Need Help? We are right here!
Search Results:
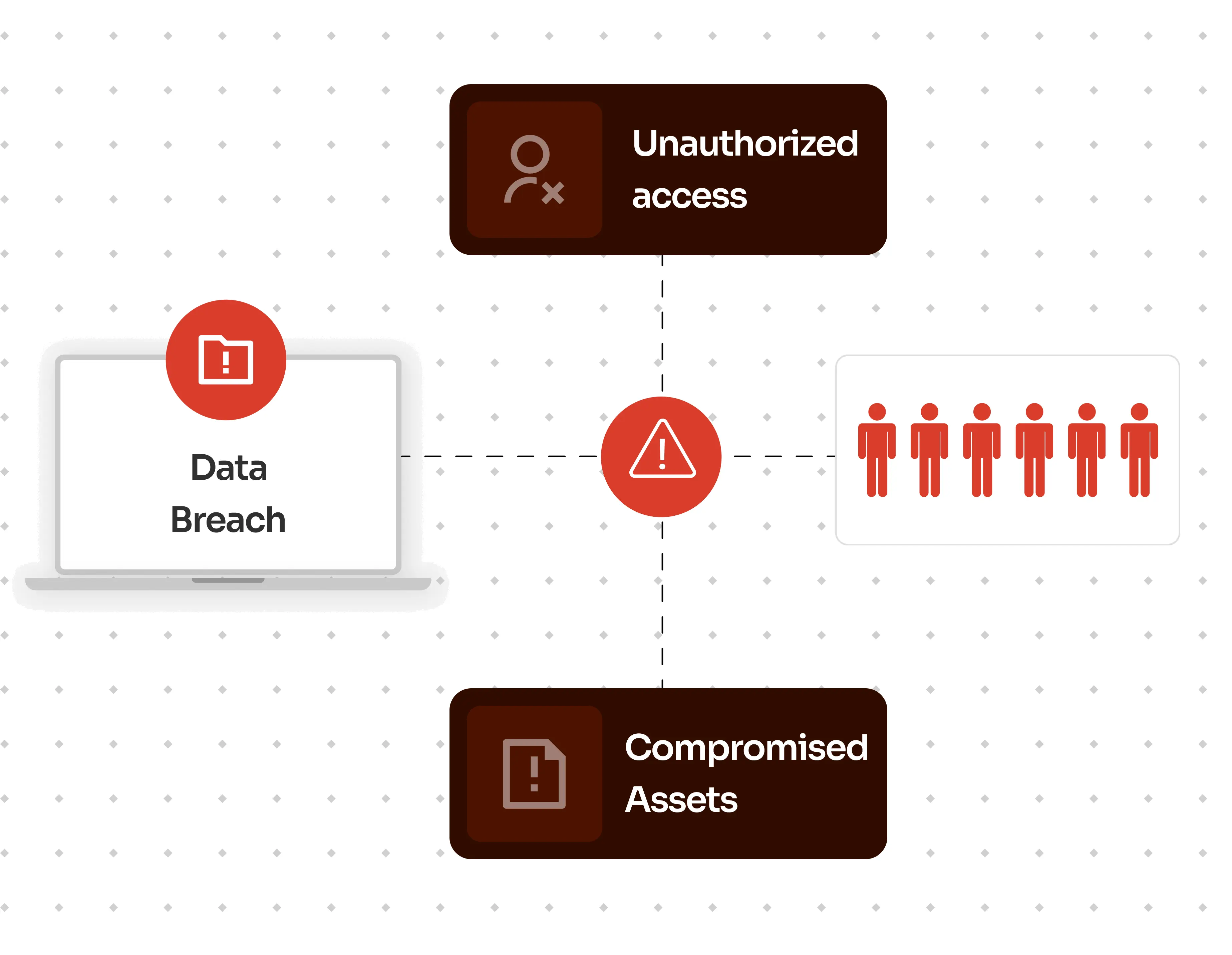
×In a world where mobile devices have become an integral part of our work lives, securing access to critical resources is of utmost importance. However, the convenience of mobile connectivity also brings forth security concerns. Unauthorized access, data breaches, and compromised assets are potential risks that must be mitigated.
