Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry. Our team will soon reach out to you.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×
In today's digital landscape where securing remote access to critical systems is non-negotiable, Remote Desktop Services (RDS) prove to be a valuable tool for organizations because it enables your users to secure remote access to desktops and applications. However, ensuring the security of Remote Desktop connections is paramount. This is where Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA) comes into play as an indispensable security measure.
In this article, we'll explore the compelling reasons why enabling 2FA/MFA for Remote Desktop Services like RD Gateway, RD Web Access, RD HTML5 Web Client and RDP is highly essential. 2FA/MFA significantly elevates the security of Remote Desktop Access, from strengthening user authentication to safeguarding sensitive data, while also enhancing user experience.
It is very important to have second-factor authentication. miniOrange provides an easy-to-setup Two-Factor Authentication (2FA) or Multi-Factor Authentication (MFA) solution for your Virtual Desktop and Remote Desktop Services (RDS). After entering your username and password as the first factor for the Remote Desktop Services (RDS) MFA, you will have to enter the second factor, which will authenticate you to use your machine virtually.
miniOrange MFA provides 15+ 2FA/MFA methods like OTP over SMS/Email, Google/Microsoft/miniOrange Authenticator, Hardware tokens, and many more. Let's delve into why Multi-Factor Authentication (MFA) is a game-changer for organizations seeking a robust defense against evolving cyber threats like unauthorized access and data breaches.
Be Cyber Insurance compliant with miniOrange MFA solution. Read More
Receive a text on your mobile with the information required to validate yourself for the second factor.

Receive a time based OTP token (TOTP) by an external authentication app such as Google, Microsoft and Authy authenticator.

Use the miniOrange authenticator to login in the form of a soft token, push notification or QR code.

MFA using login links and password keys on your registered email address.
Use a physical USB token on your computer, which generates the required information to gain access.

Answer a few knowledge based security questions which are only known to you to authenticate yourself.

It uses built-in authentication methods like laptop password or pin, mobile, Windows Hello, Biometrics (FaceID/fingerprint), and Hardware Tokens.

“ By using a single solution, you can upgrade the security posture of your entire organization for remote access. ”
The Multi-Factor Authentication (MFA/2FA) for Remote Desktop Gateway (RD Gateway) provides additional Two-Factor Authentication security for secure access to Remote Desktop, RDWeb, and RemoteApp Access logons on top of Active Directory or Azure AD logins. It blocks connections to RDP servers if users have not passed the 2FA/MFA challenge.
The miniOrange RD (Remote Desktop) gateway MFA solution can work with Active Directory or Azure AD logins. It allows users to configure 15+ 2FA/MFA methods, including Push Notification through miniOrange authenticator and out-of-band methods like SMS and Email links, to secure Remote Desktop Access for users.
After configuring the MFA solution, users must enter their username, and password, which can be Active Directory or Azure AD login credentials. Based on the 2FA/MFA method, they will receive a notification or SMS/Email link to log in. The Windows MFA Solution by miniOrange can also provide secure access to Windows machines with Active Directory or Azure AD login. There are also customized MFA solutions for other OS systems like Mac & Linux.
