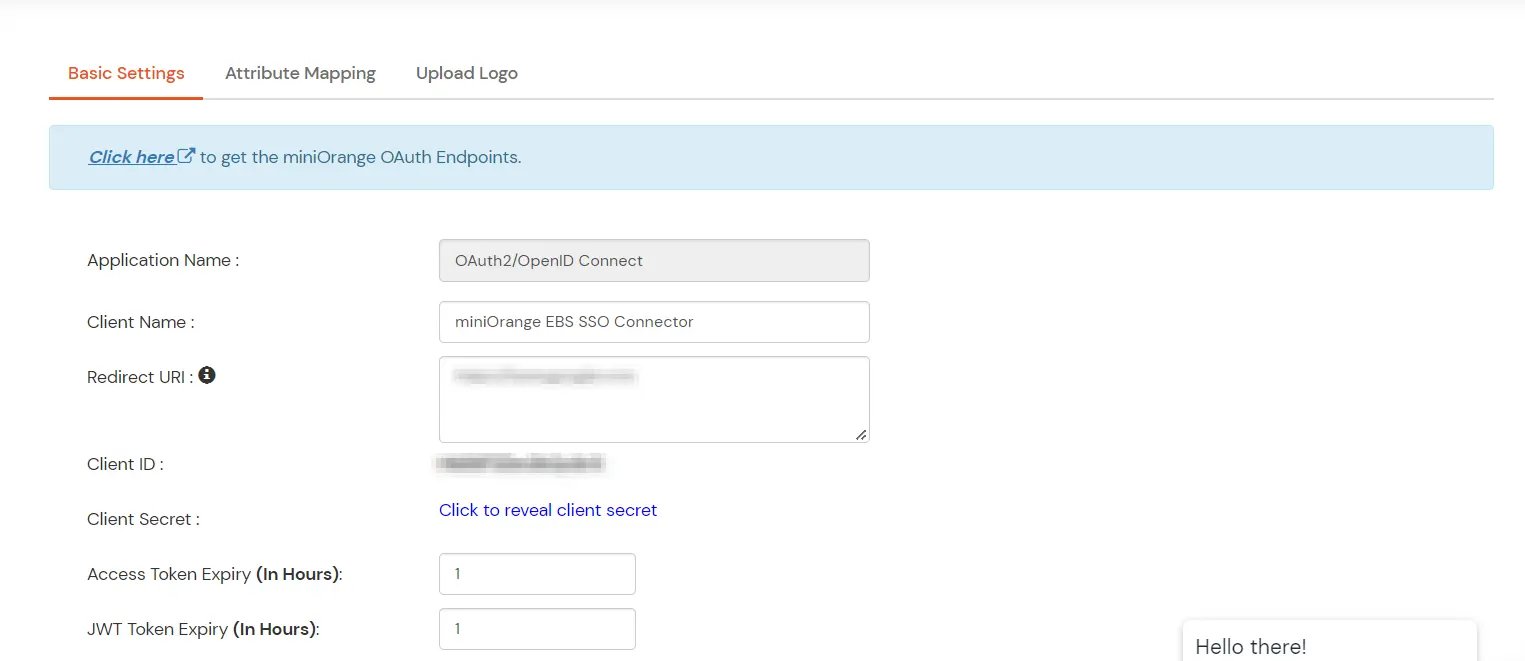
Note: Oracle and Java are registered trademarks of Oracle and/or its affiliates. miniOrange is a separate entity.

Our Other Identity & Access Management Products