Need Help? We are right here!
Need Help? We are right here!
Thanks for your Enquiry.
If you don't hear from us within 24 hours, please feel free to send a follow-up email to info@xecurify.com
Search Results:
×miniOrange provides a ready to use solution for Thinkific. This solution ensures that you are ready to roll out secure access to Thinkific using Okta within minutes. Okta as an IDP ( Identity Provider) helps you log in into Thinkific.
miniOrange provides user authentication from various external sources, which can be Directories (like ADFS, Microsoft Active Directory, Azure AD, OpenLDAP, Google, AWS Cognito etc), Identity Providers (like Shibboleth, Ping, Okta, OneLogin, KeyCloak), Databases (like MySQL, Maria DB, PostgreSQL) and many more.
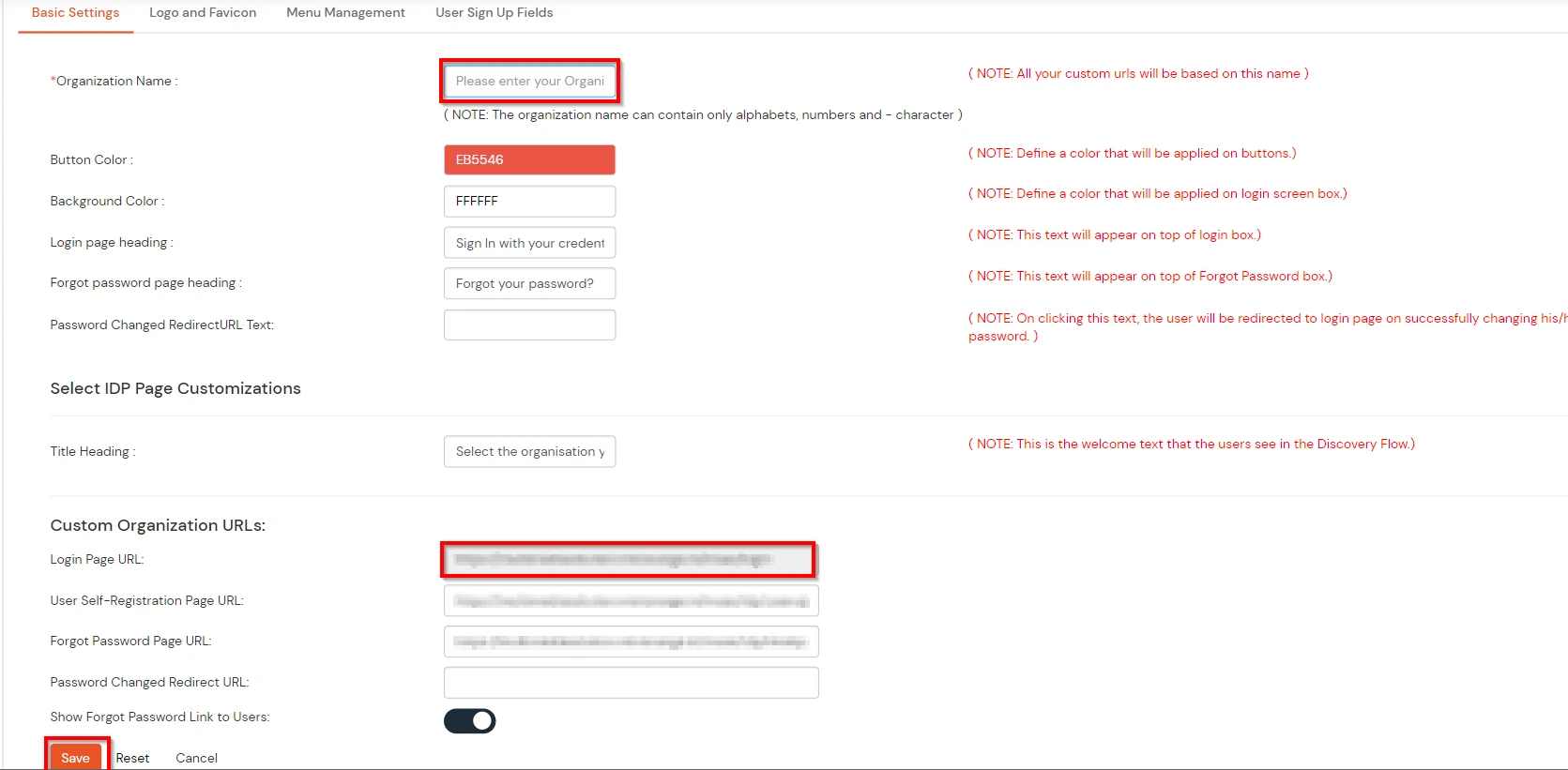
