Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×Connect with LDAPS using miniOrange guidelines to setup LDAP over SSL and establish a secure connection with LDAP Server. Secure your LDAP server connection between client and server application to encrypt the communication. In case of simple bind connection using SSL/TLS is recommended to secure the authentication as simple bind exposes the user crendetials in clear text.
1.1: Install "Active Directory Certificate Services" role through Server Manager roles.
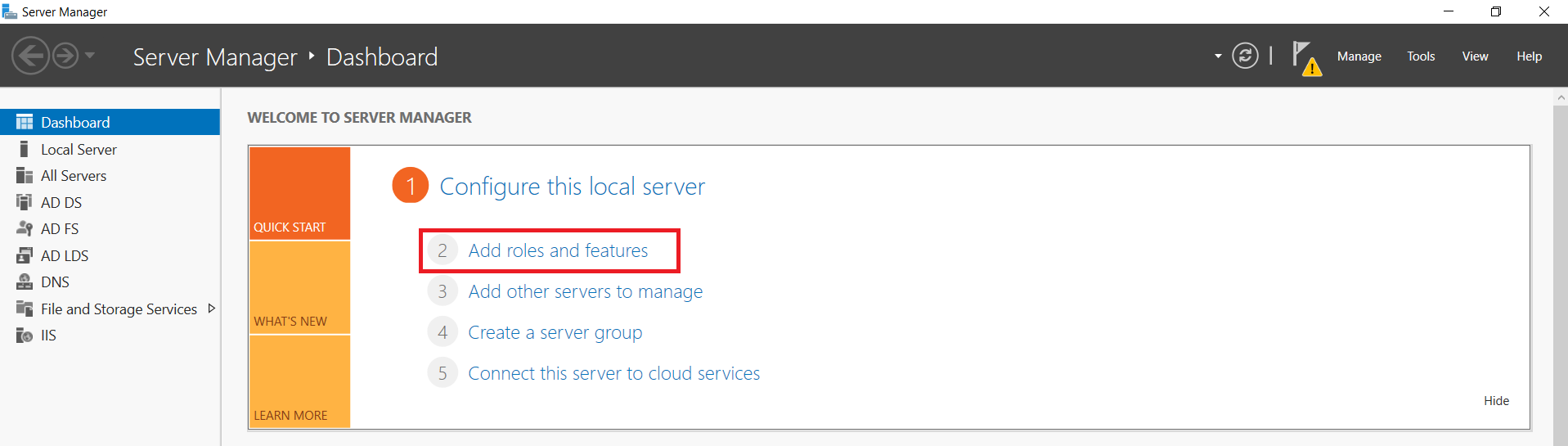
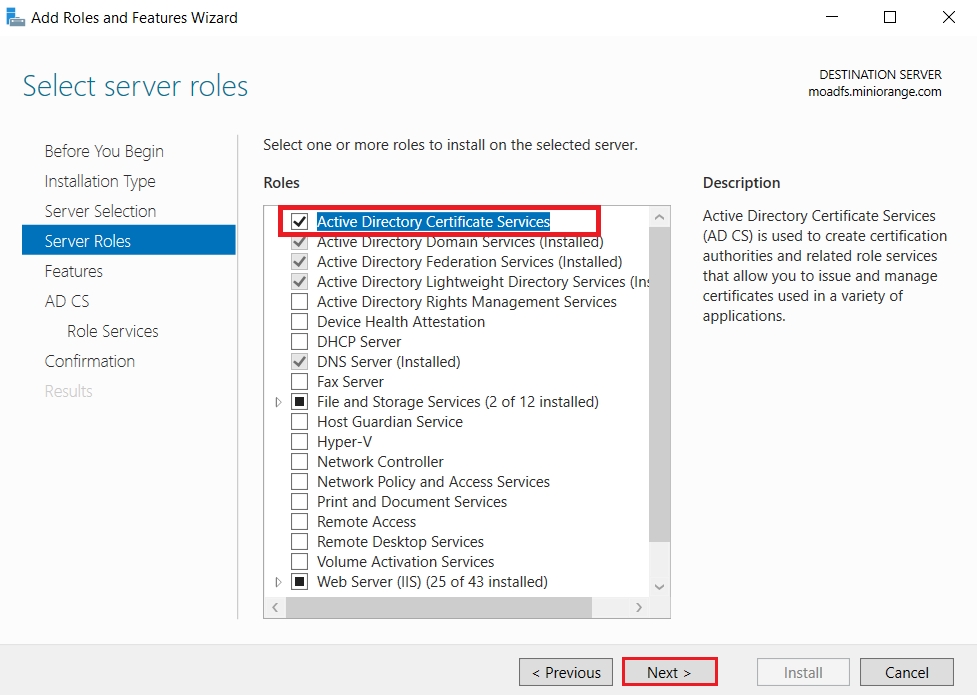
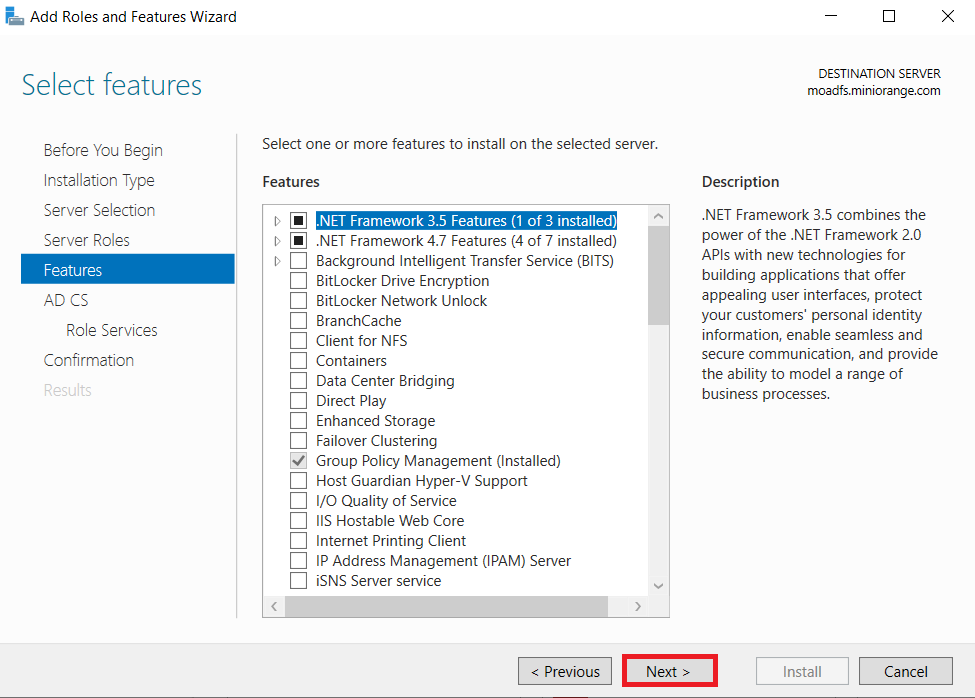
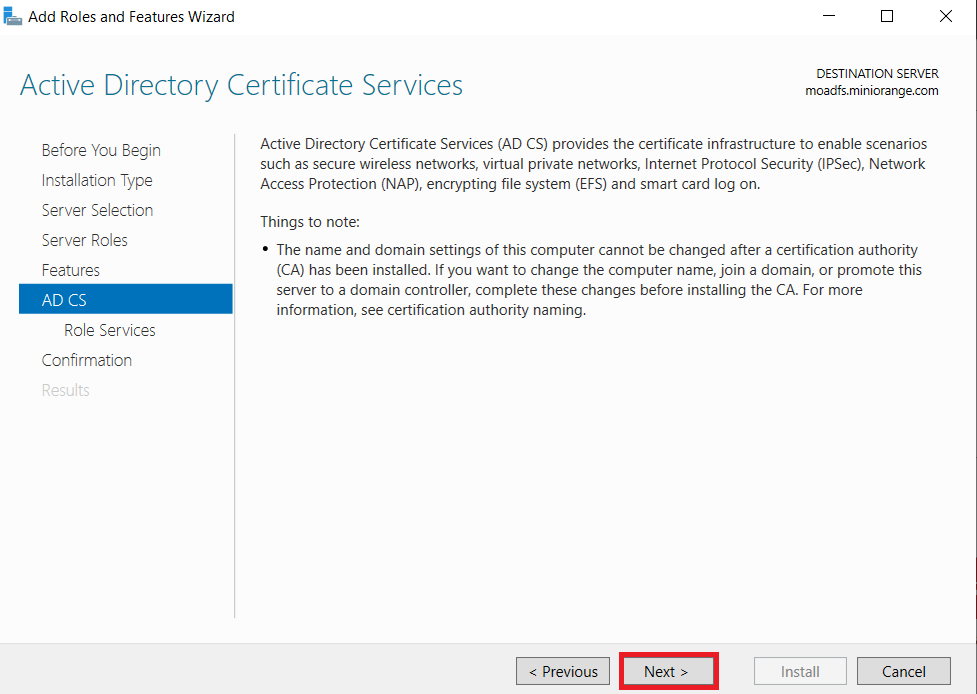
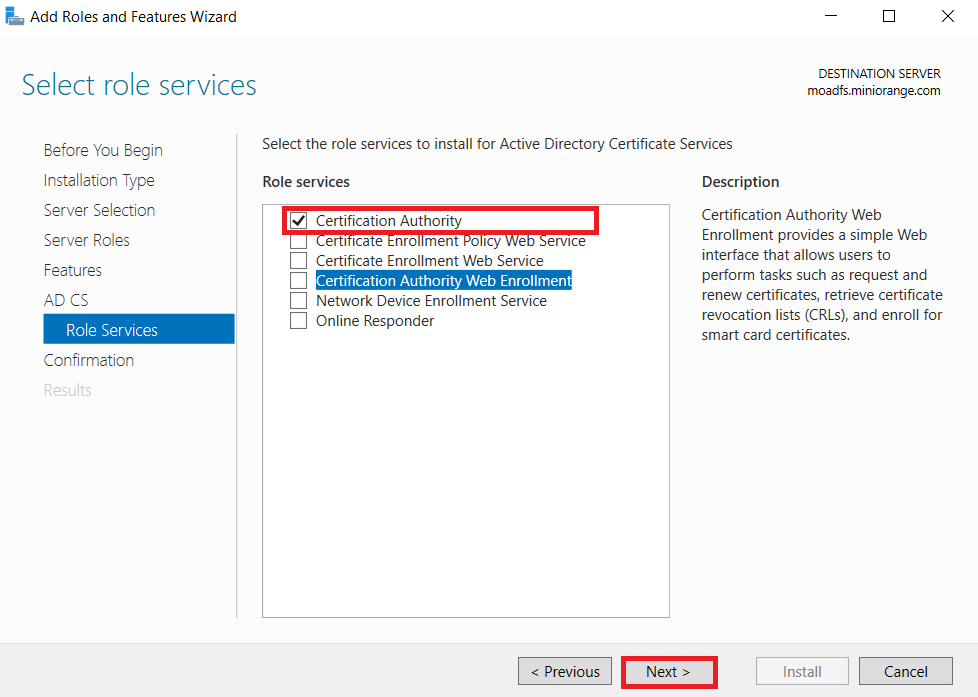