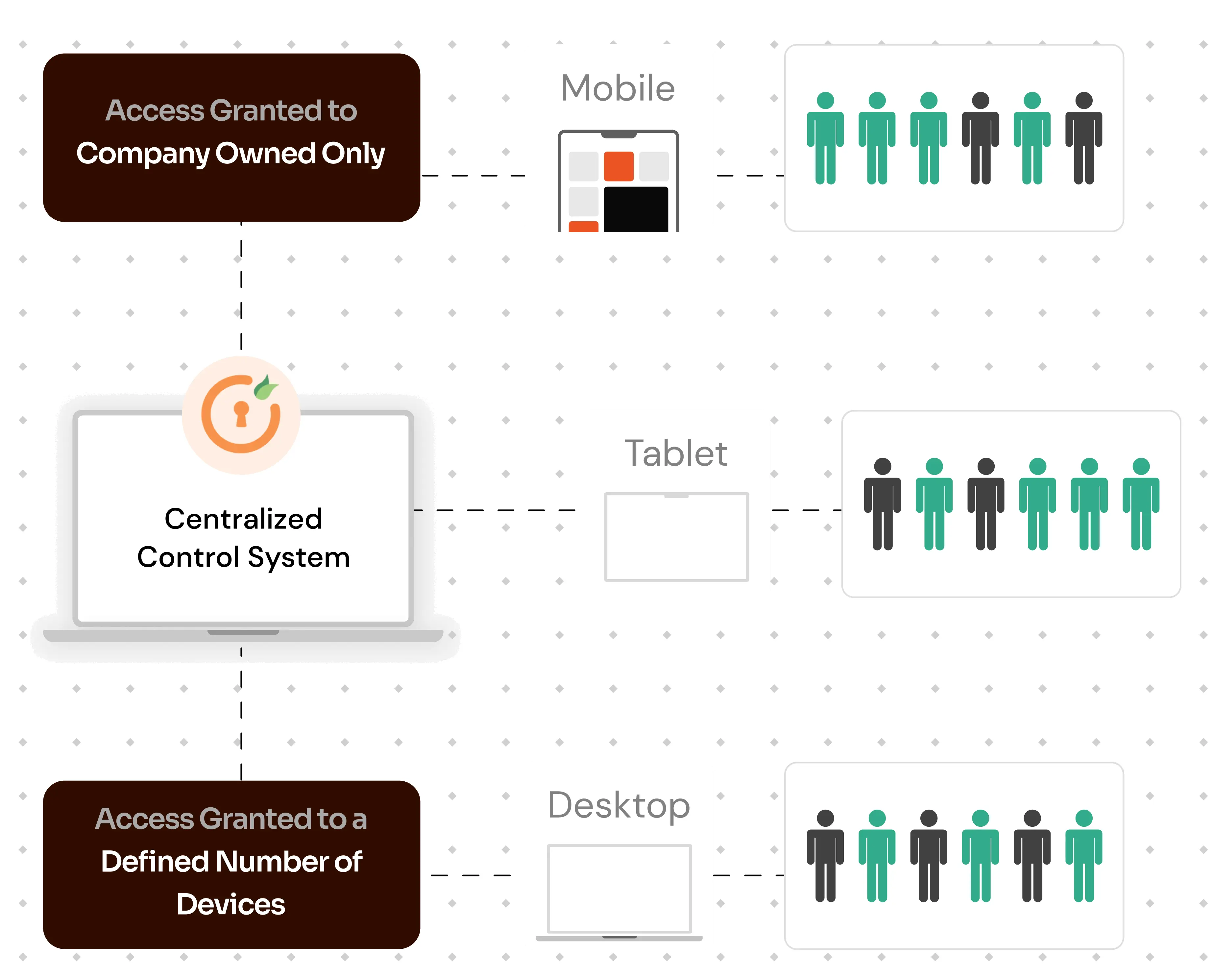
Under the principle of COBO (Company Owned/Business Only), this restriction system typically emphasizes granting access only to corporate devices, ensuring heightened security. By designating certain devices as "trusted", this method not only curtails user access to those specific devices but also potentially restricts access on personal devices, thereby adding an intensified layer of security against unauthorized access
per user per month
*Please contact us to get volume discounts for higher user tiers.
Register and label devices as "trusted", facilitating seamless access and aligning with COBO (Company Owned/Business Only) policies where only company-owned devices are prioritized.
An upper cap on the number of devices that can be registered. Set by the administrator, this ensures tighter control and alignment with company device policies.