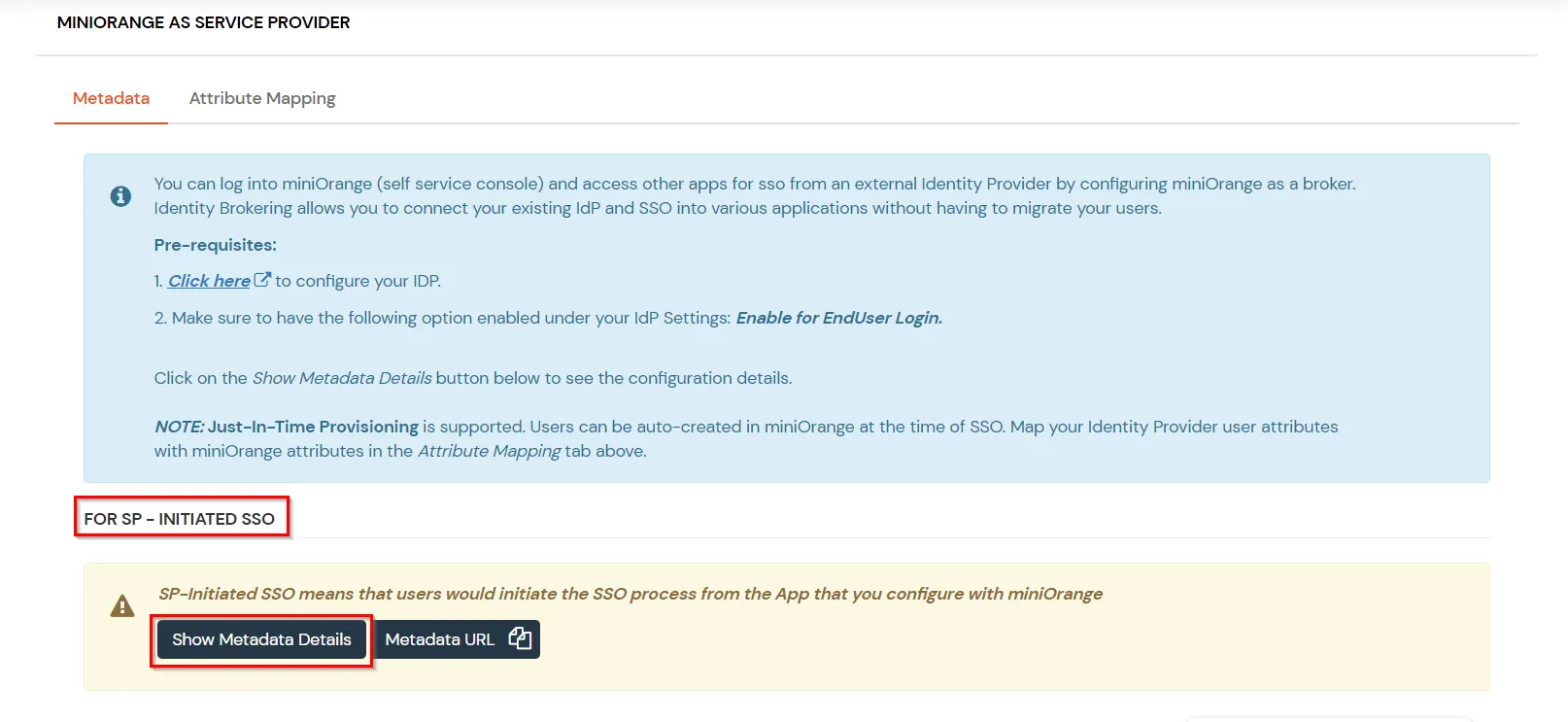
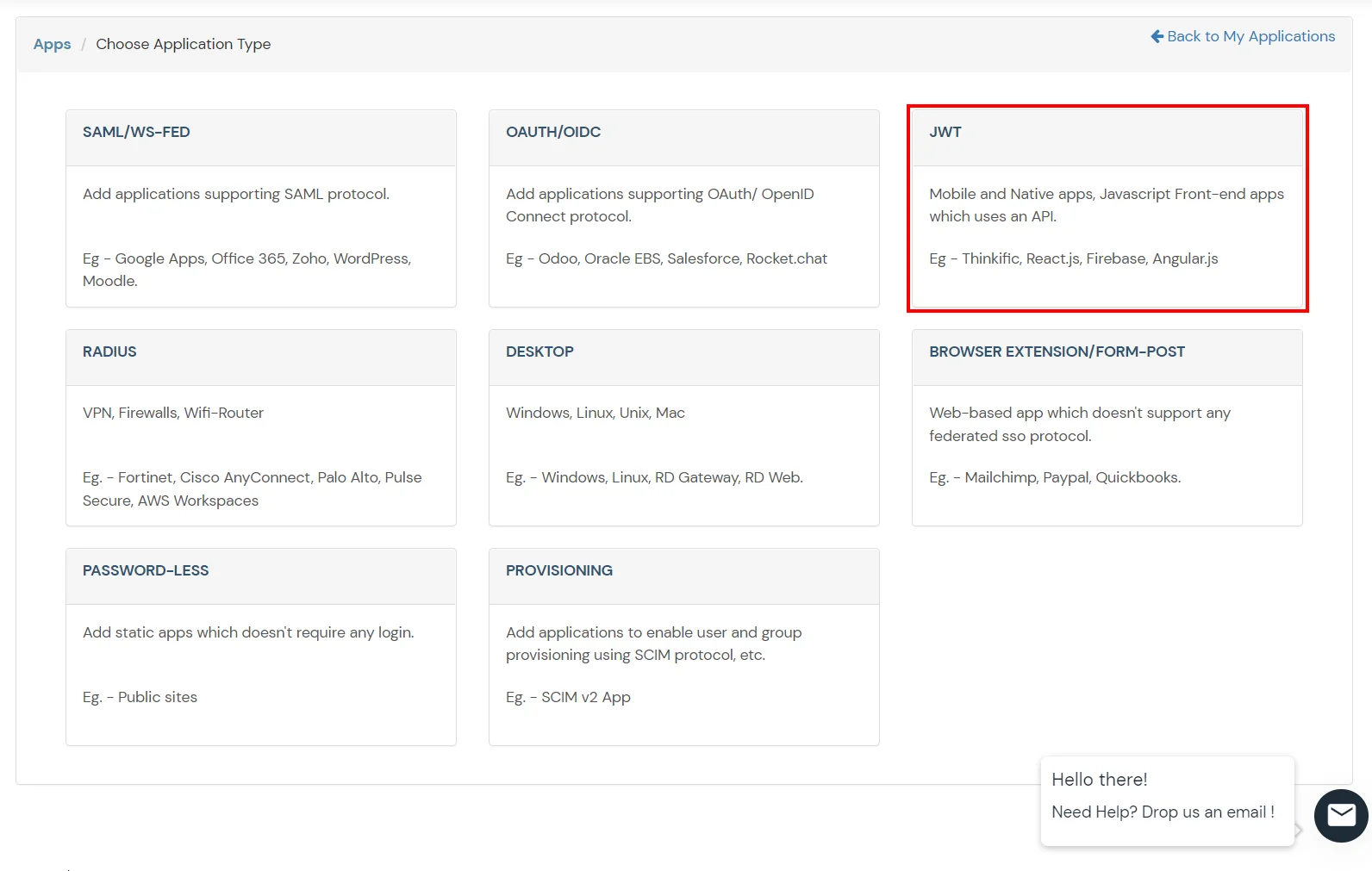
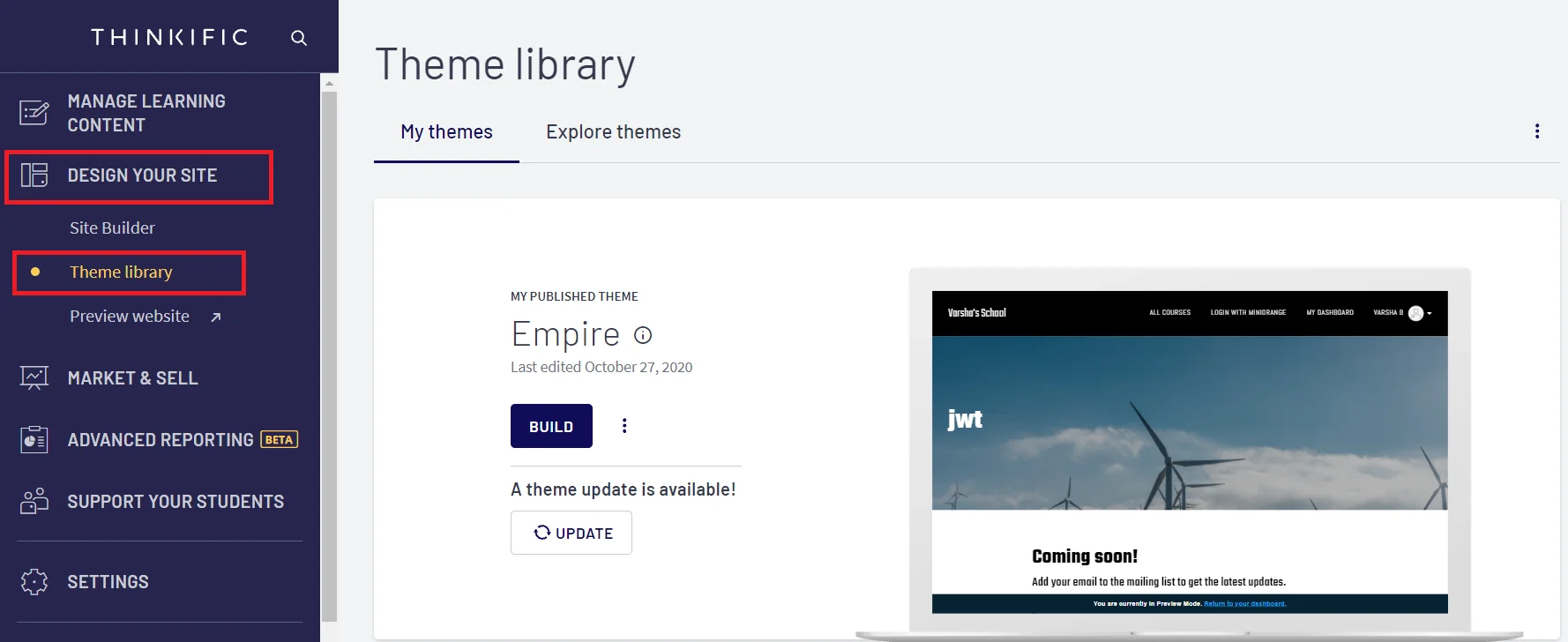
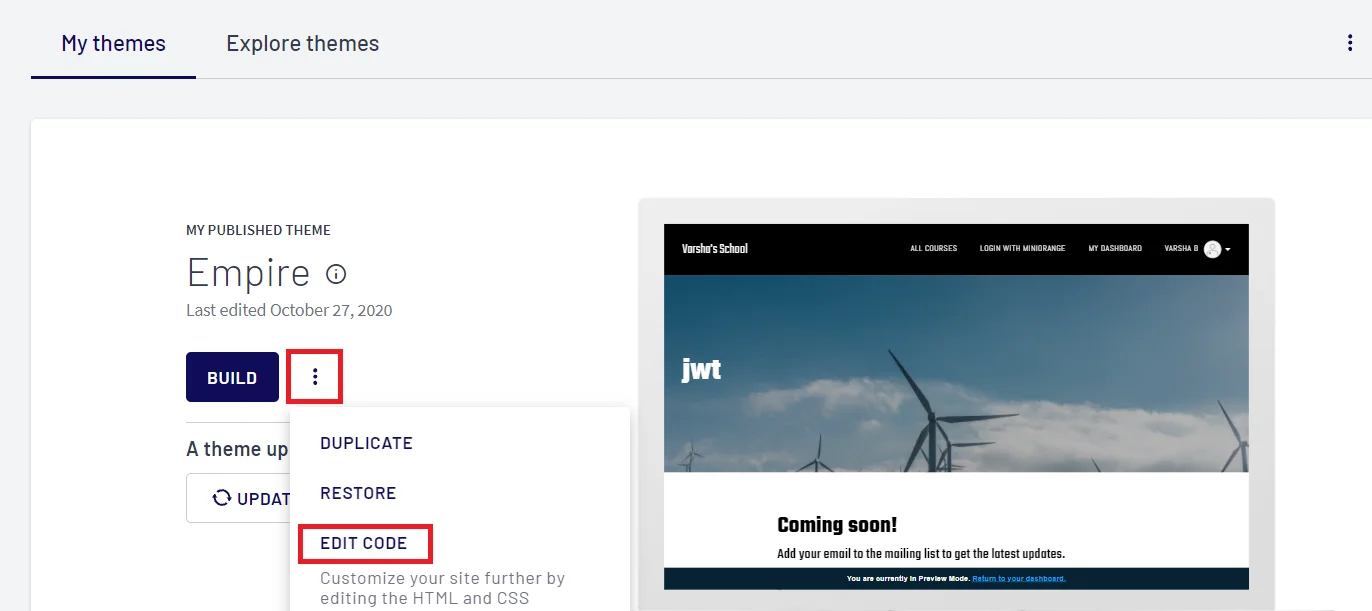
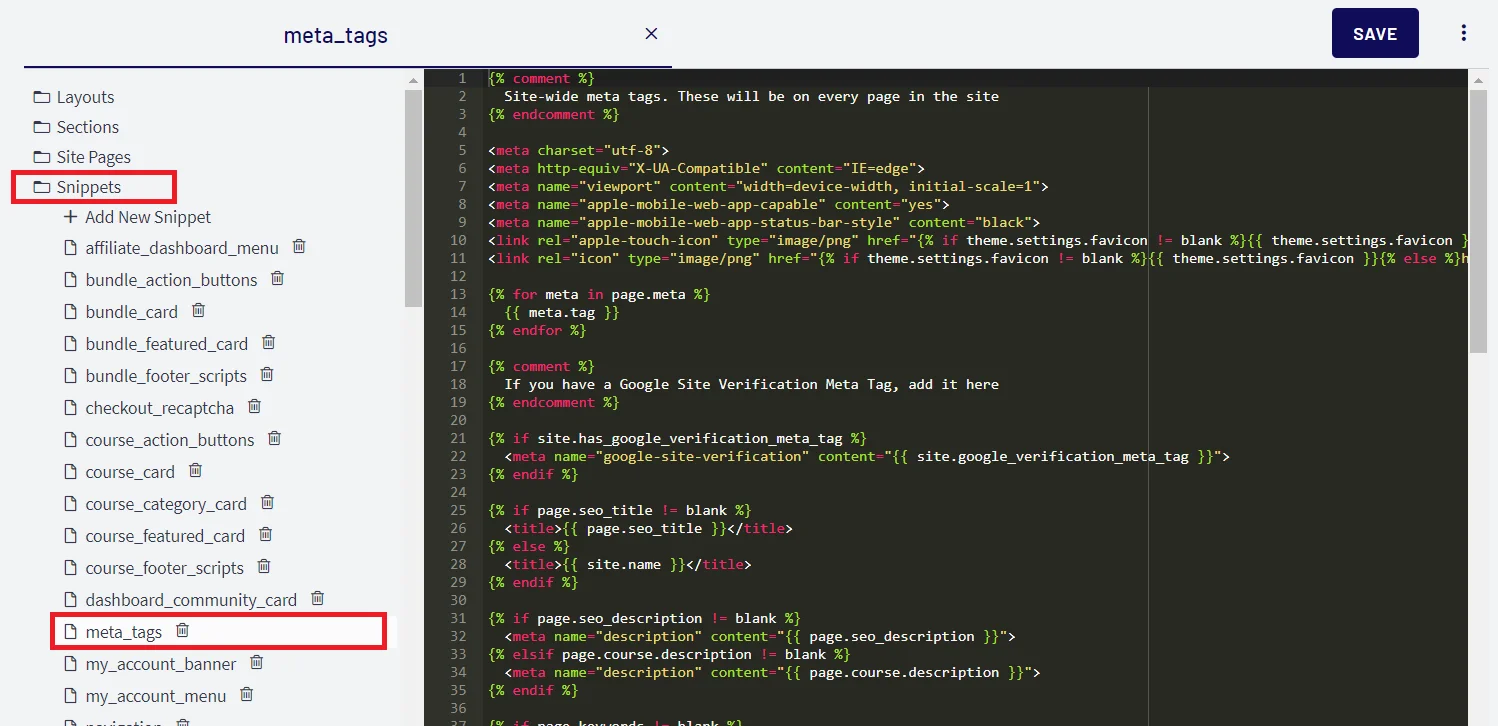
Obtain the following information from Thinkific.
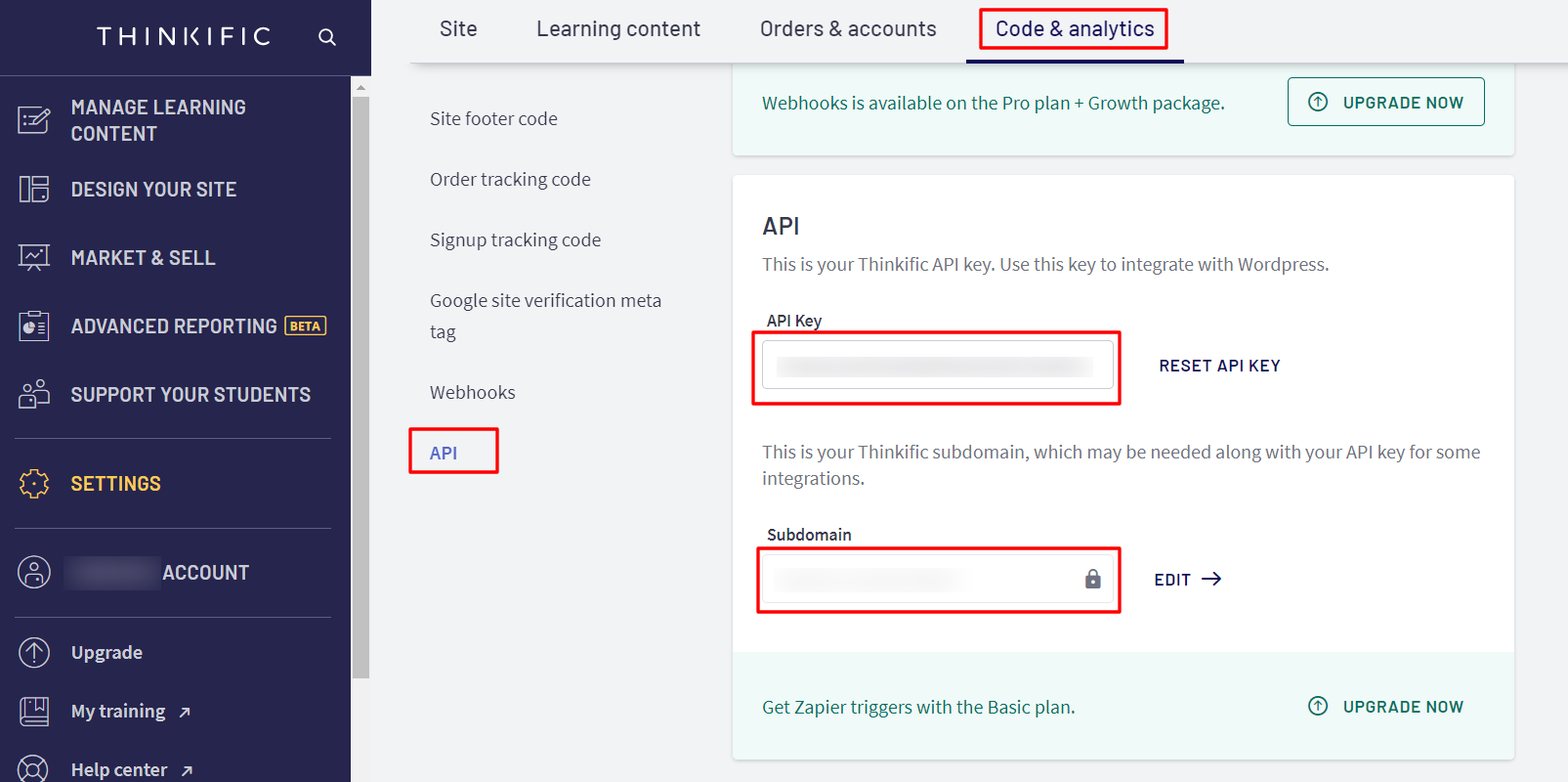
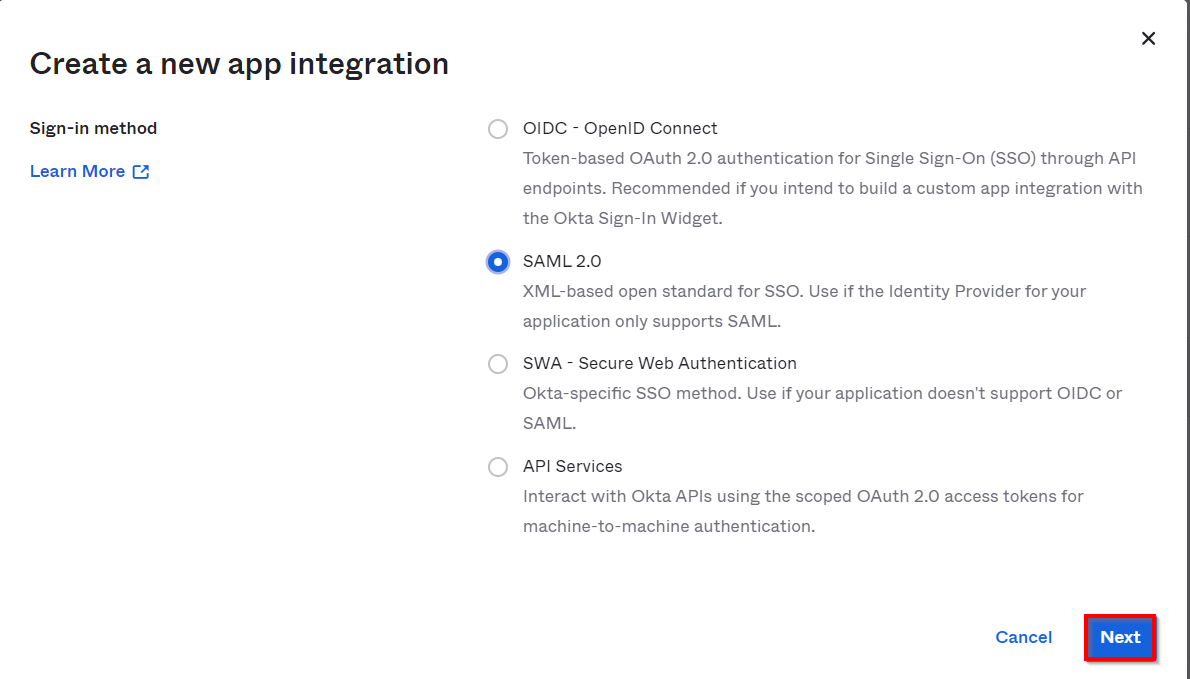
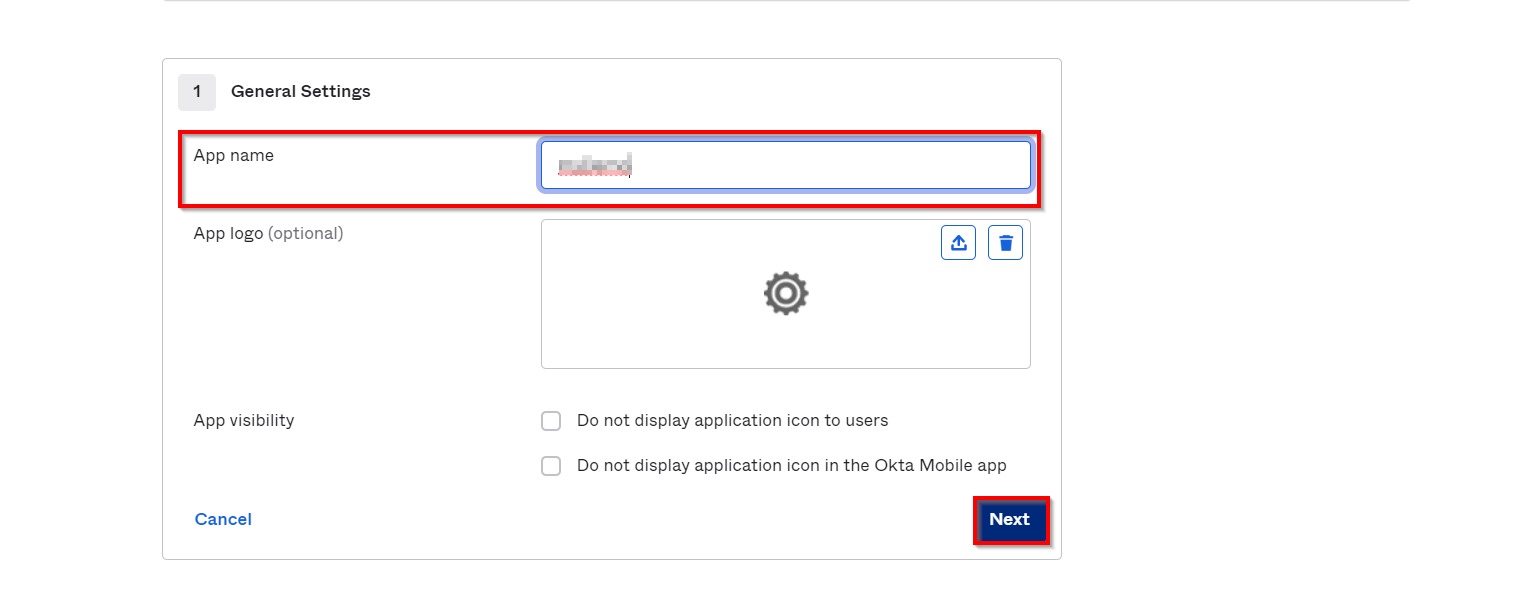
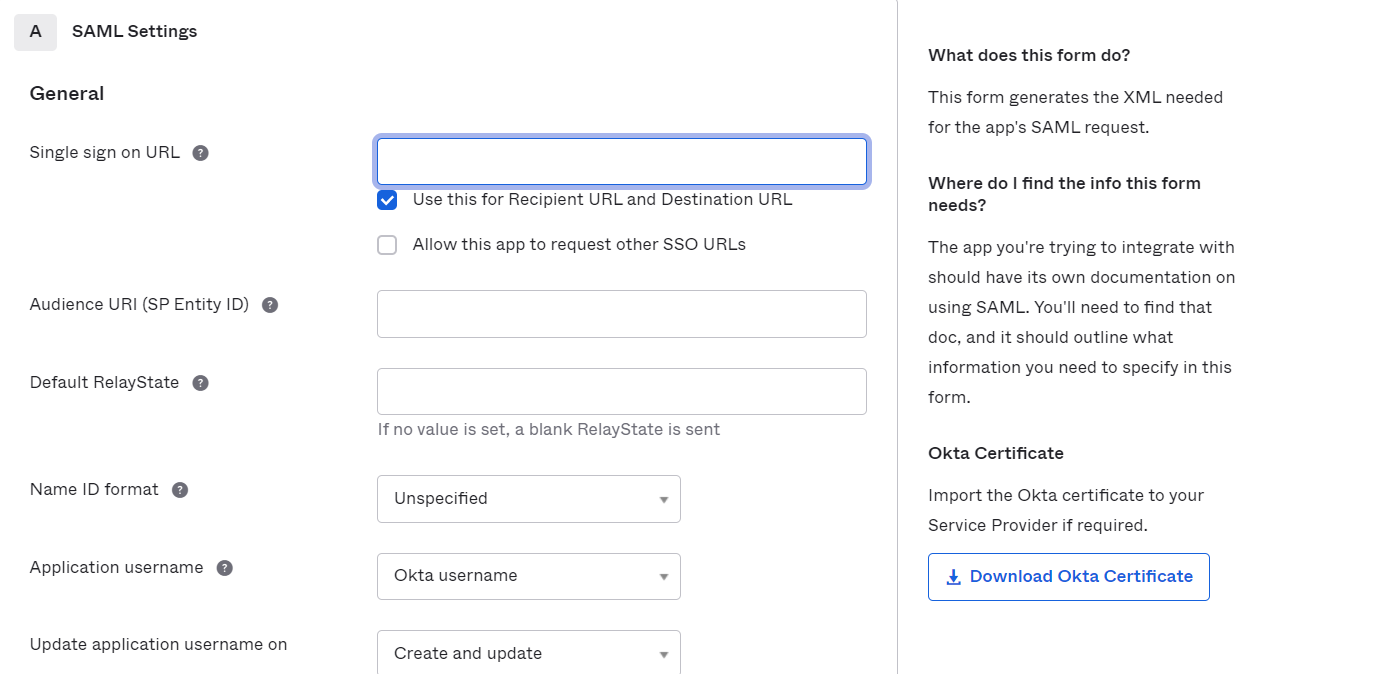