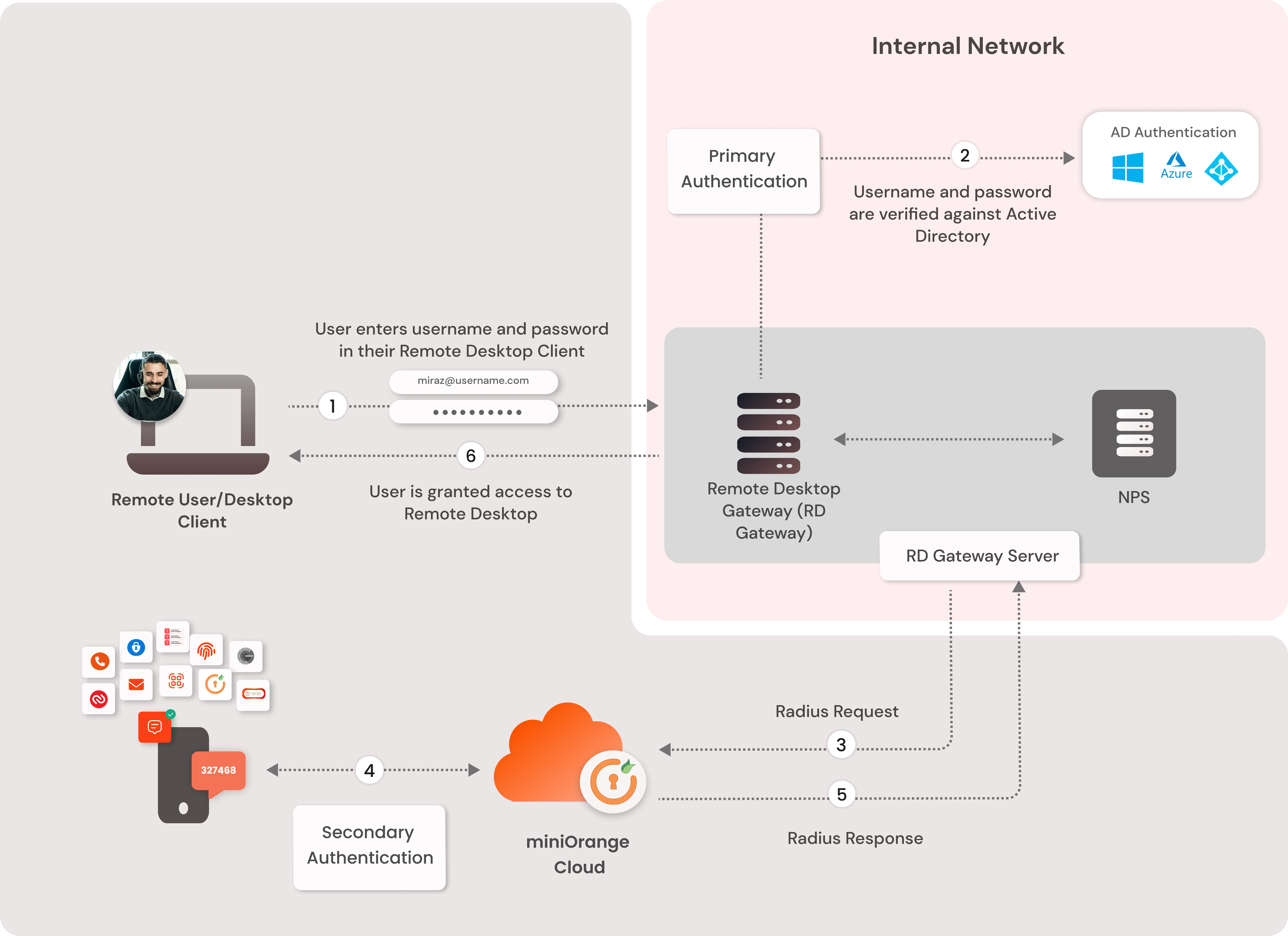
Microsoft Remote Desktop Web Access (RD Web) MFA configuration is a security feature that requires users to authenticate themselves for two or more factors to access company resources, applications, or servers through RD Web. This authentication method is initiated when a user logs into the Remote Desktop Service (RDS) through a Remote Desktop Client or the RD Web login page.
The miniOrange RD Web component sends a RADIUS request to the miniOrange RADIUS server, which authenticates the user via the Local Active Directory. After successful authentication, the user is granted access to the RD Web Service. Enabling Multi-Factor Authentication (MFA) increases the security of the organization's resources by requiring additional verification factors beyond usernames and passwords.
The miniOrange MFA for RD Gateway is completely agentless, which means that it can be seamlessly deployed even on non-domain joined systems as well. This makes deployment faster and simpler. miniOrange offers 2FA/MFA methods such as Push notifications and Authentication via Email/SMS link for RD Gateway.