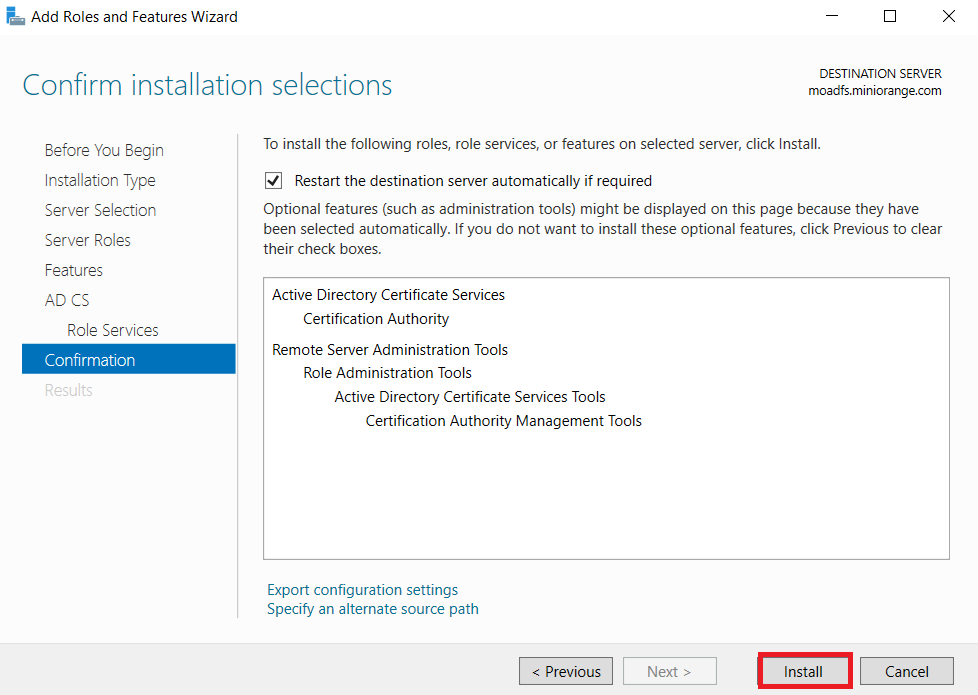
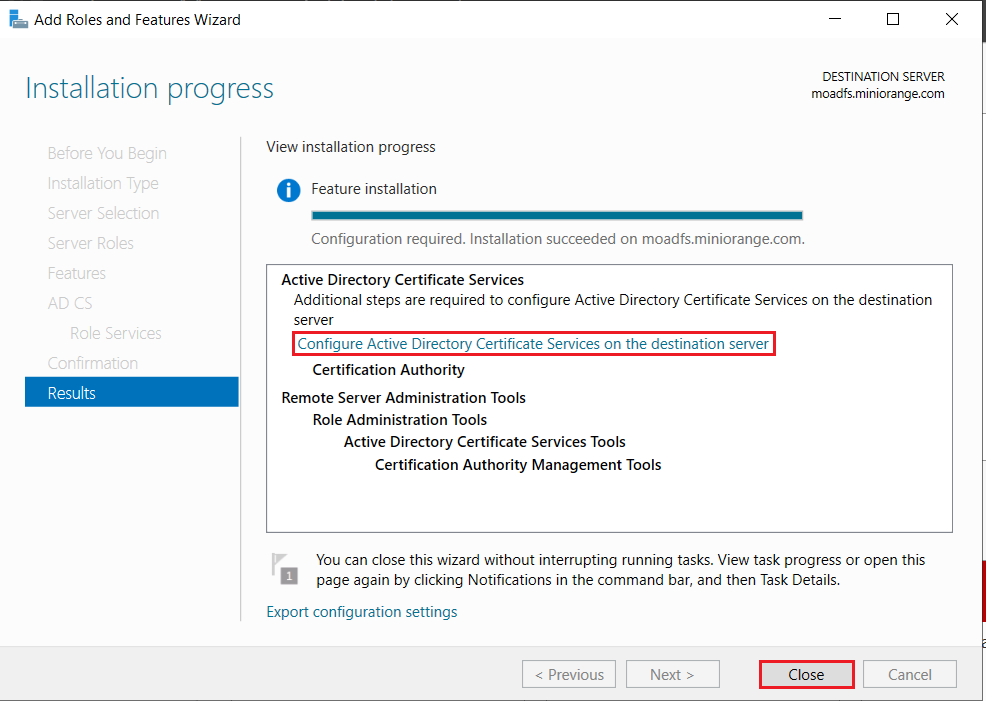
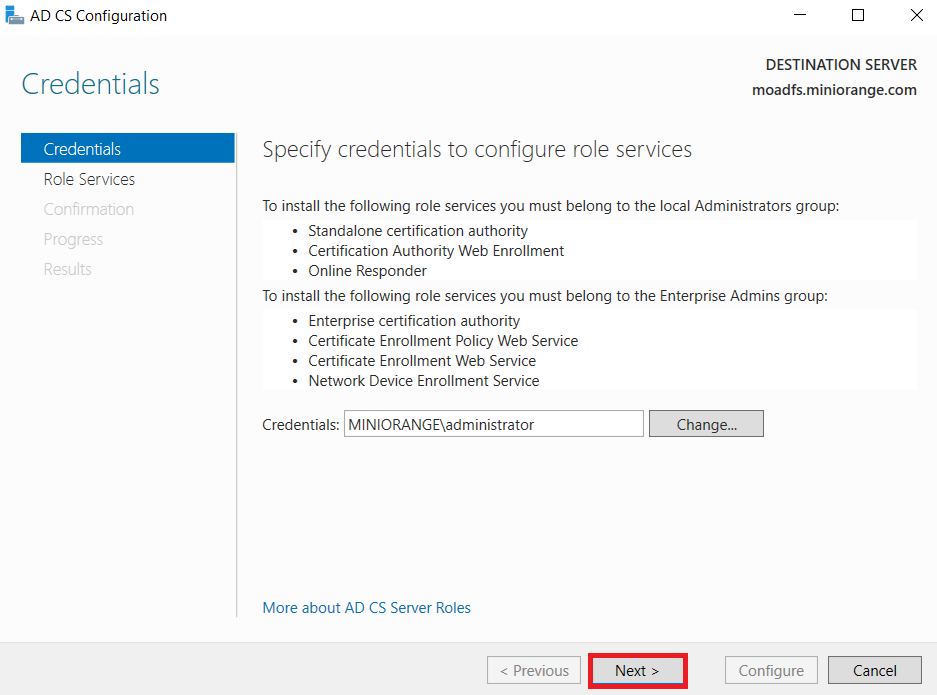
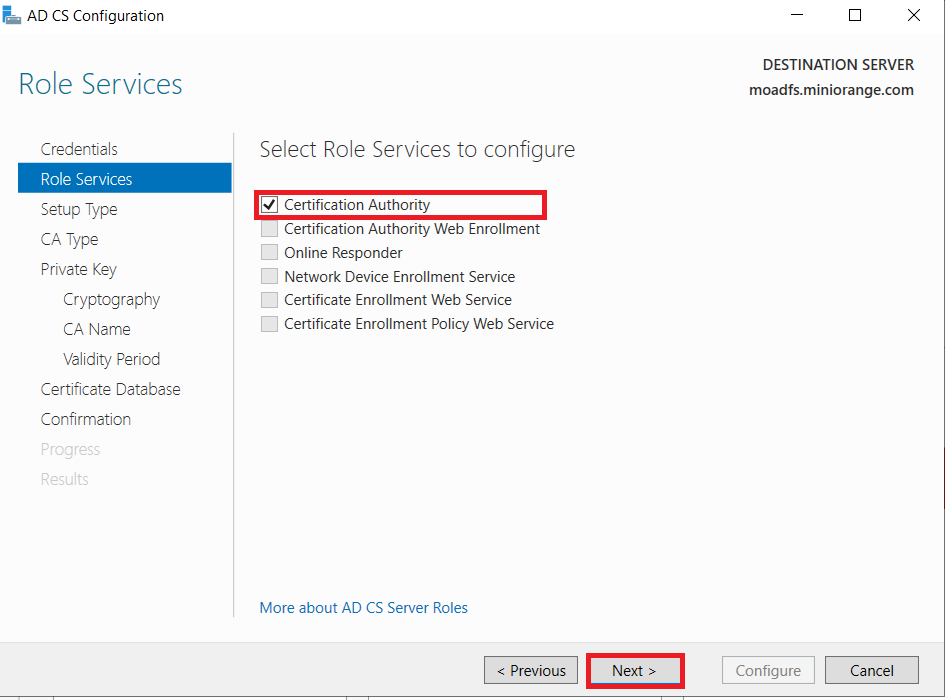
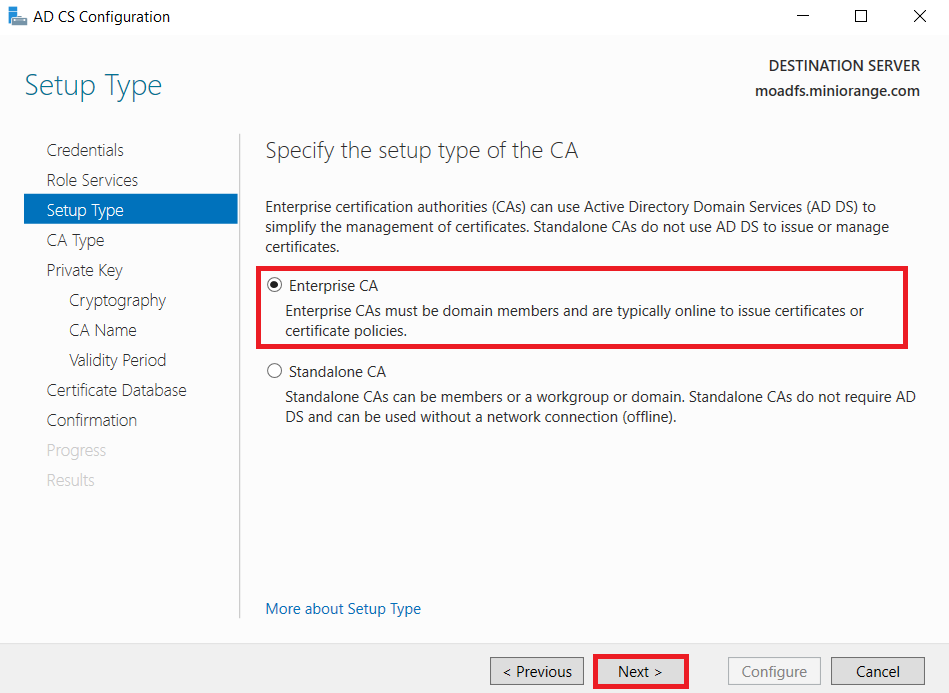
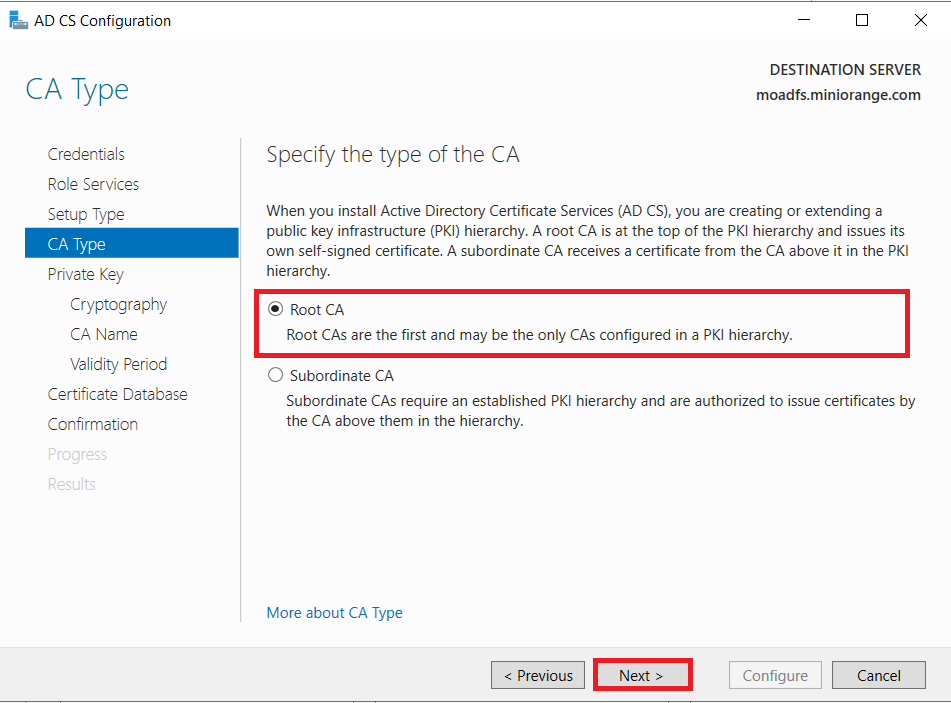
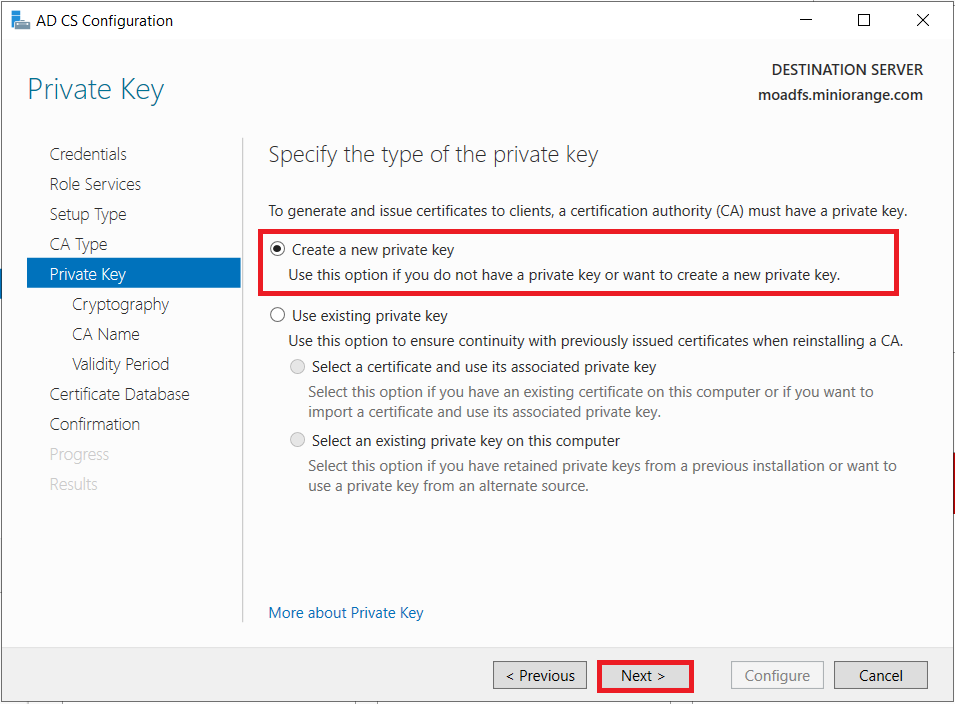
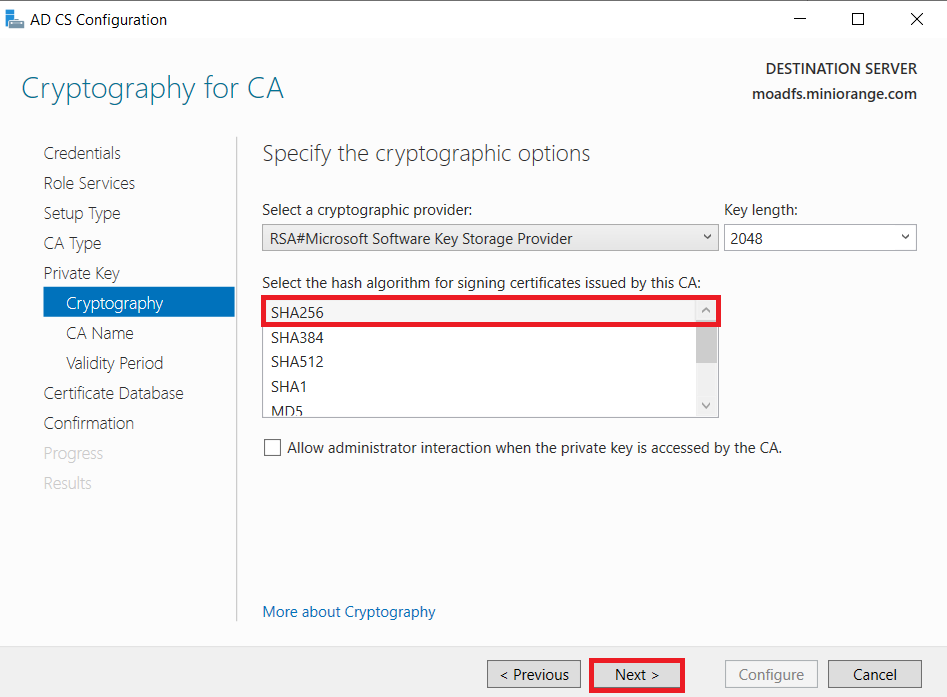
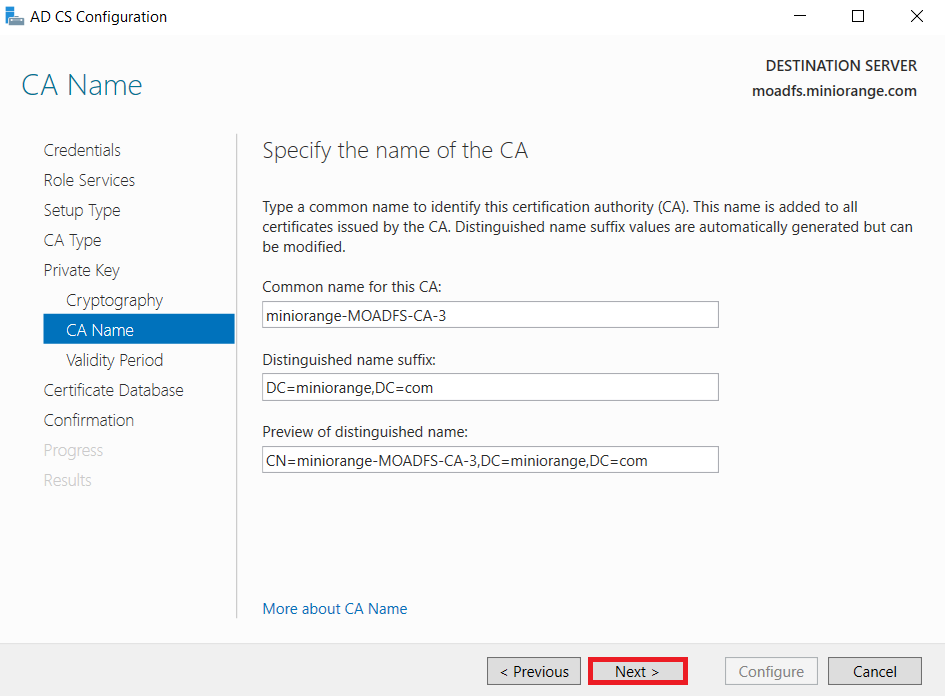