When unregistered devices are used or when device limits are exceeded, users face advanced security barriers, such as security questions, OTPs, and biometrics.
Beyond just challenging, the system can outright deny access if the user is trying to access from an unregistered device or has exceeded the allowed device count.
By restricting access to "trusted" corporate devices under the COBO model, the risk from personal devices is minimized, reducing the risk of data breaches and unauthorized access.
Align with regulatory requirements by implementing stringent security measures for mobile device access.
Beyond just devices, MDM allows fine-tuned control down to specific browser sessions, and the system denies access to non-COBO devices or when device limits are exceeded.
Strict access control not only safeguards the company's data and standing in the market but also ensures efficient distribution and use of company resources.
Integrate and selectively manage devices with centralized control, while maintaining corporate security standards. Simultaneously, administrators can select resources that can be accessed via mobile devices, ensuring appropriate access levels.
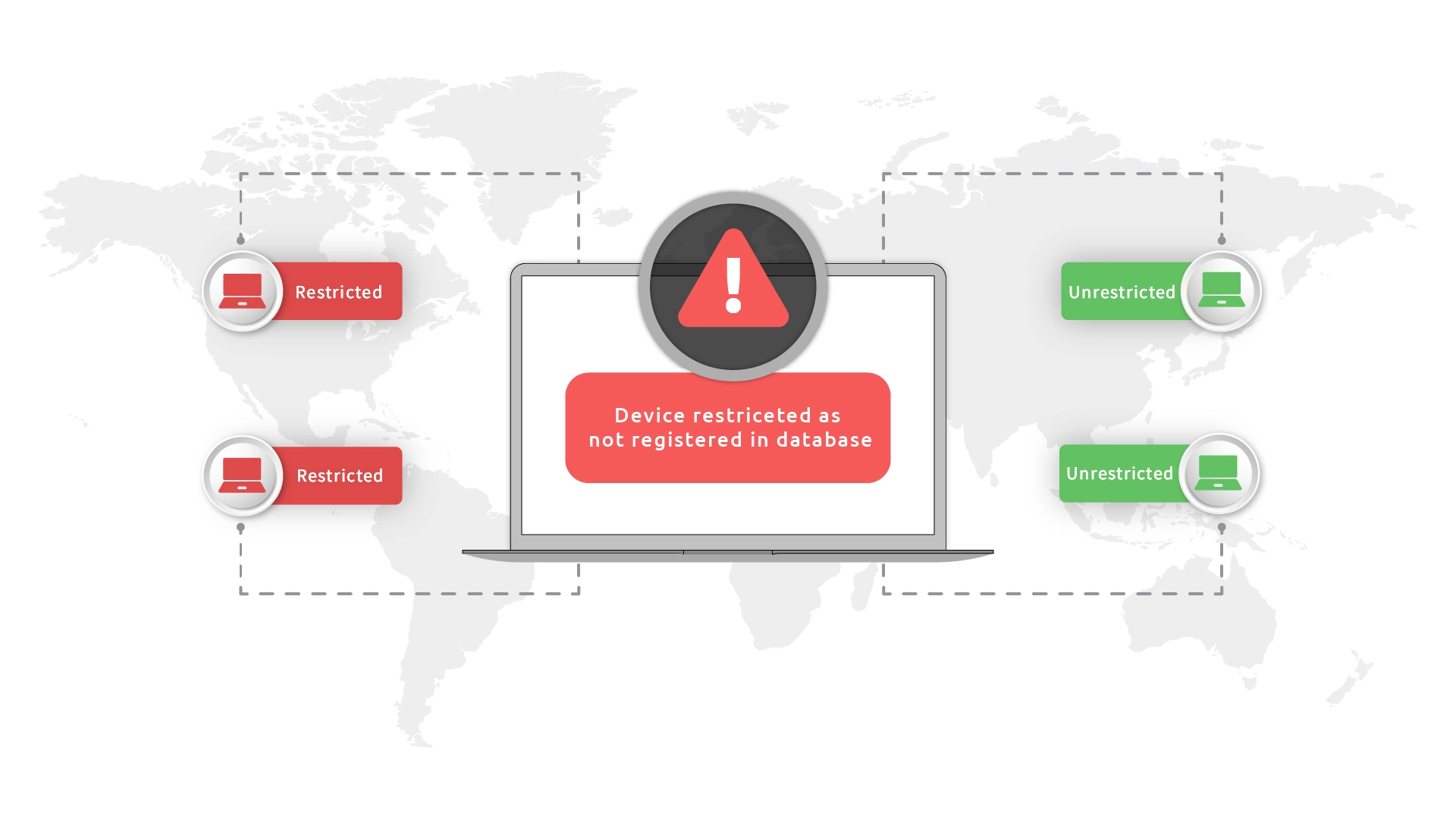
Enable a robust device-based policy which limits login process, ensuring exclusive access to your most valuable information.