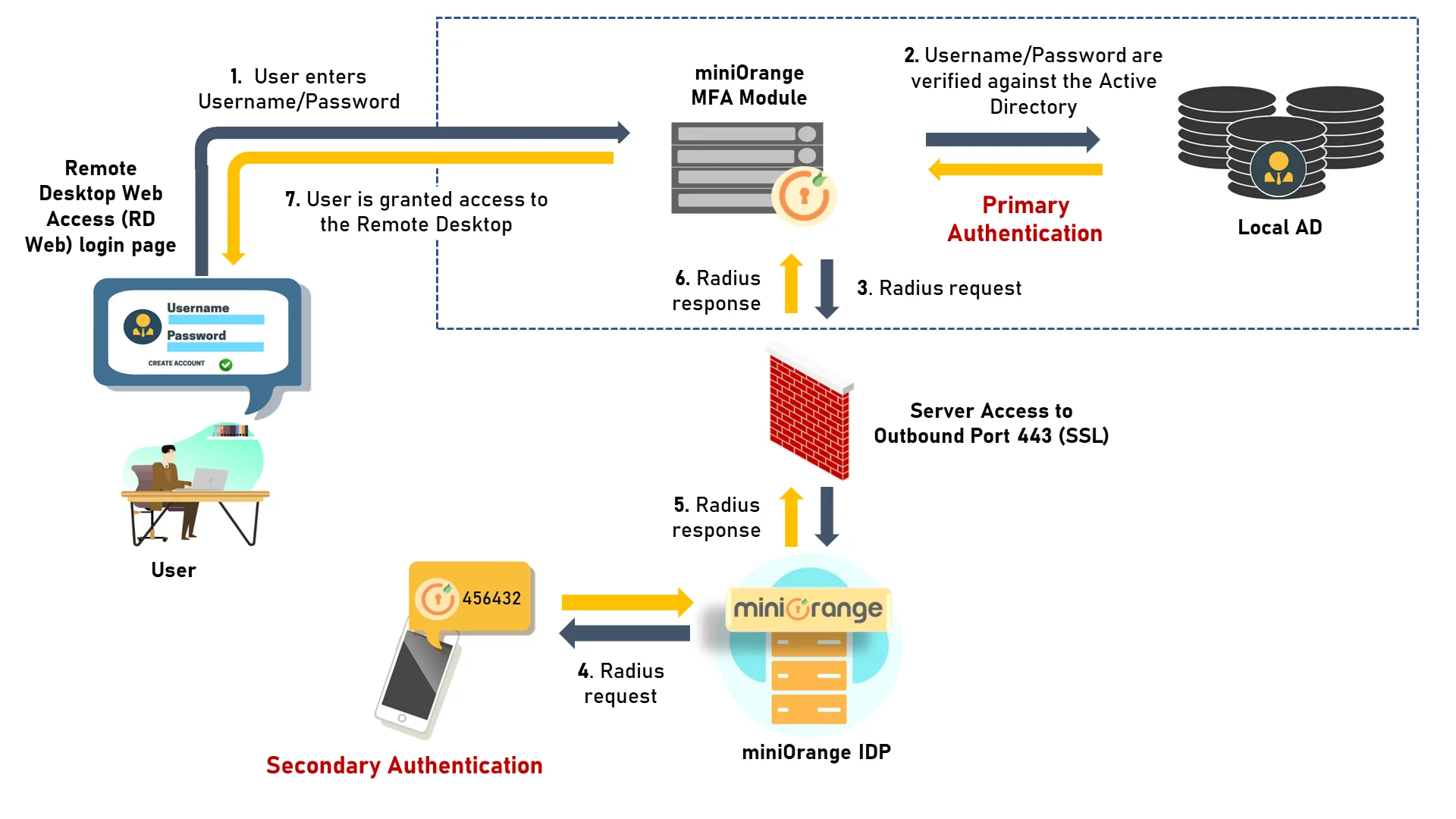
miniOrange supports all the latest HTML5-based RD web clients for enabling Multi-Factor Authentication (MFA) for remote access for users. This allows users to use 15+ 2FA/MFA methods provided by miniOrange MFA without changing their primary authentication (username and password) using the existing on-premise Active Directory. The self-service console allows user registration and MFA setup. The custom groups and policies can also be set up for RDS MFA based on the organization's requirements. MFA security can further secure access to RemoteApp programs hosted via RD Web Access and Web Client.