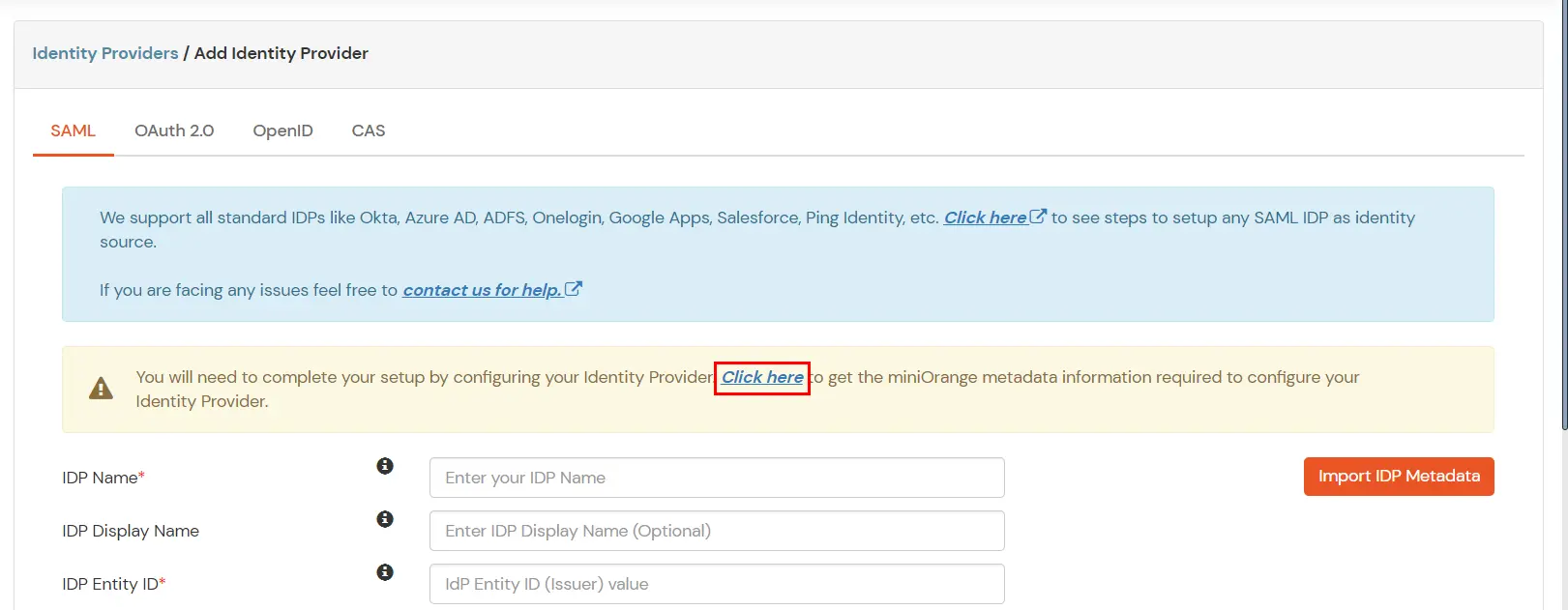
| Single sign on URL | ACS URL copied from the miniOrange metadata section mentioned in the previous step. |
| Audience URI (SP Entity ID) | Entity ID or Issuer copied from the miniOrange metadata section mentioned in the previous step. |
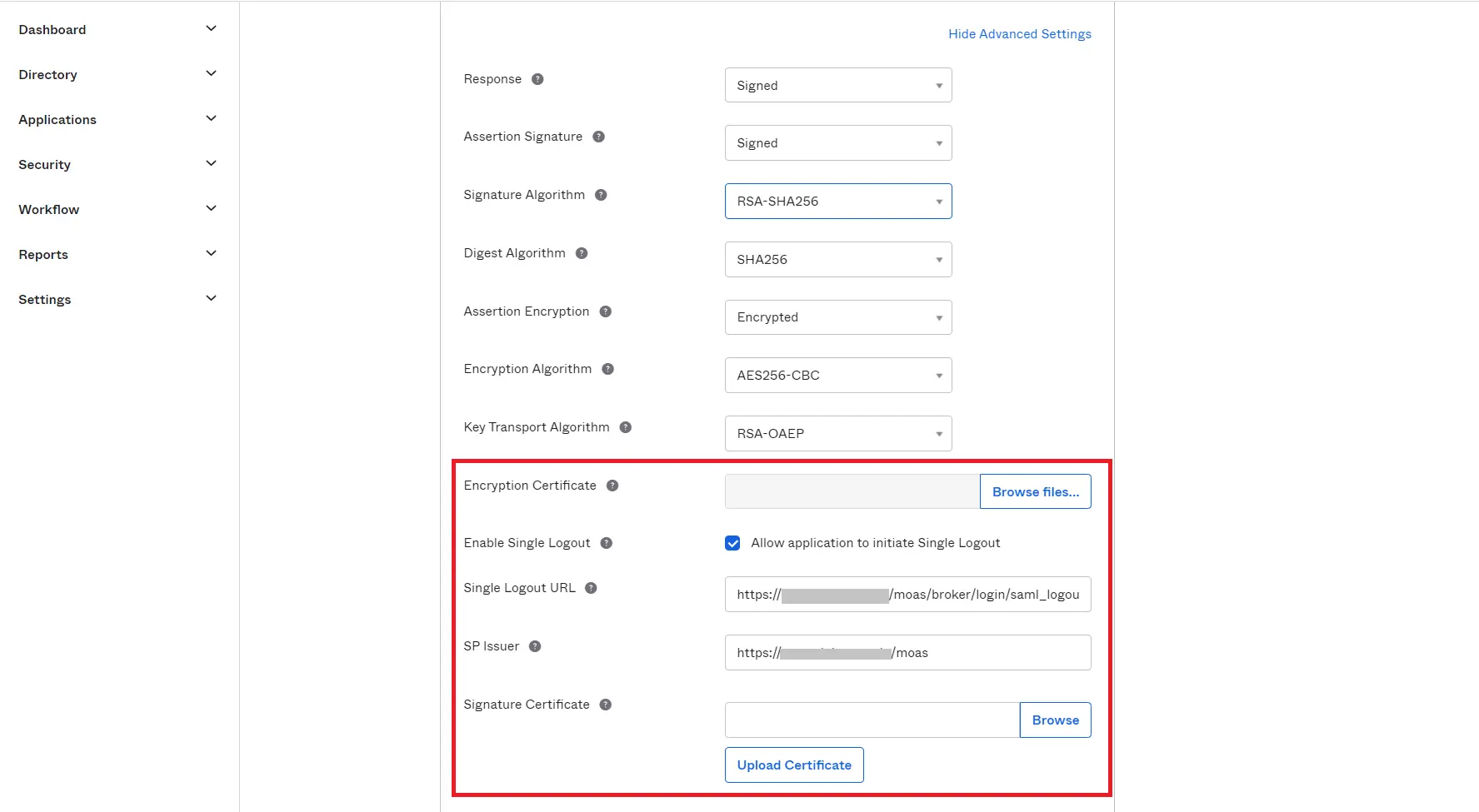
| Encryption Certificate | This is optional |