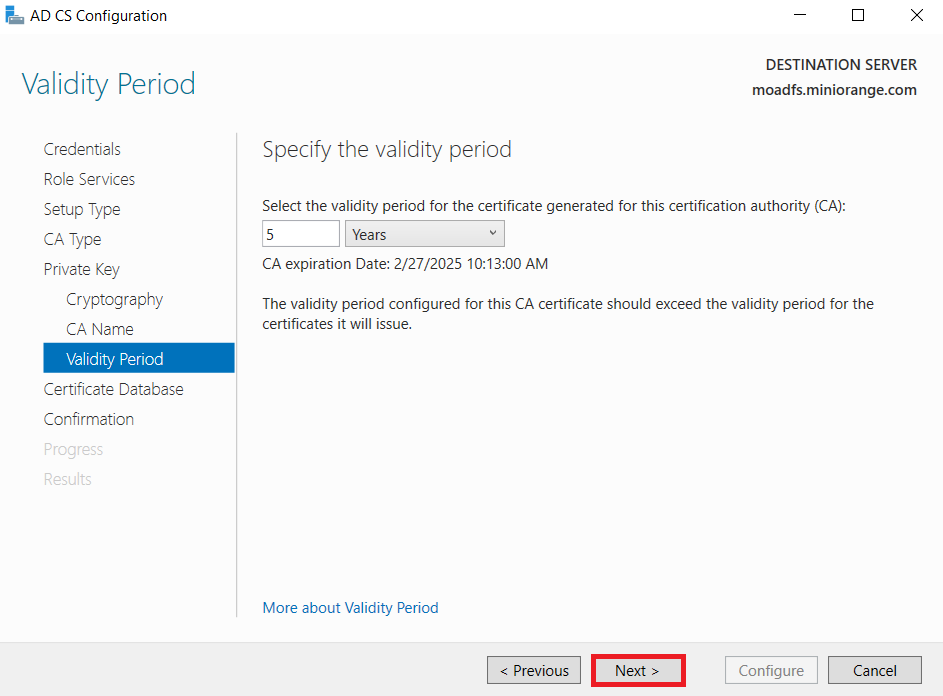
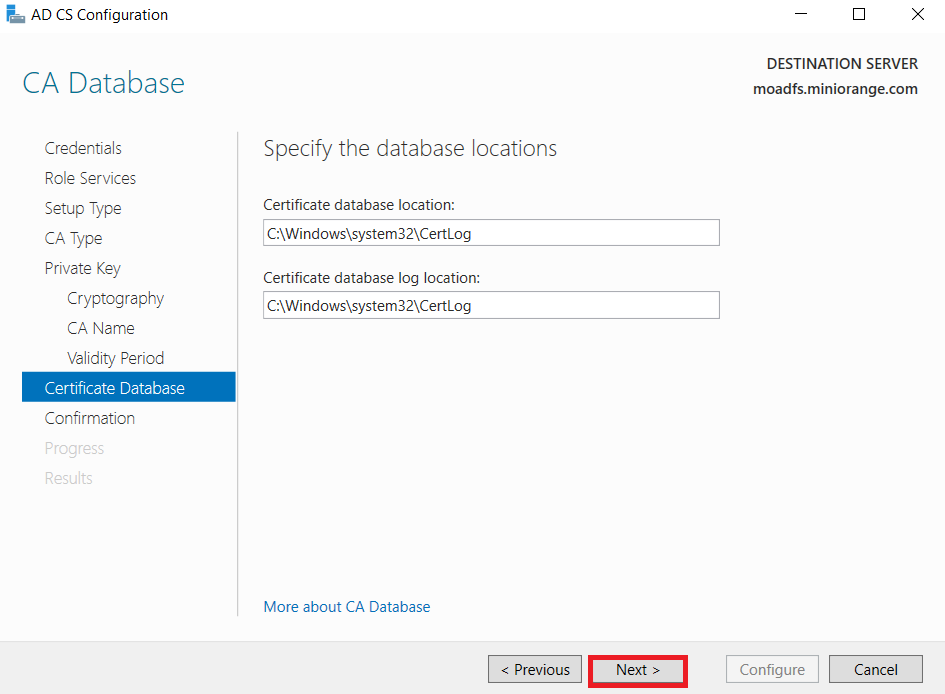
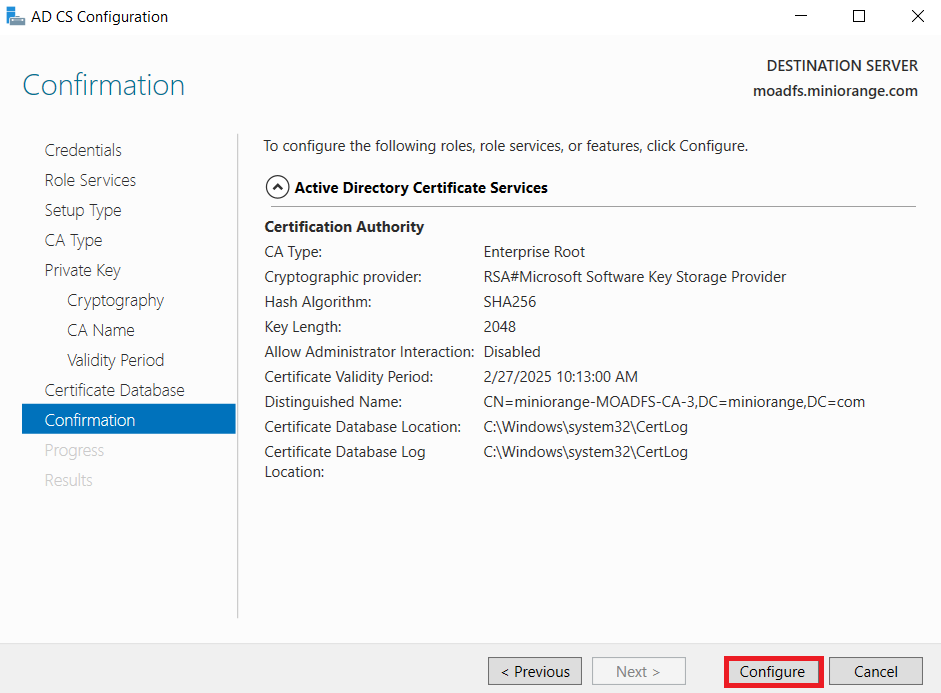
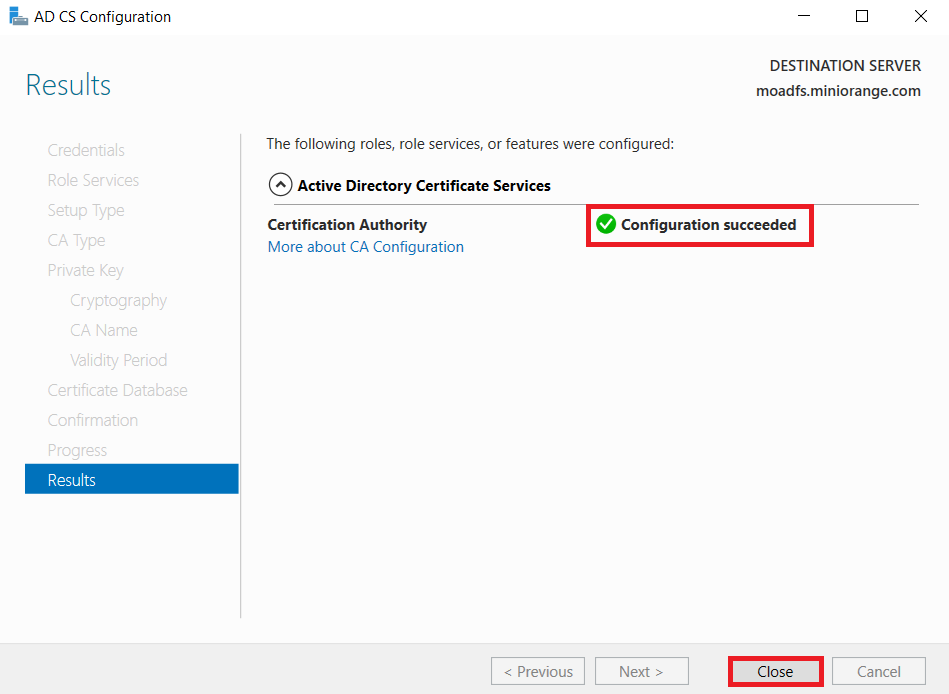
1.2: Create certificate template
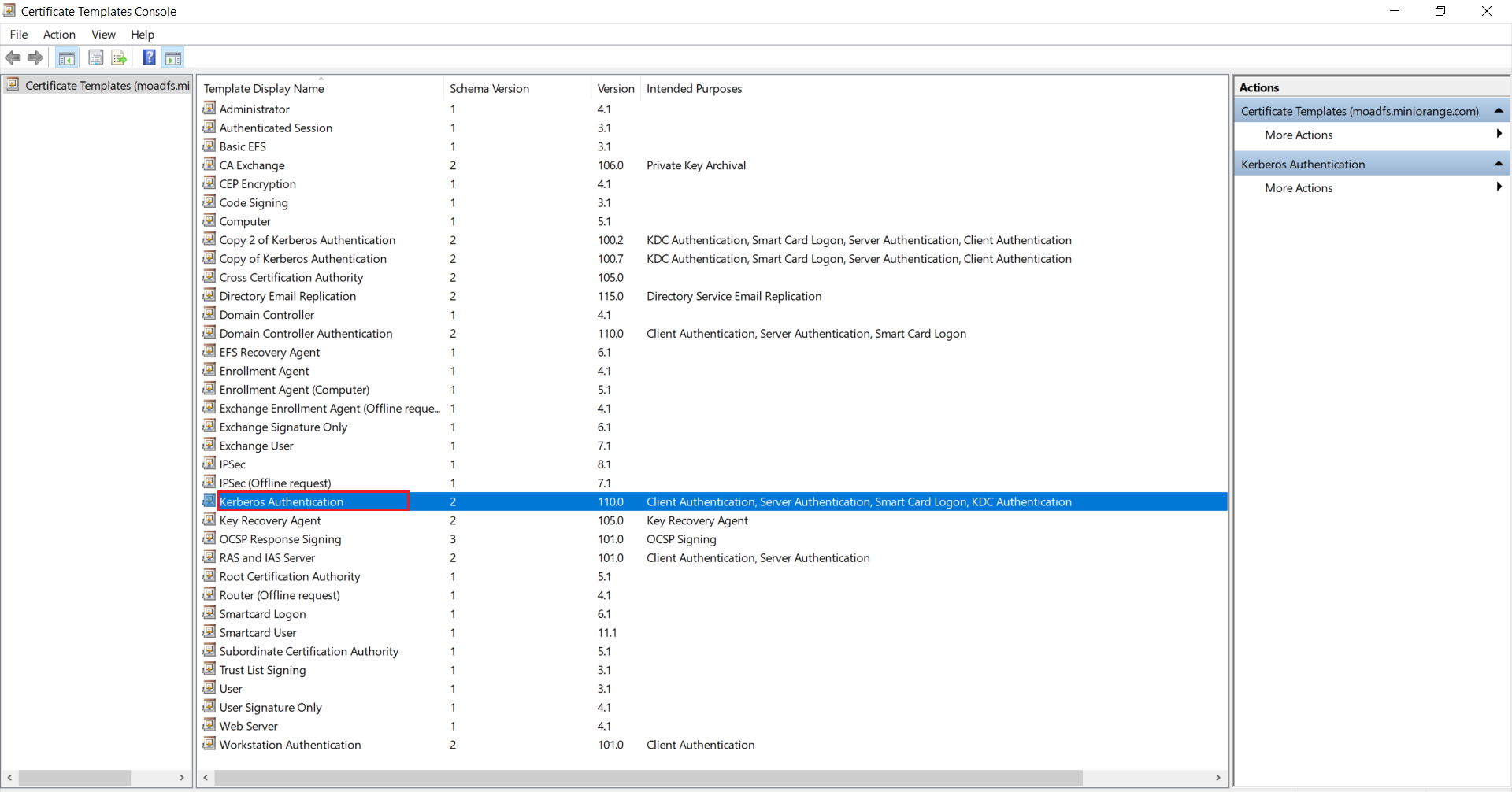
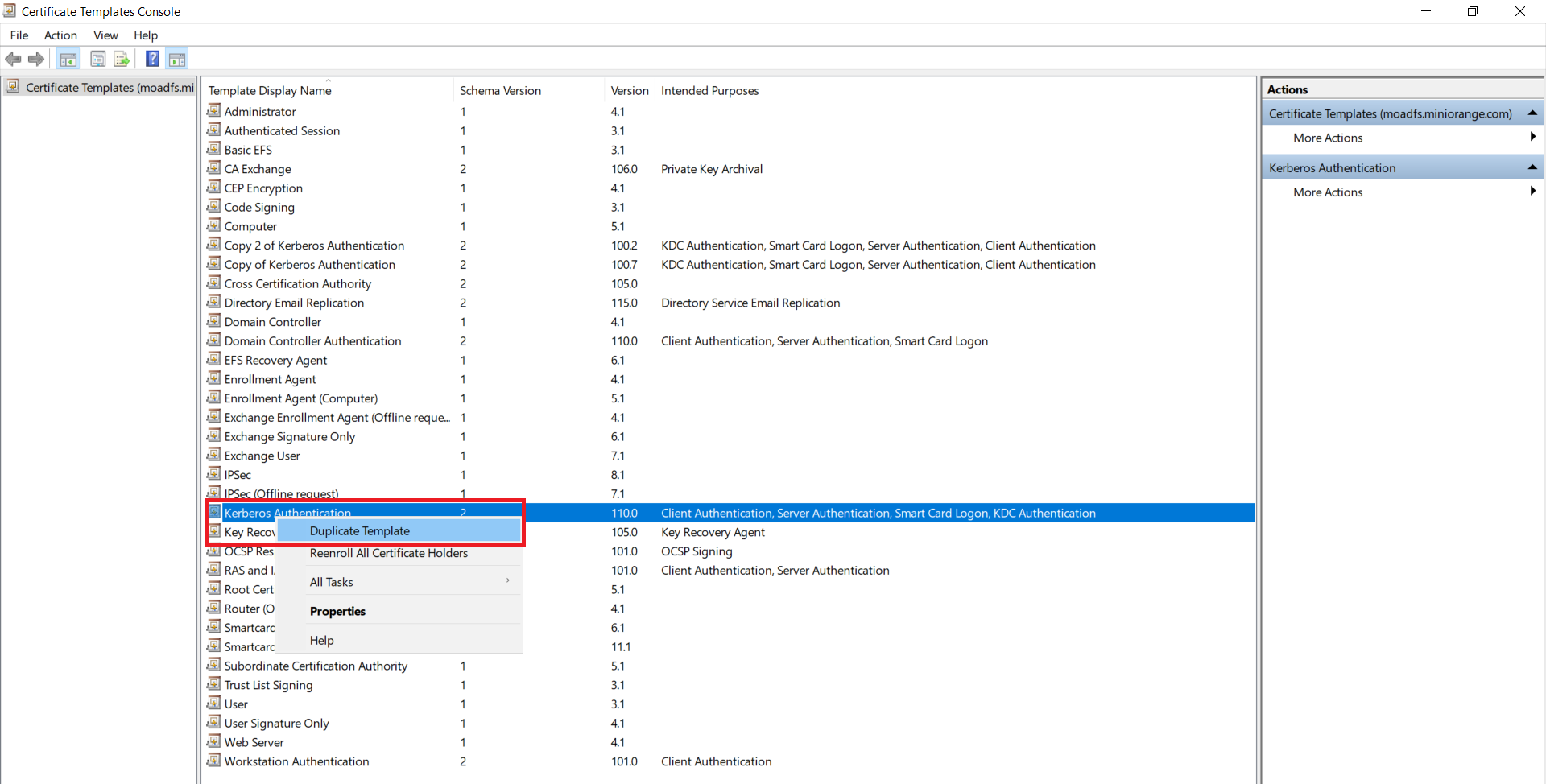
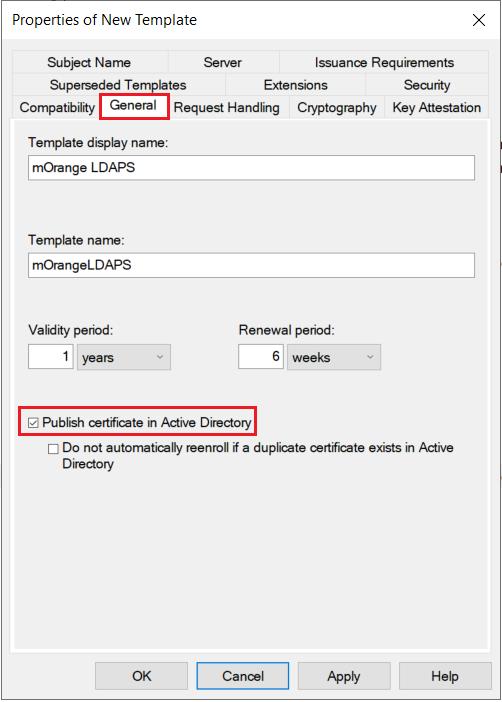
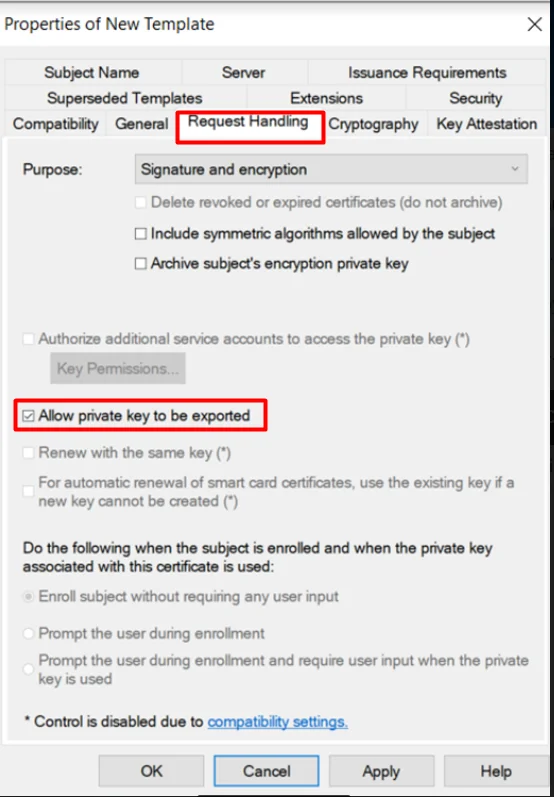