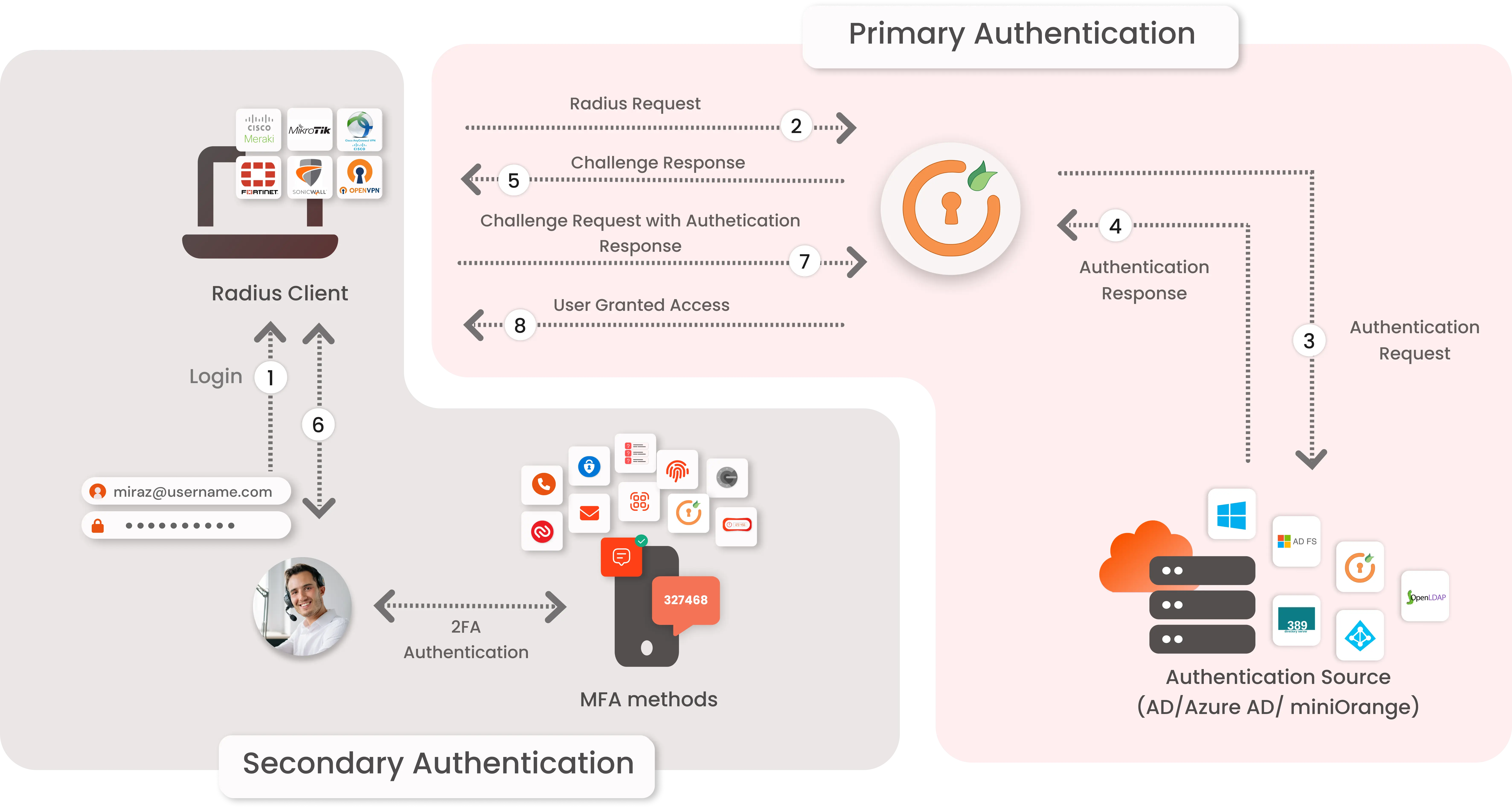
Multi-Factor Authentication (MFA) for Remote Desktop Protocol (RDP) is a crucial security measure for remote access to Windows systems and servers. It involves configuring Multi-Factor Authentication, integrating it with the RDP server, and setting authentication policies. When a user connects via RDP, they are prompted to provide their username and password (which can be AD or Azure AD credentials). Then they have to fulfill an additional authentication factor like a one-time code from a mobile app, Microsoft/Google/miniOrange Authenticator, or biometric scan.