| Enable Single Logout | Enable the check box to Allow application to initiate Single Logout |
| Single Logout URL | Single Logout URL as mentioned in the Metadata Section |
| SP Issuer | Entity ID or Issuer as mentioned in the Metadata Section |
| Signature Certificate | X.509 Certificate can be downloaded from the Metadata Section |

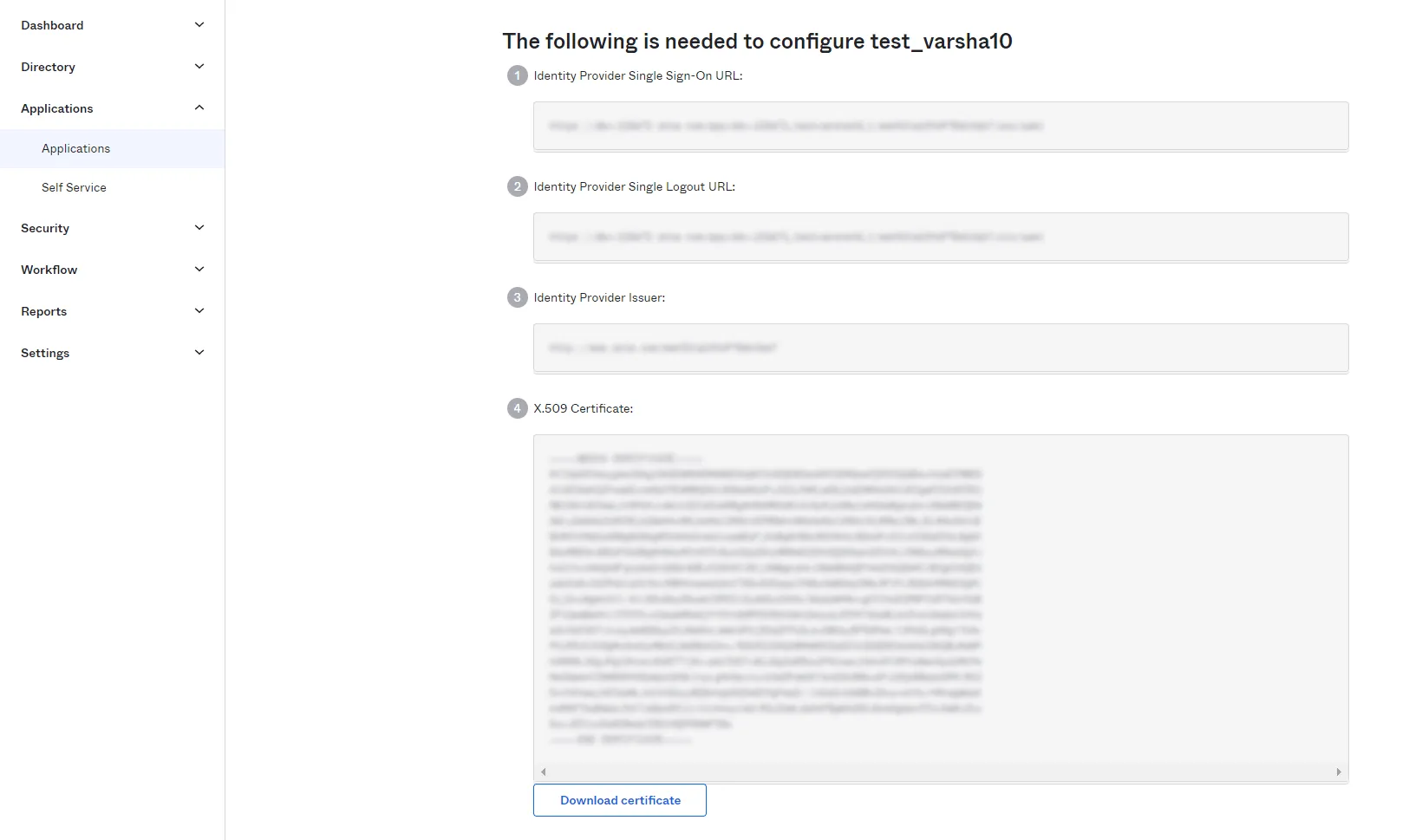
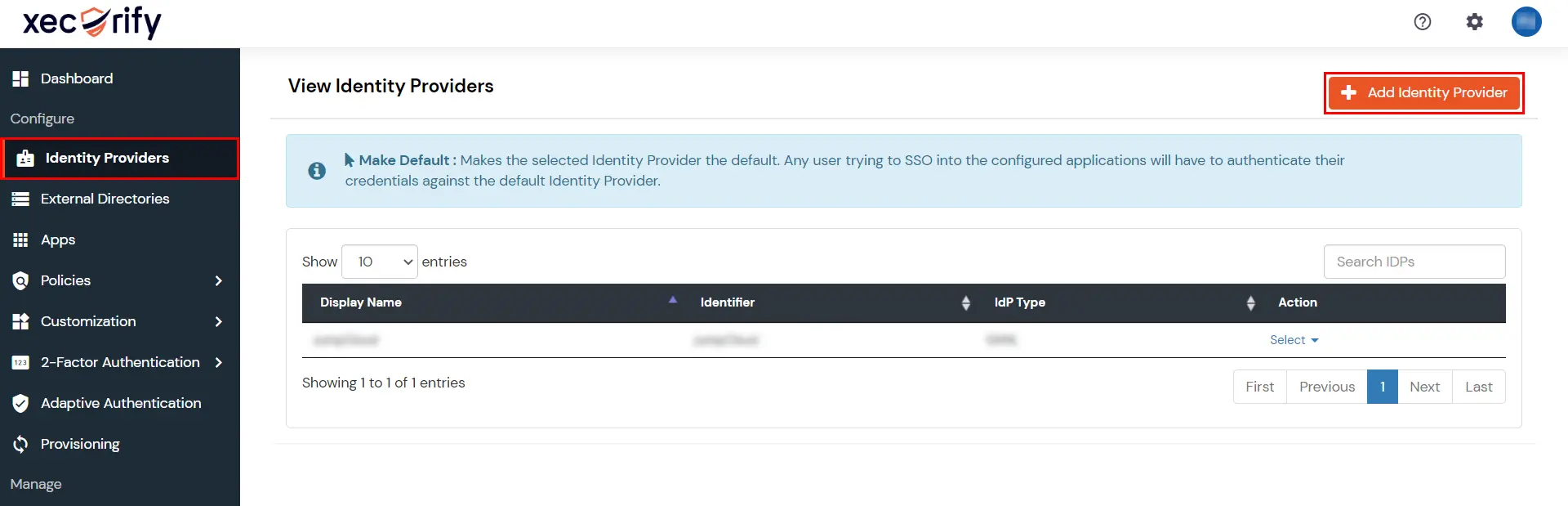
