Need Help? We are right here!
Search Results:
×
The Device-based Adaptive Authentication method, which is commonly known as Device Restriction, allows administrators to restrict user access to a limited number of trusted devices, such as browser sessions. This enhances security by allowing authorized devices and controlling access from unauthorized ones.
For example, once a user's device has been registered, they can log in without any restrictions. However, if the number of registered devices exceeds the administrator's defined limit, the user may be challenged or denied access based on the Device Restriction settings or policies set by the admin.
Device Restriction operates by restricting the usage of an application exclusively to the intranet or office premises, preventing user access from outside the network. Additionally, it allows selective access for specific users from outside the network by creating distinct groups.
Every device has a unique MAC Identity, and enabling MAC-based restriction allows user access from only those devices whose MAC ID is configured.
You can set the custom policies to allow user access from only trusted or approved mobile devices within the corporate network by enabling Mobile Restriction.
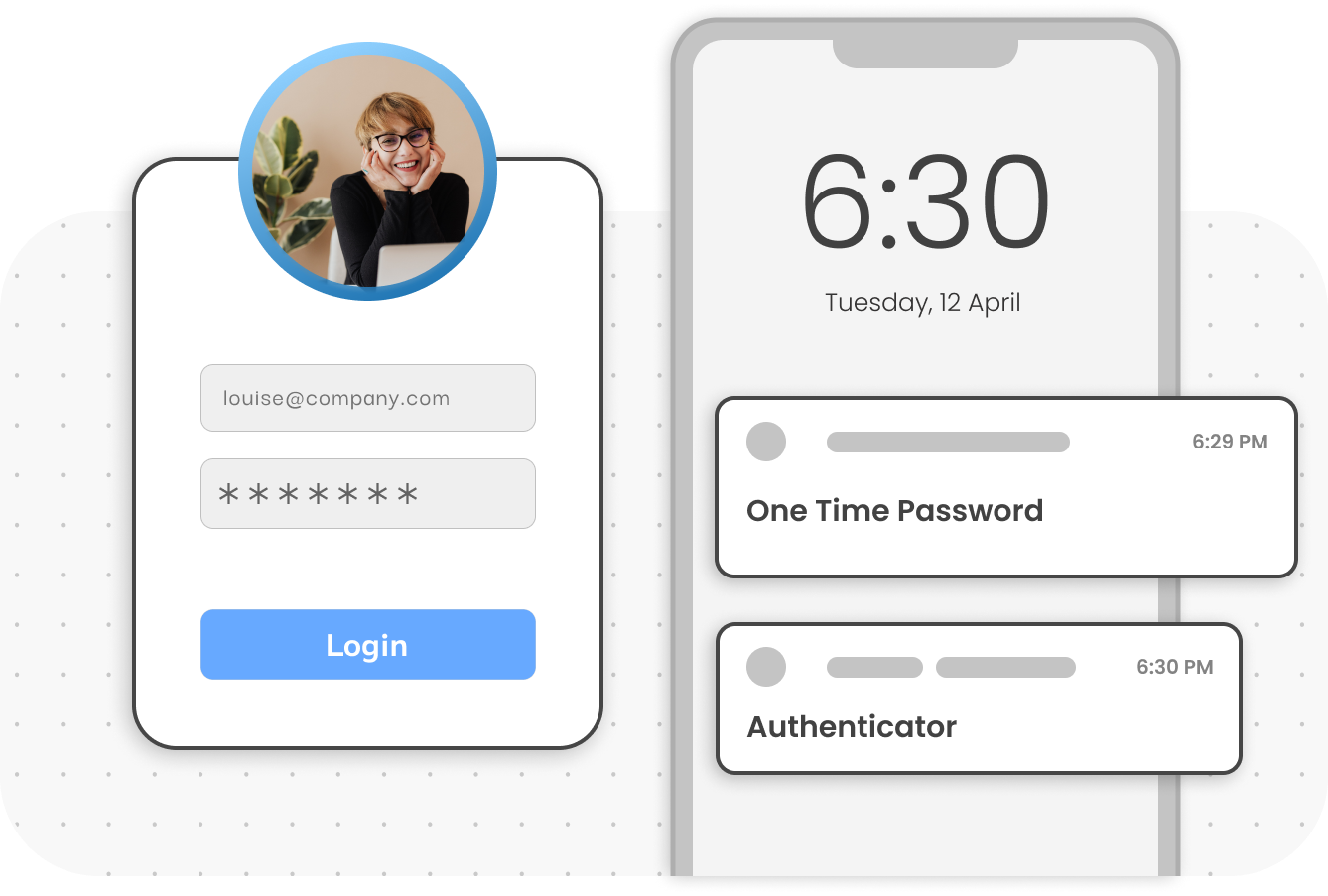
Choose from 15+ MFA methods like push notifications, hardware tokens, OTP verification, and many more. Configure your preferred MFA method at your convenience.
Device Restriction limits user access to critical apps from trusted devices only within the corporate network and enhances security by preventing unauthorized access.