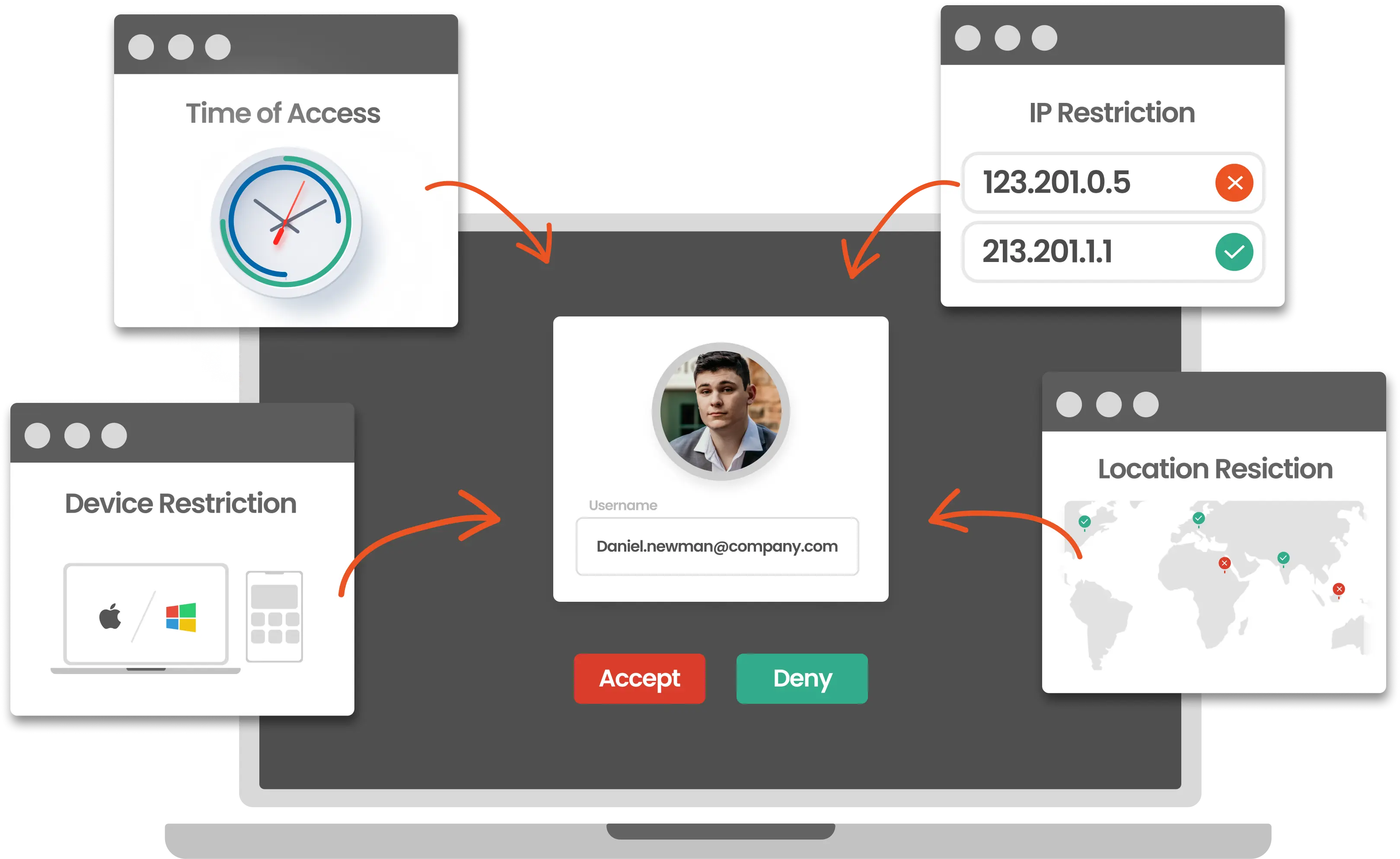
Secure your enterprise systems in high-risk scenarios by enabling admins to set MFA policies for different scenarios and use cases.