| IdP Entity ID | Identity Provider Issuer from Okta |
| SAML SSO Login URL | Identity Provider Single Sign-On URL from Okta |
| X.509 Certificate | X.509 Certificate from Okta |
| Single Logout URL [Optional] | Single Logout URL from Okta |
| Domain Mapping | Can be used to redirect specific domain user to specific IDP |
| Show IdP to Users | Enable this if you want to show this IDP to all users during Login |
| Send Configured Attributes | Enabling this would allow you to add attributes to be sent from IDP |
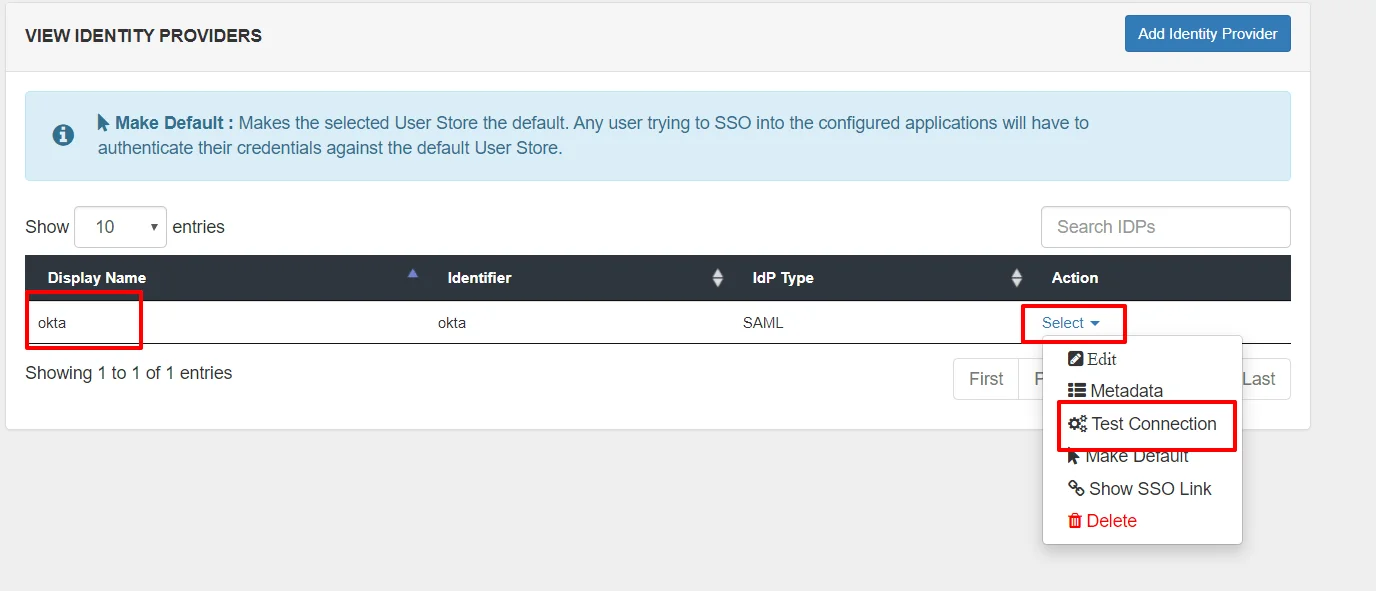
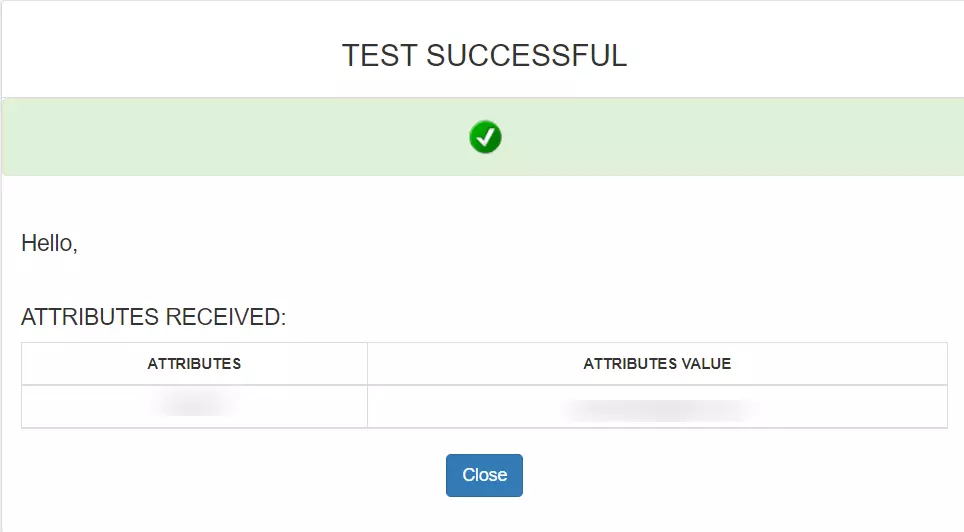
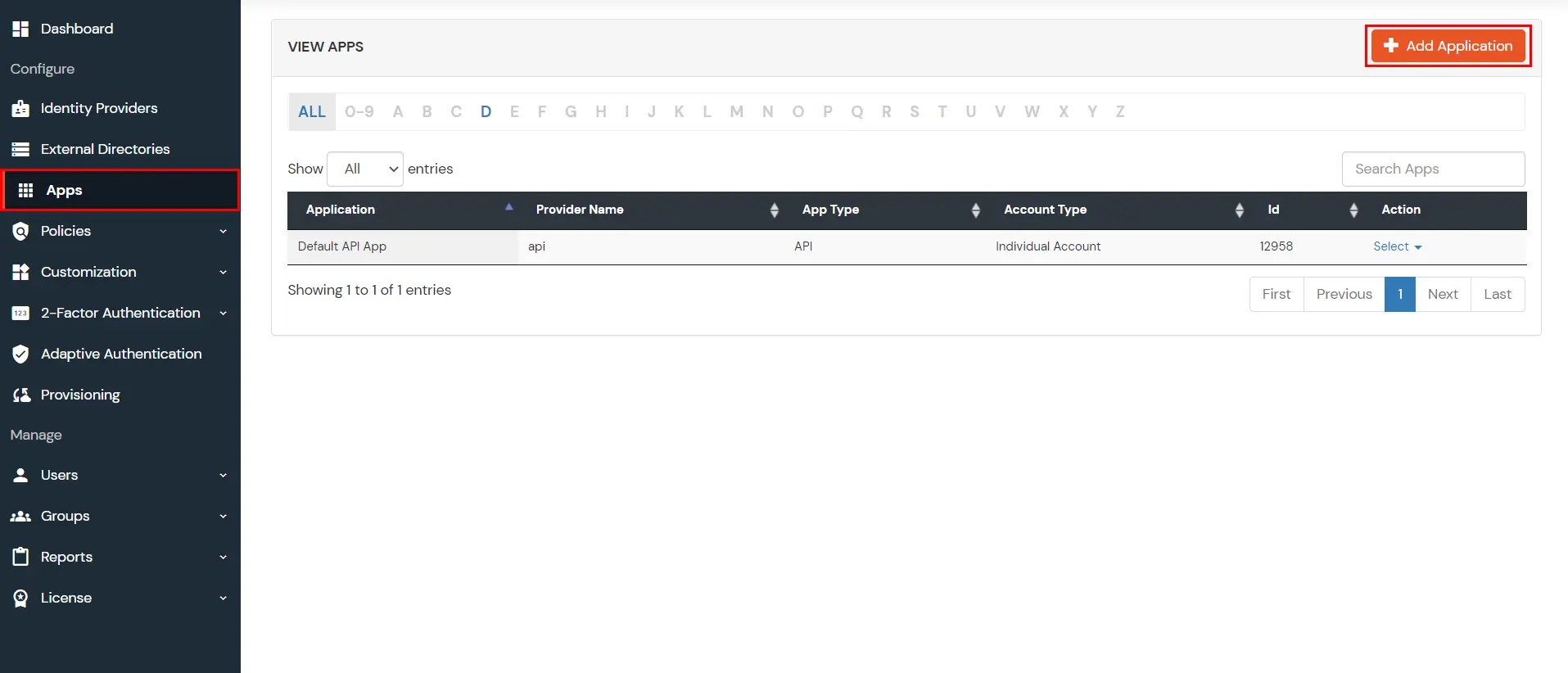
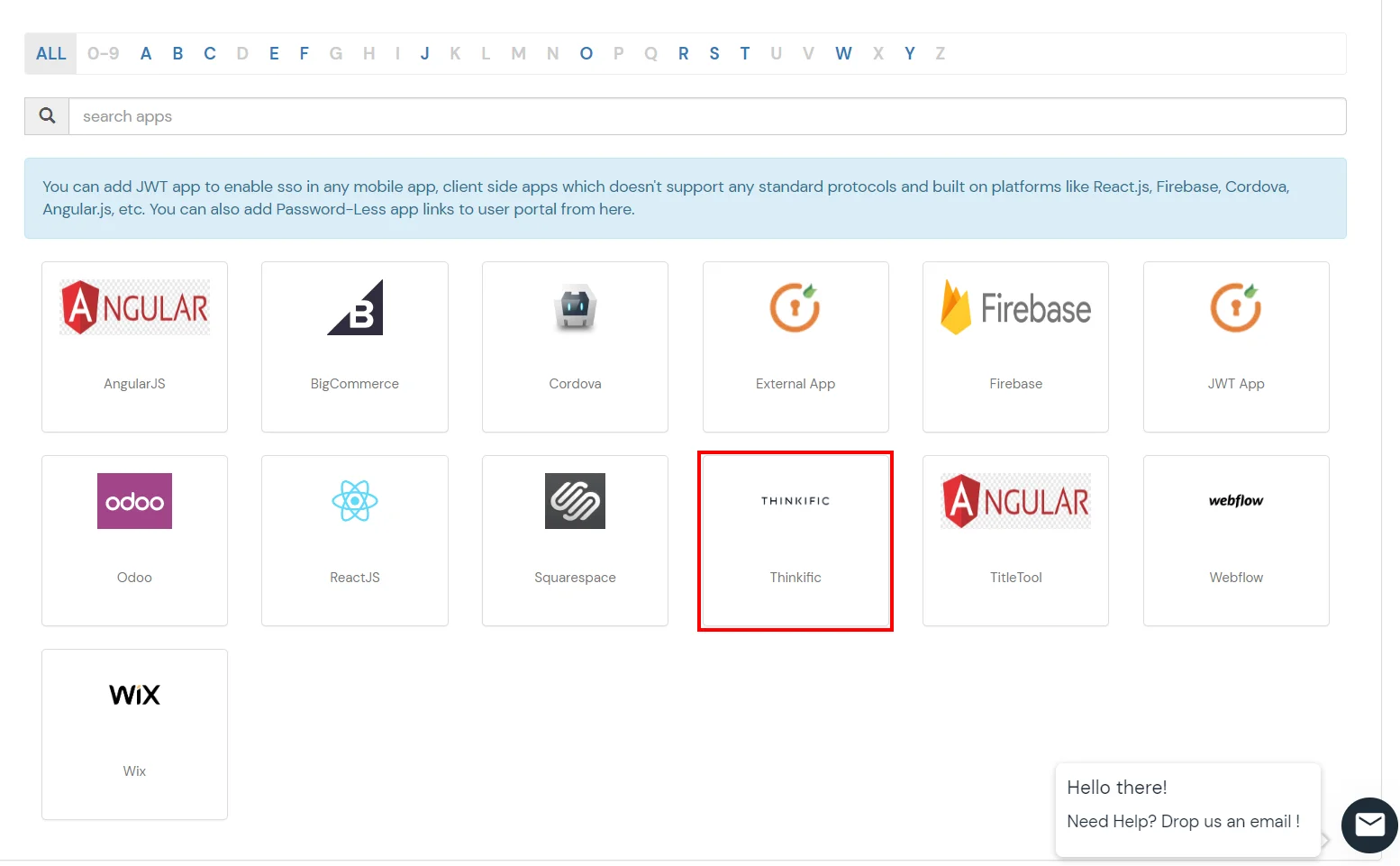
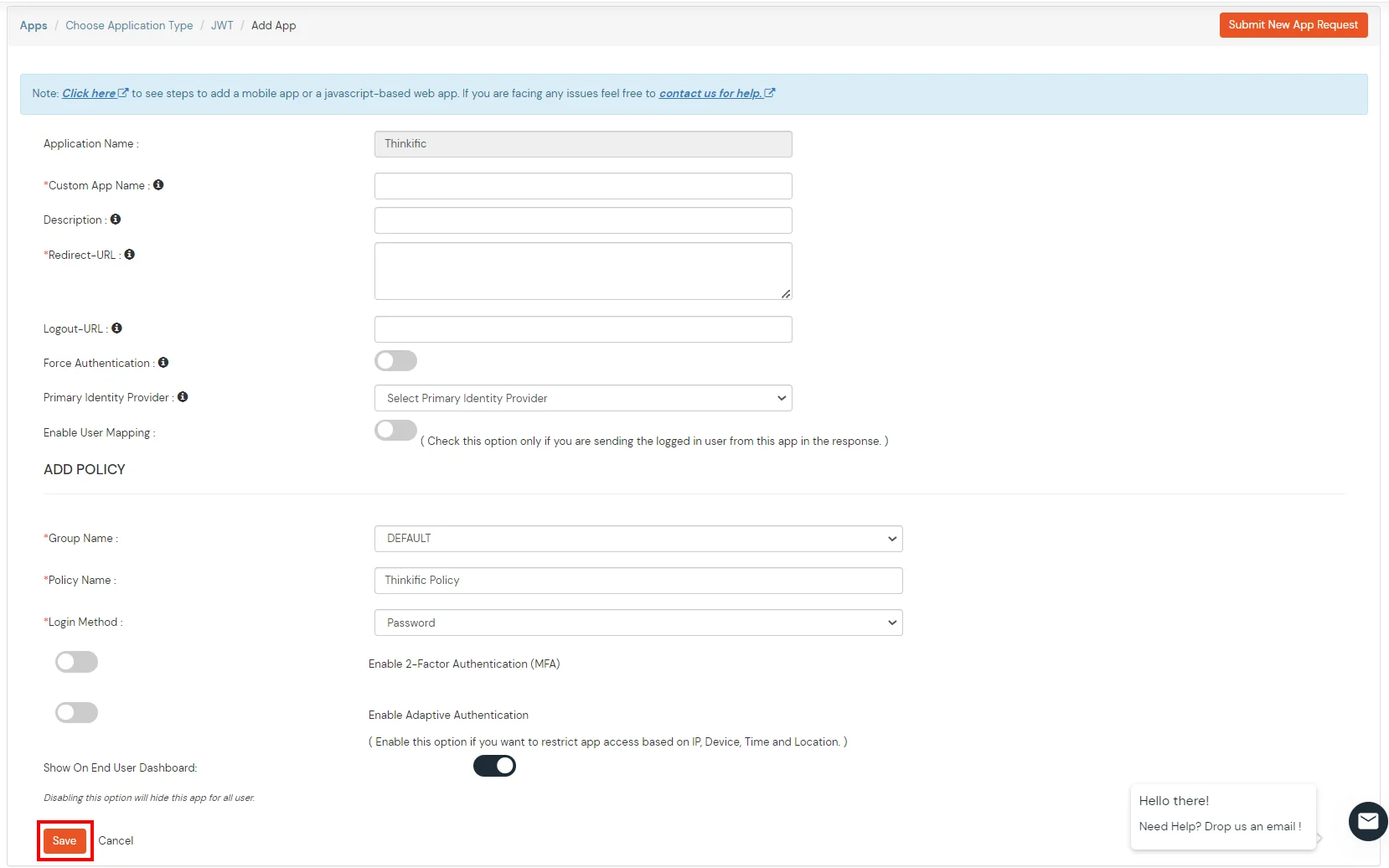
| Custom Application Name | Choose appropriate name according to your choice. |
|---|---|