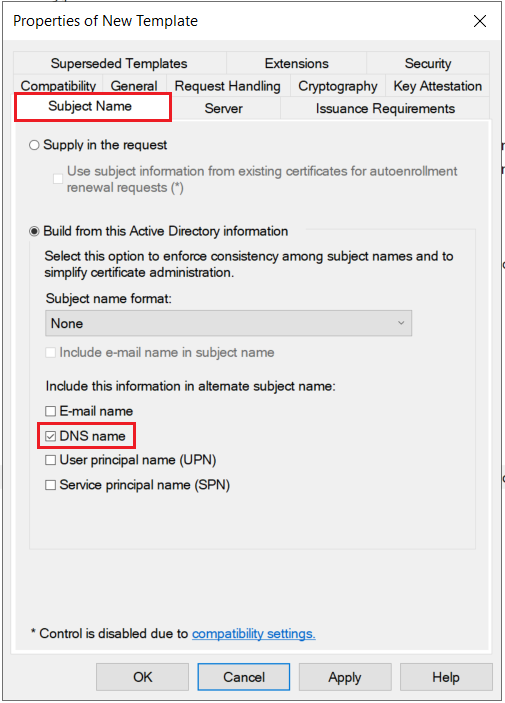
1.3: Issue certificate template
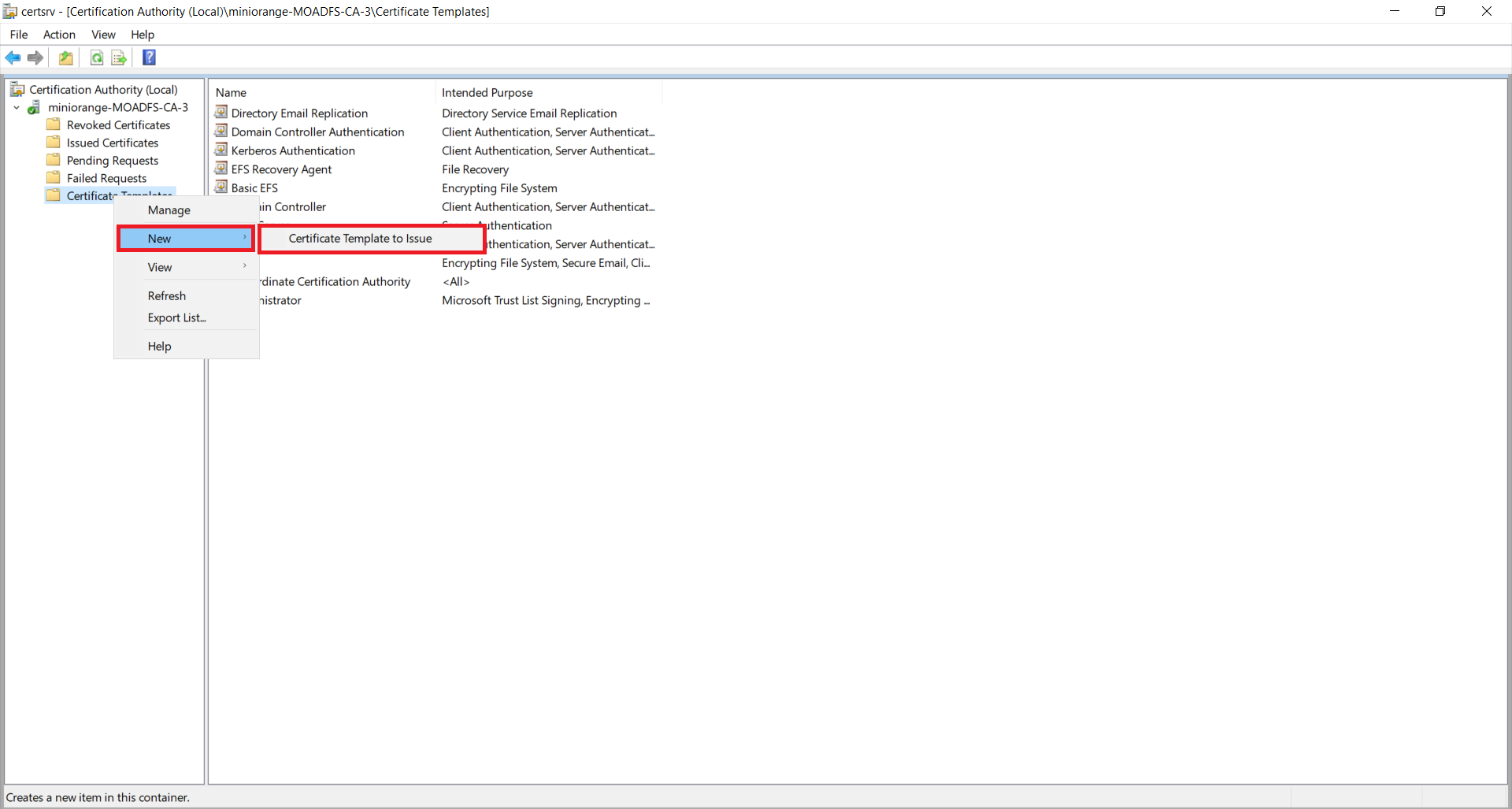
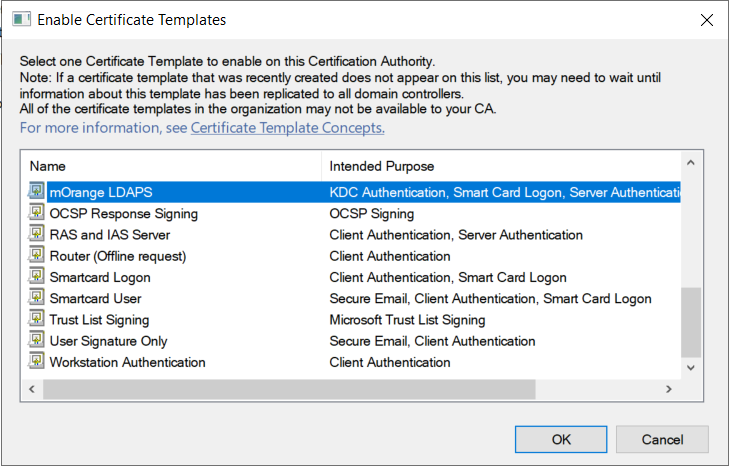
1.4: Request new certificate for created certificate template
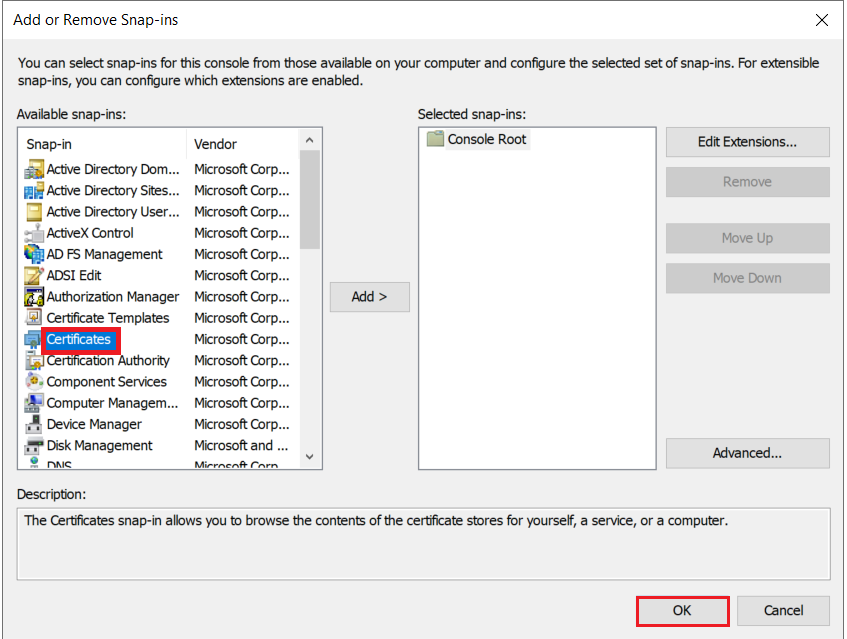
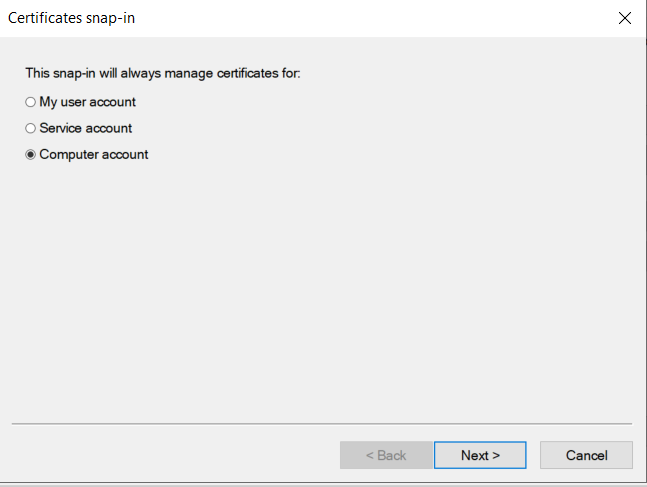
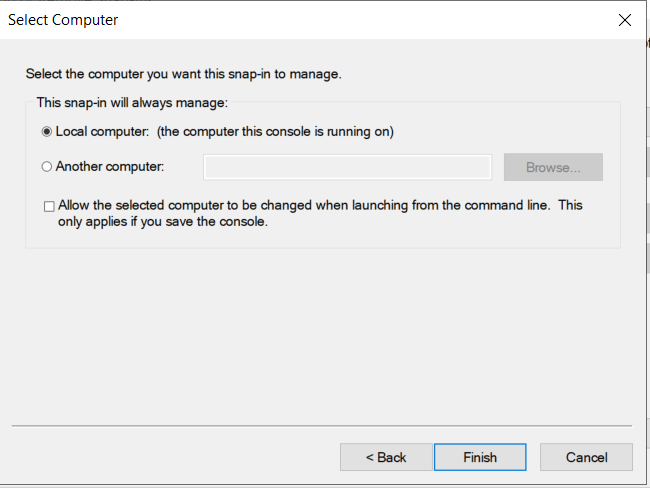