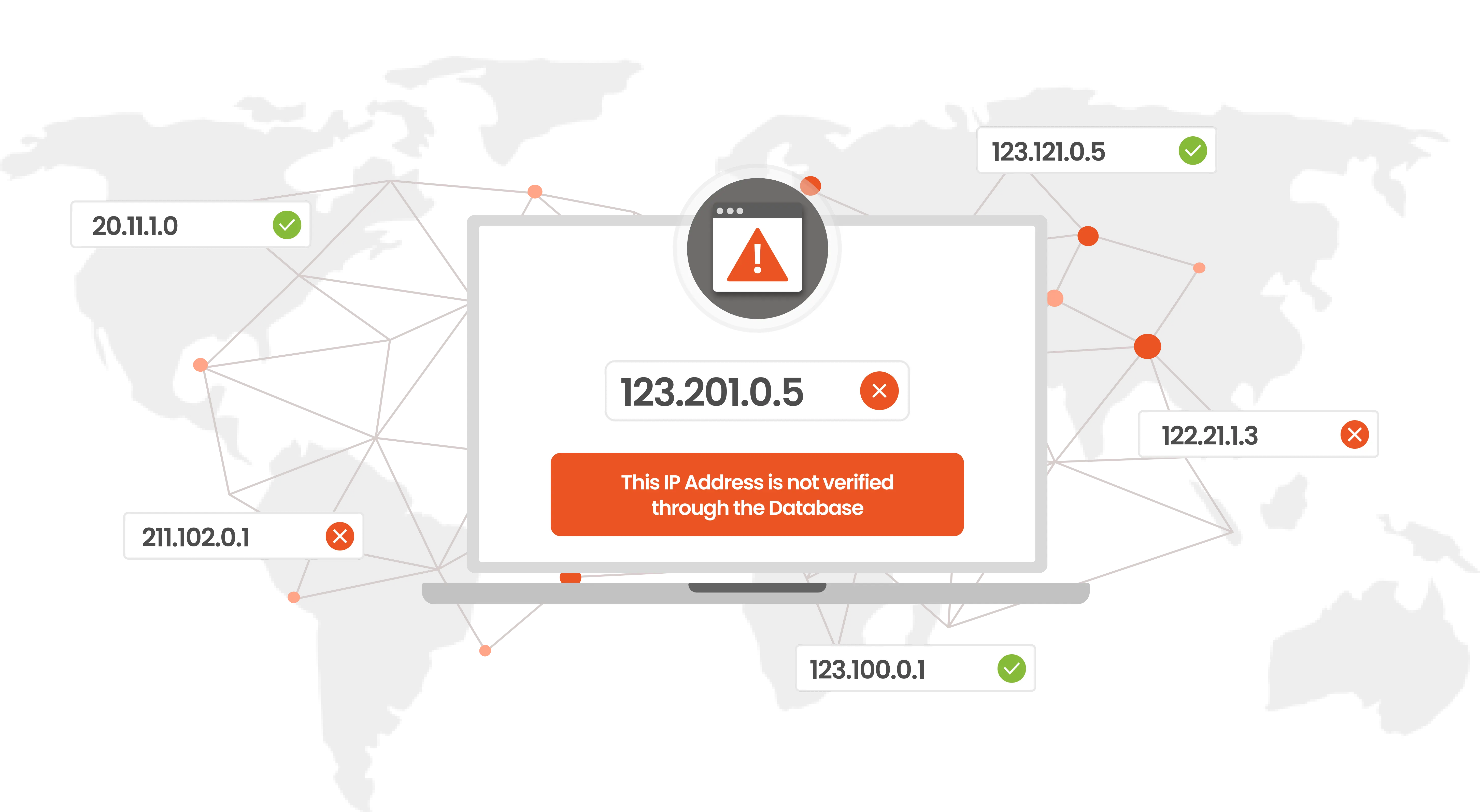
Restrict unwanted user access to crucial business data from unknown IP addresses.

Our Other Identity & Access Management Products