| Description | Add appropriate description according to your choice. |
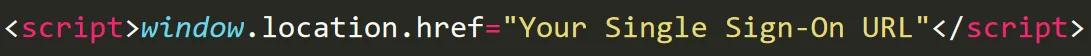
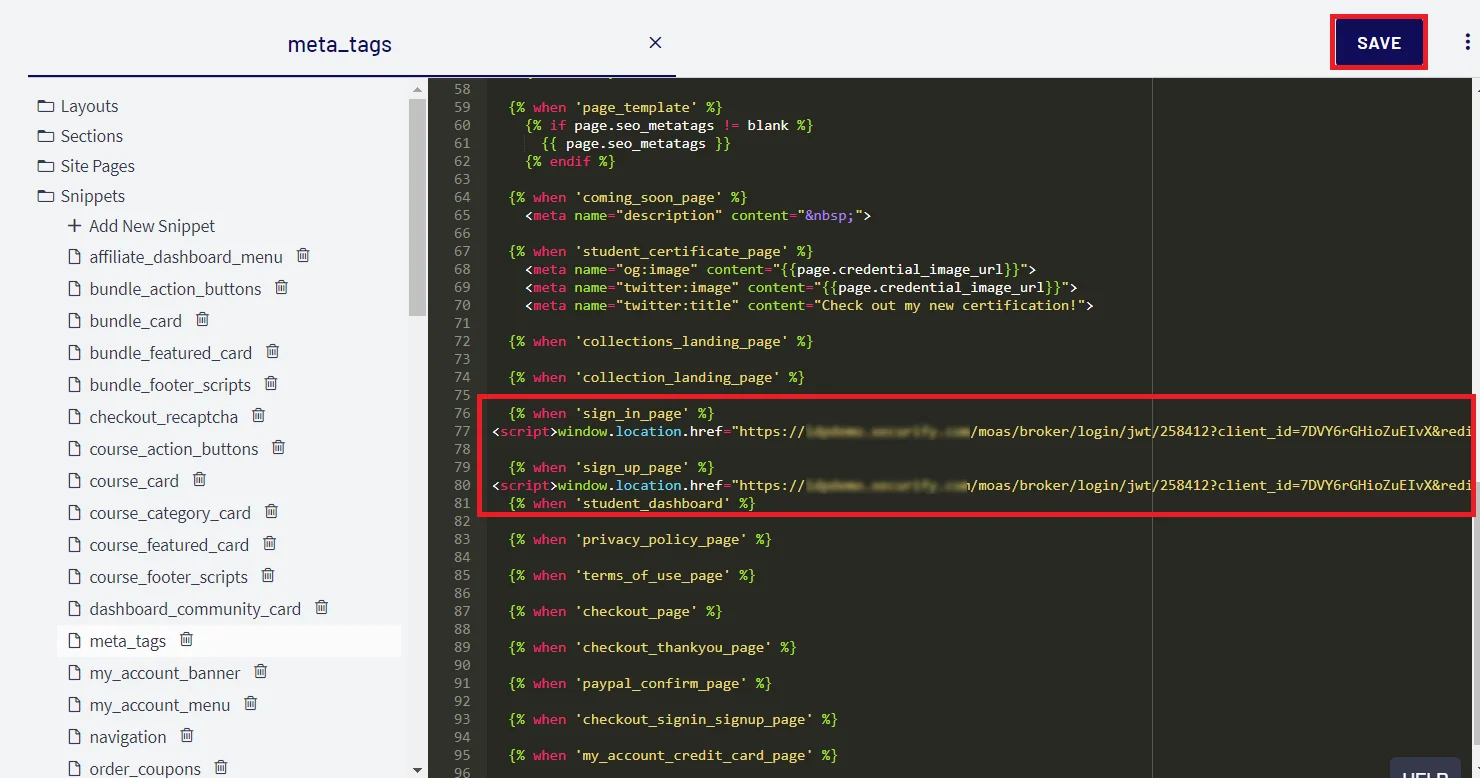
| Redirect-URL | https://{Subdomain}.thinkific.com/api/sso/v2/sso/jwt?jwt= |
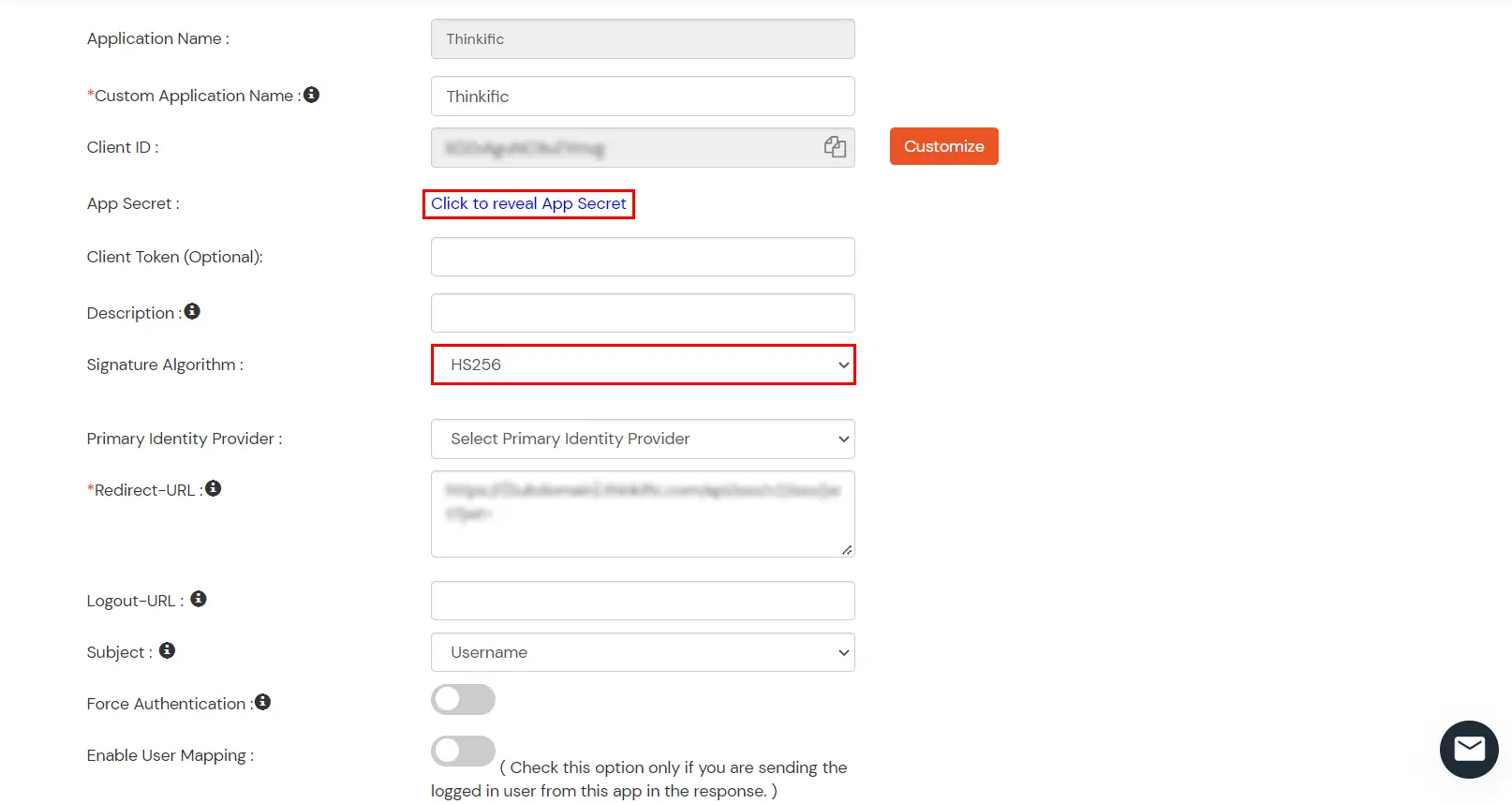
| App Secret | The API key fetched from Thinkific dashboard |
| Signature Algorithm | Choose HS256 |



Our Other Identity & Access Management Products