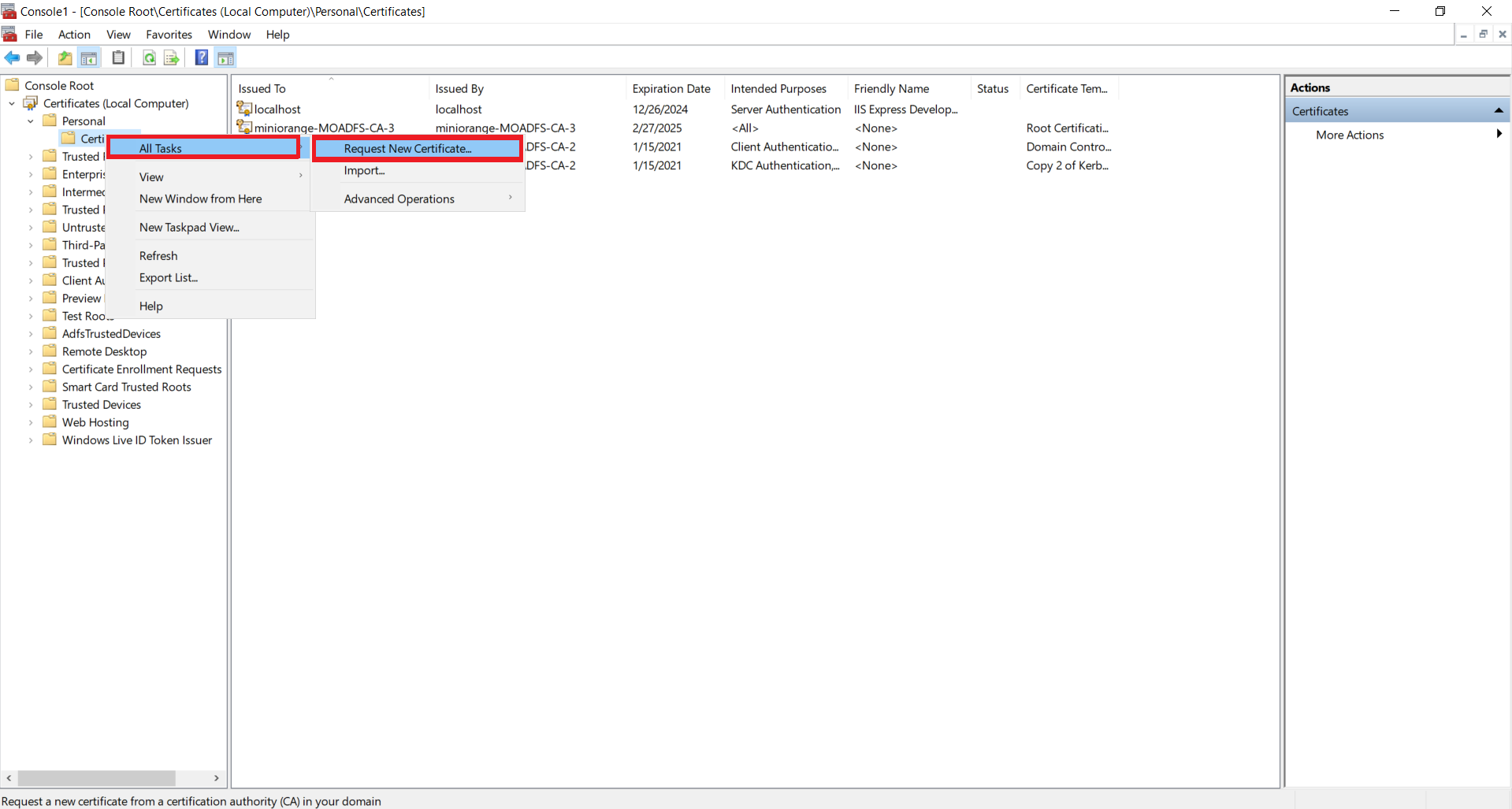
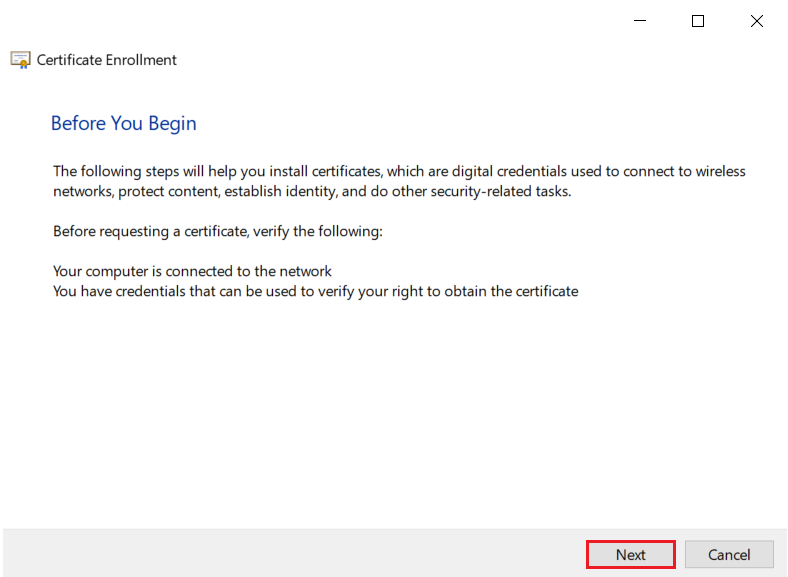
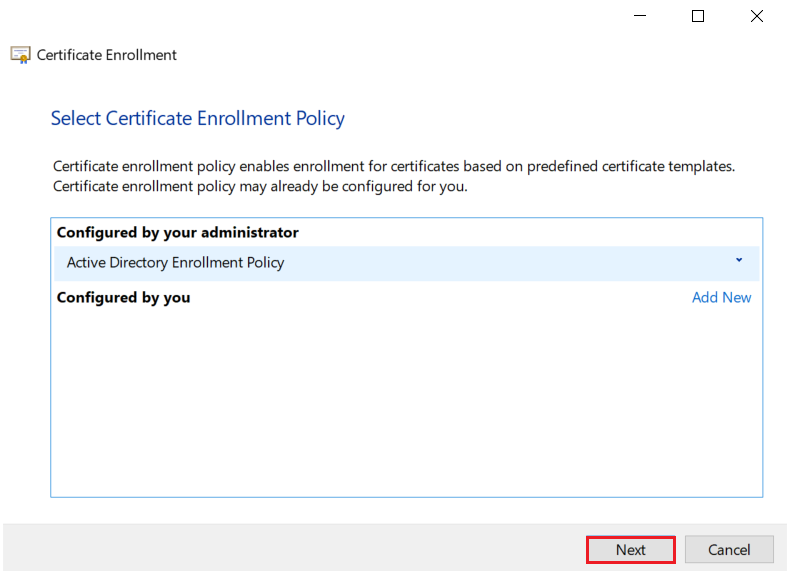
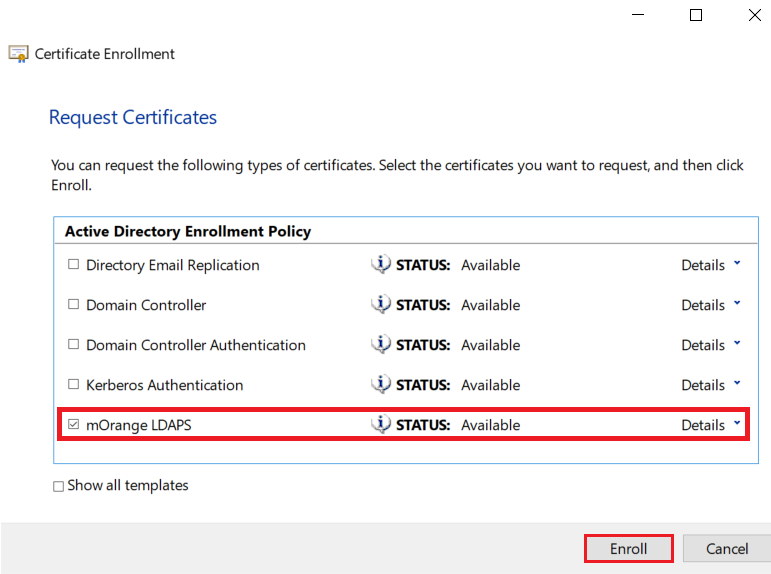
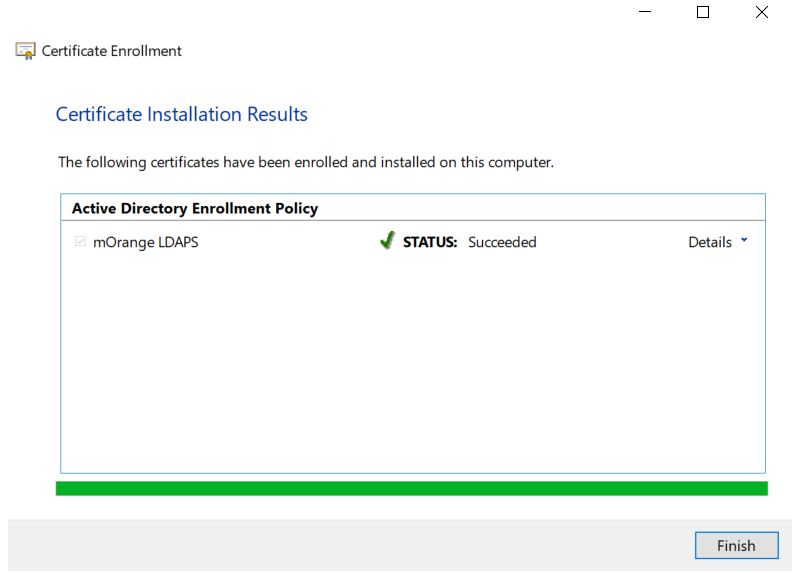
1.5: Export the created certificate
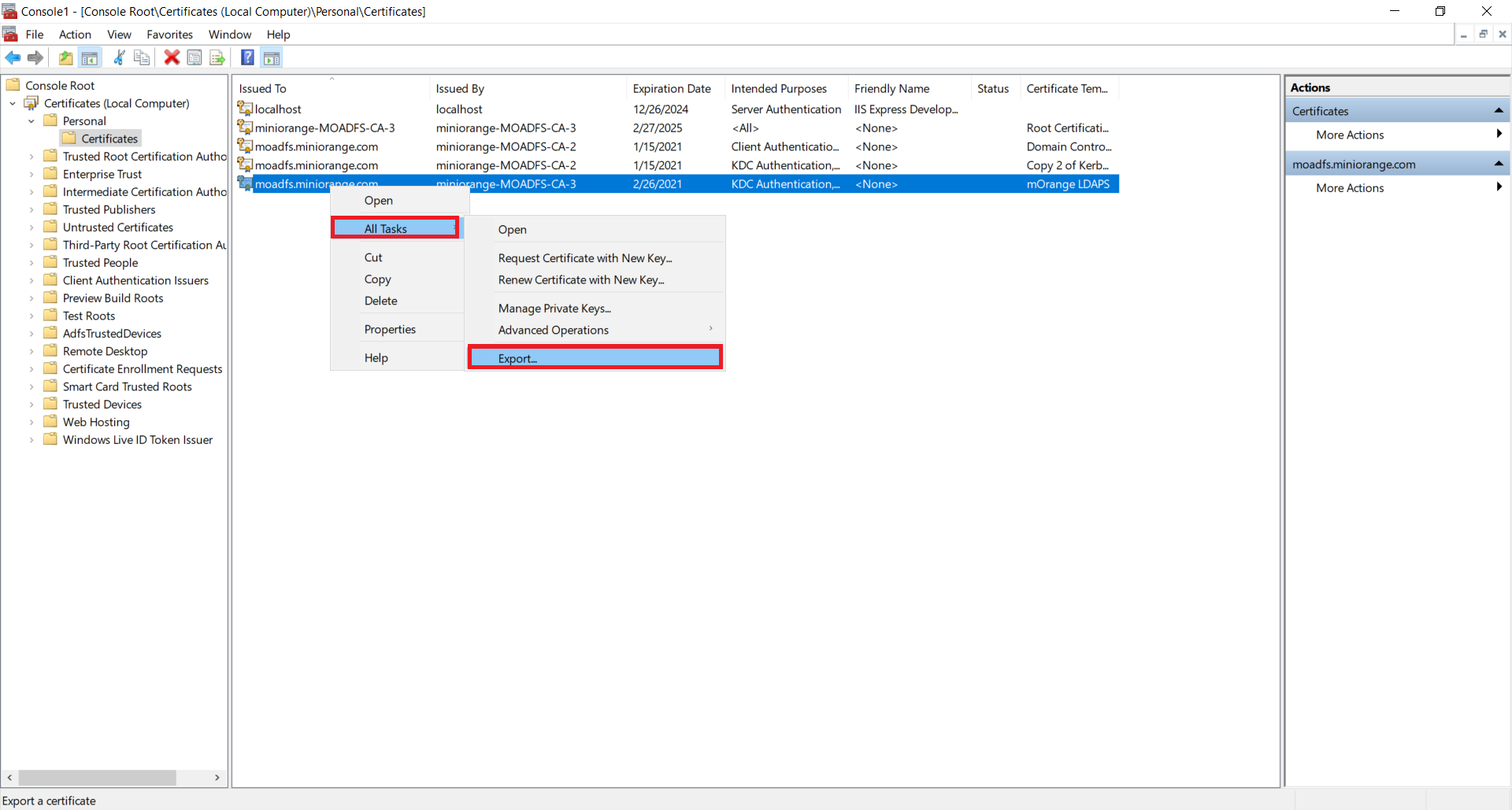

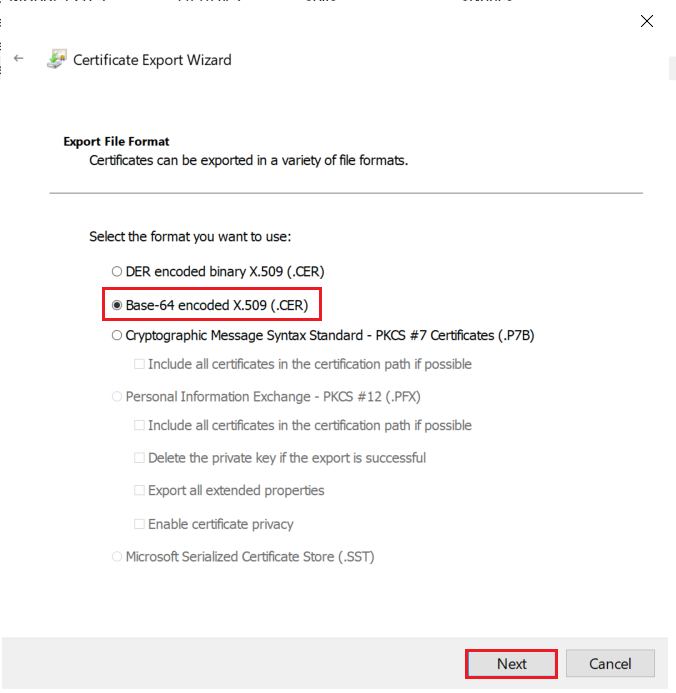
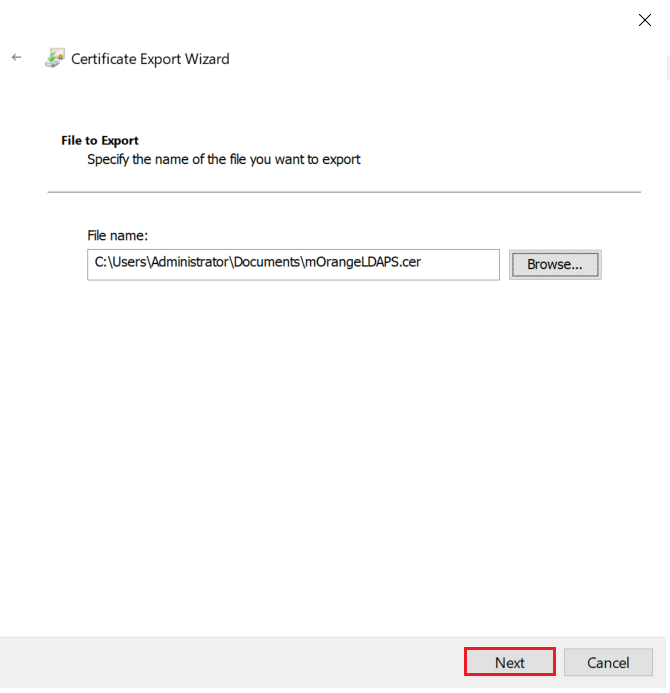
2.1: Convert Certificate Format and Install the Certificate using OpenSSL
C:\openssl\openssl x509 -in mOrangeLDAPS.cer -out mOrangeLDAPS.pemTLS_CACERT C:\openldap\sysconf\mOrangeLDAPS.pemsudo apt-get install opensslyum install openssl/openssl x509 -in mOrangeLDAPS.cer -out mOrangeLDAPS.pemTLS_CACERT /etc/openldap/mOrangeLDAPS.pem2.2: Install certificate in JAVA Keystore.
keytool -importcert -alias "mOrangeLDAPS"
-keystore "C:\Program Files\Java\jre1.8.0_231\lib\security\cacerts"
-file "C:\Users\Administrator\Documents\mOrangeLDAPS.cer"
keytool -importcert -alias "mOrangeLDAPS"
-keystore "/usr/java/jdk1.8.0_144/jre/lib/security/cacerts"
-file "/home/mOrangeLDAPS.cer"

Our Other Identity & Access Management Products