Setup RDP MFA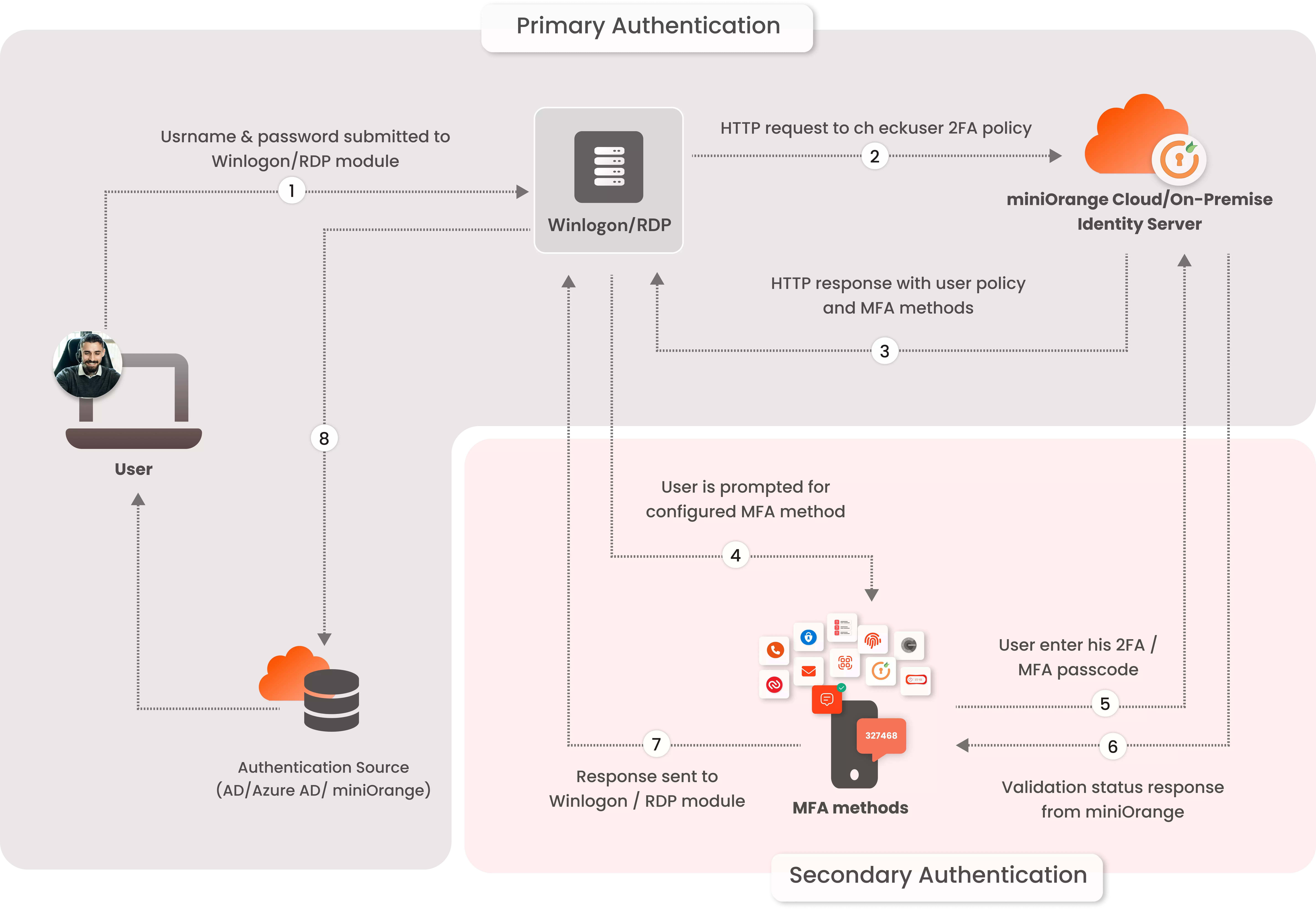
Example : For instance, organizations that prohibit internet access for security reasons may utilize Offline MFA to guarantee that users are prompted with 2FA/MFA via authenticator apps and granted secure access without the need for any authentication server.
Example : Admins can set custom MFA policies such as allowing user access via MFA for certain types of users, bypassing MFA for Admin accounts, or for a specific time after subsequent login, and many more.
Example : Organizations looking to secure their entire infrastructure Remote Desktop Services, Network Devices (VPNs), and others can leverage miniOrange as a central authentication source and enable the same MFA configuration.
Example : The user can log in to the machine using an account on any trusted domain like Active Directory domain-joined or Azure AD domain-joined, or using a Windows local account. This improves convenience and productivity.
Example : If an organization has non-domain joined machines, Admins can configure different MFA methods for devices allocated to admins or someone with privileged access than the ones allocated to local users.
Example : Organizations can reduce help-desk calls by enabling their users to reset their passwords for the first authentication factor via the self-service portal offered by the miniOrange MFA solution. It also enhances user experience by removing dependency.
Example: Users don’t need to know what IDP your organization is using and what security processes are running for secure authentication. miniOrange organizations to customize the login page by updating it with the company logo.
Example: For organizations with domain-joined machines, miniOrange can deploy the MFA solutions to all the systems at once with GPO push instead of deploying them one by one. This makes the process much faster and saves valuable time.

Our Other Identity & Access Management Products