Administrators can define different groups of users with varying levels of access permissions. This allows selective access for specific users from outside the network while maintaining strict restrictions for others and provides flexibility in managing access based on user roles/requirements.
Limiting access to trusted devices minimizes the risk of unauthorized or unknown devices accessing enterprise apps, protecting sensitive data and reducing security vulnerabilities.
Device Restriction limits access to approved devices in a secure network, ensuring compliance and data integrity. This helps you comply with international regulations like GDPR, HIPAA, PCI DSS, SOX, and many more.
For use-cases and risk situations require customized security policies. You can effectively set custom Device Restriction policies like
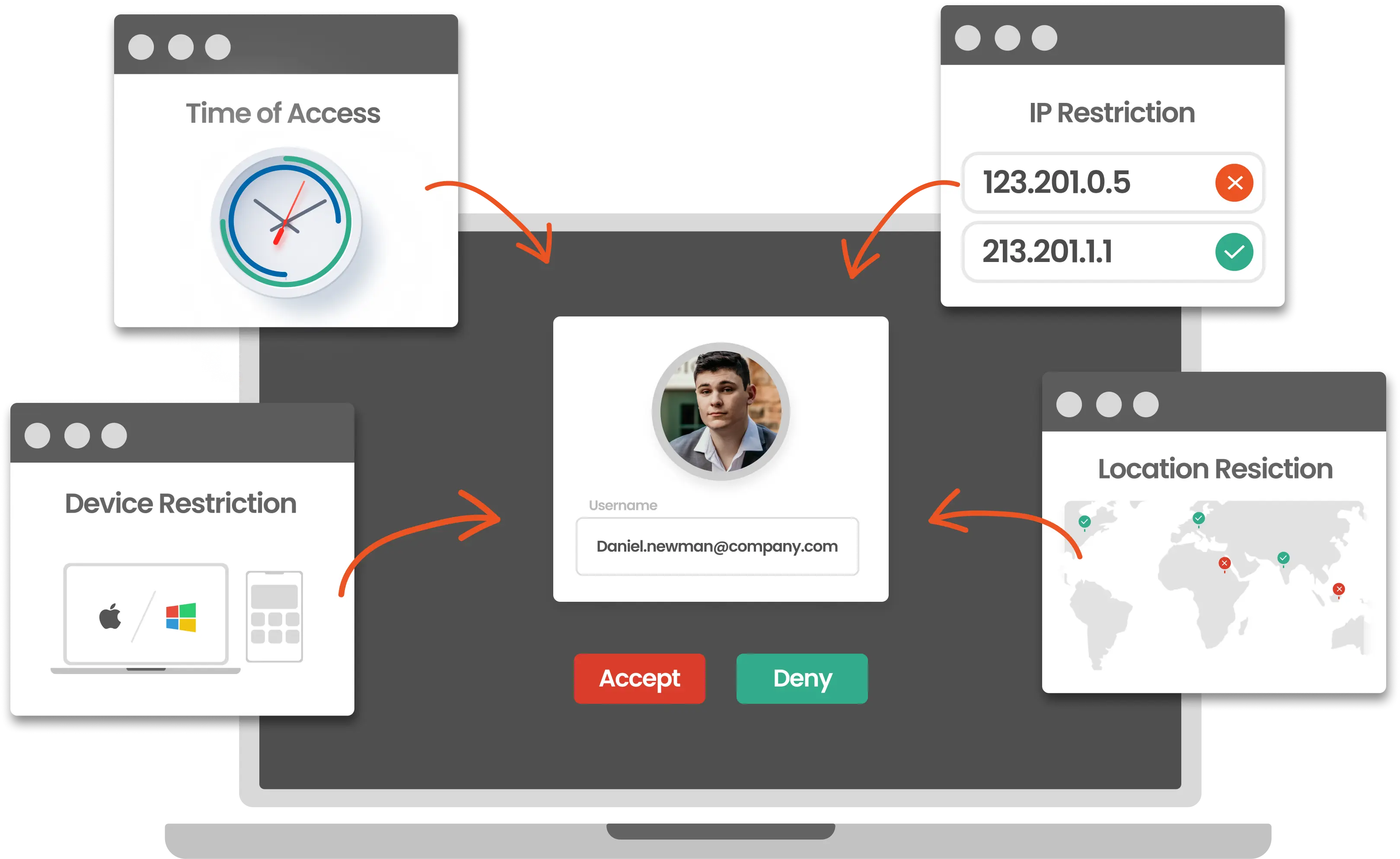
Enforce Risk-Based Authentication to deal with high-risk scenarios. Based on the level of risk, you can configure custom Adaptive MFA policies based on contextual factors other than Device Restriction, like:
per user per month
*Please contact us to get volume discounts for higher user tiers.
An advanced level of authentication with two or more levels of security factors such as OTP over SMS, TOTP tokens, OTP over Email, hardware tokens etc.
Restrict the number of devices the users can access the services on, Geo-location, IP restriction, time of login, etc.
It provides an additional layer of MFA security based on risk and access provided by the security admin to control user access.

Our Other Identity & Access Management Products